
Role Based Access Control Rbac Identity management techniques protect your sensitive digital assets. but what form should that protection take? knowing the difference between role based access control (rbac) vs. attribute based access control (abac) can help you make a smart decision. the main difference between rbac vs. abac is the way each method grants access. Learn how to implement role based access control (rbac) for your apis to enhance security and streamline access management.

Role Based Access Control Rbac Flow Chart Ppt Example You can use two broadly defined models to implement access control: role based access control (rbac) and attribute based access control (abac). each model has advantages and disadvantages, which are briefly discussed in this section. the model you should use depends on your specific use case. There are three main approaches: role based access control (rbac), attribute based access control (abac), and policy based access control (pbac). in this blog, we’ll break down the differences between these methods, explore their strengths and weaknesses, and show you how solutions like seamfix iam can help you implement the right approach. Role based access control (or rbac) is a security model that restricts system access based on the roles assigned to users within an org. it provides a way to manage user permissions by associating users with specific roles and granting access to resources on their basis. for e.g., in a whatsapp group chat, you have a normal user and an admin. Discover what attribute based access control (abac) is and how to go about implementing this with tokens for more robust api authorization.

Introducing Role Based Access Control Rbac Management Vrogue Co Role based access control (or rbac) is a security model that restricts system access based on the roles assigned to users within an org. it provides a way to manage user permissions by associating users with specific roles and granting access to resources on their basis. for e.g., in a whatsapp group chat, you have a normal user and an admin. Discover what attribute based access control (abac) is and how to go about implementing this with tokens for more robust api authorization. Role based access control (rbac) rbac is an access control model that assigns permissions based on predefined roles within an organization. users are granted access depending on their roles, which reflect their job functions or responsibilities. To support dynamic attributes, particularly in large organizations, a “role explosion” can result in thousands of separate roles being fashioned for different collections of permissions. recent interest in attribute based access control (abac) suggests that attributes and rules could either replace rbac or make it more simple and flexible.
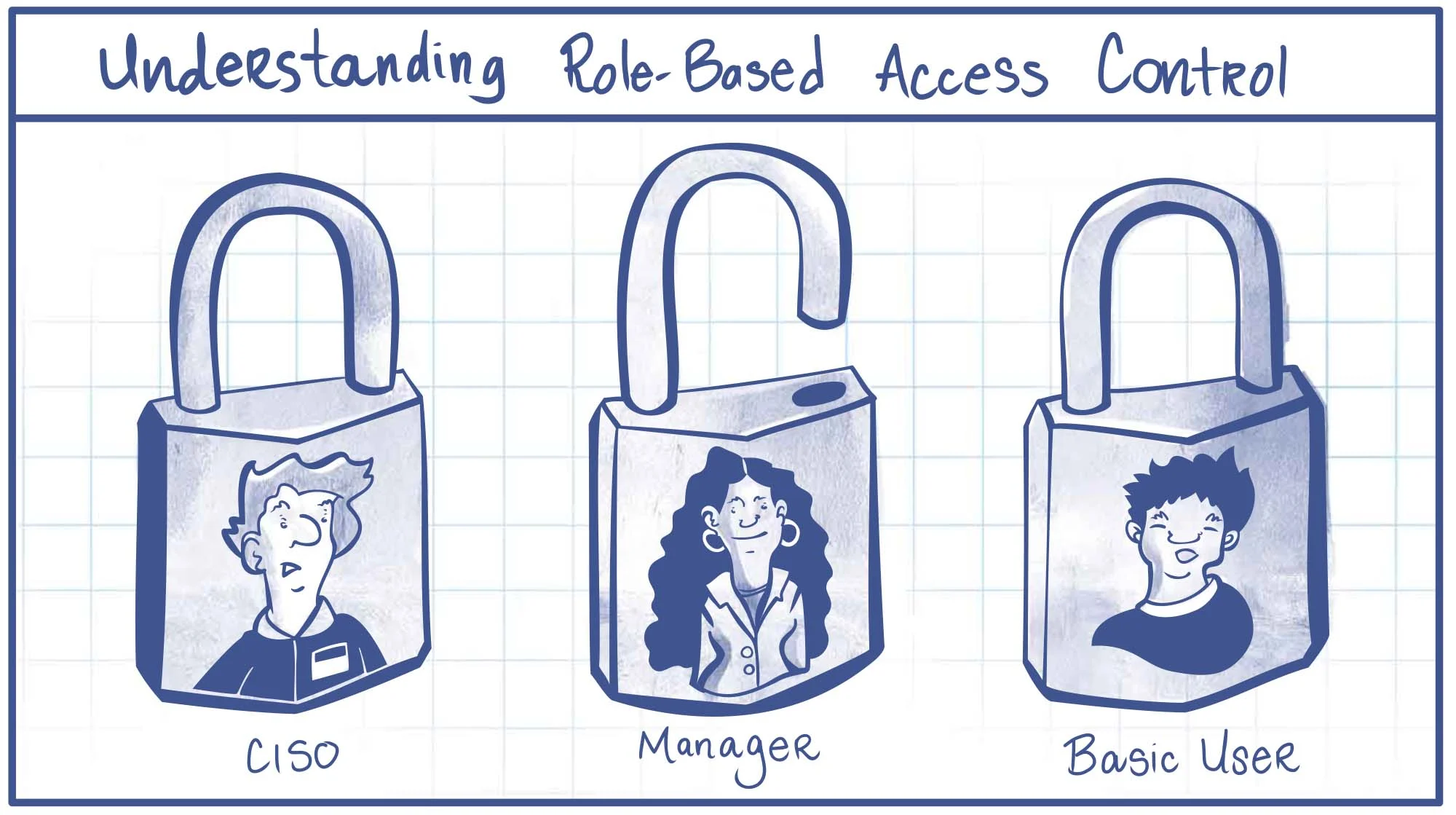
Rbac Role Based Access Control In Sailpoint Infosectr Vrogue Co Role based access control (rbac) rbac is an access control model that assigns permissions based on predefined roles within an organization. users are granted access depending on their roles, which reflect their job functions or responsibilities. To support dynamic attributes, particularly in large organizations, a “role explosion” can result in thousands of separate roles being fashioned for different collections of permissions. recent interest in attribute based access control (abac) suggests that attributes and rules could either replace rbac or make it more simple and flexible.
Lightrun Bolsters Security Measures With Role Based Access Control