
Josh Stroschein On Linkedin Malware Mondays Episode 01 Identifying Here it is, the inaugural episode of malware mondays! this series will provide a malicious artifact for you to analyze on mondays, and a follow on live stream on friday to review that artifact. 🚨 prepping for another malware mondays next week! until then, you can get caught up with previous live streams! ep. 01 process monitor lnkd.in gc9ujkvi ep. 02 process explorer.

Identifying Malicious Activity On A Computer System Platinum Technologies Sharpen your skills with real world challenges! dive into hands on exercises released monday's featuring a specific malware artifact or data capture. learn new tools and tactics by tackling these practical challenges. level up your learning with a live stream review every friday, breaking down the challenges and solutions. Here it is, the inaugural malware monday episode 01 analyzing amadey activity with procmon. this video is a behind the scenes look at how i captured the artifacts. 🔴 malware mondays episode 01 identifying malicious activity in process monitor (procmon) data 20 2 comments 3w. \want to learn how to identify malicious activity with procmon?? learn from a phd in cyber ops. live right now (and likely on replay) josh stroschein is….

Malware Mondays The Cyber Yeti 🔴 malware mondays episode 01 identifying malicious activity in process monitor (procmon) data 20 2 comments 3w. \want to learn how to identify malicious activity with procmon?? learn from a phd in cyber ops. live right now (and likely on replay) josh stroschein is…. Repository containing malware analysis filters for the windows sysinternals' process monitor tool nasbench procmon malware analysis filters. Before you run the riomalware.dll, you need to have the procmon be ready by clicking the capture button. when the procmon is in capturing mode then you can run the malware sample. in the malware code, we found the first step is basically will write a file. but let us assume we don’t know the path and how big it is. we can filter out the events gathered by the procmon by using the filtering.

7 Identifying Malicious Activity Docx 7 1 Identifying Malicious Repository containing malware analysis filters for the windows sysinternals' process monitor tool nasbench procmon malware analysis filters. Before you run the riomalware.dll, you need to have the procmon be ready by clicking the capture button. when the procmon is in capturing mode then you can run the malware sample. in the malware code, we found the first step is basically will write a file. but let us assume we don’t know the path and how big it is. we can filter out the events gathered by the procmon by using the filtering.

Trace Syscall Activity In Linux With Process Monitor Procmon Ostechnix
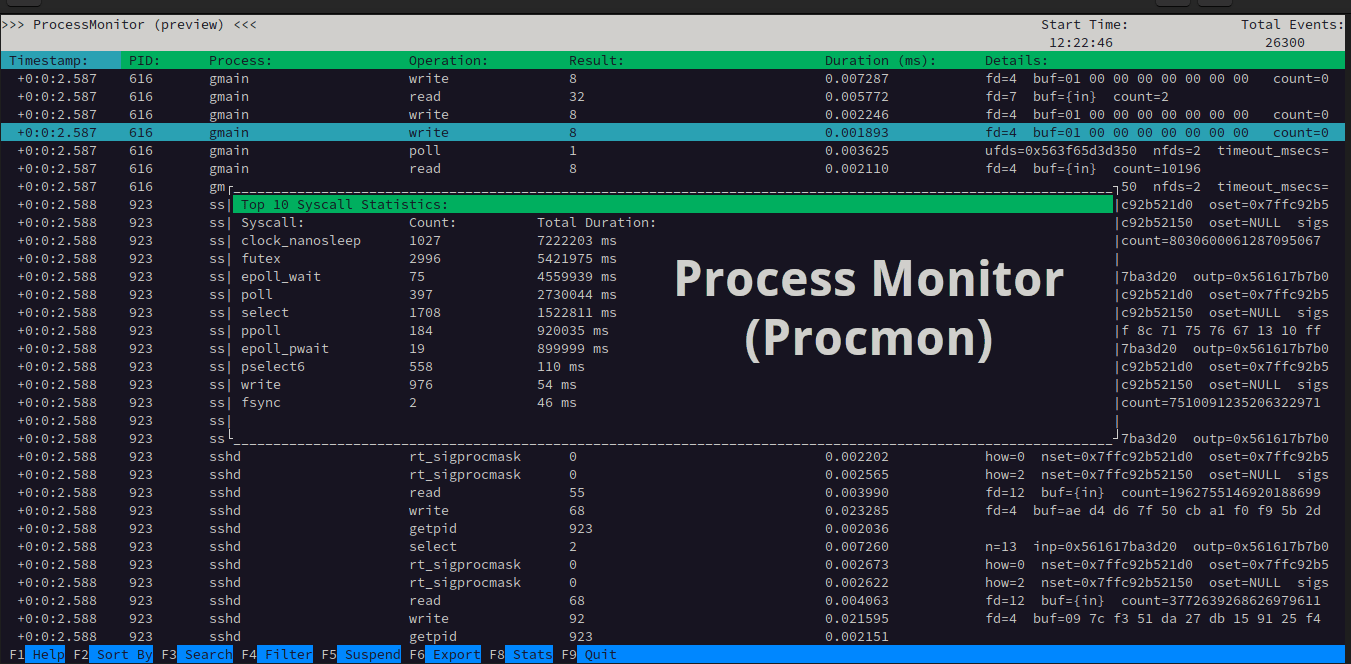
Trace Syscall Activity In Linux With Process Monitor Procmon Ostechnix
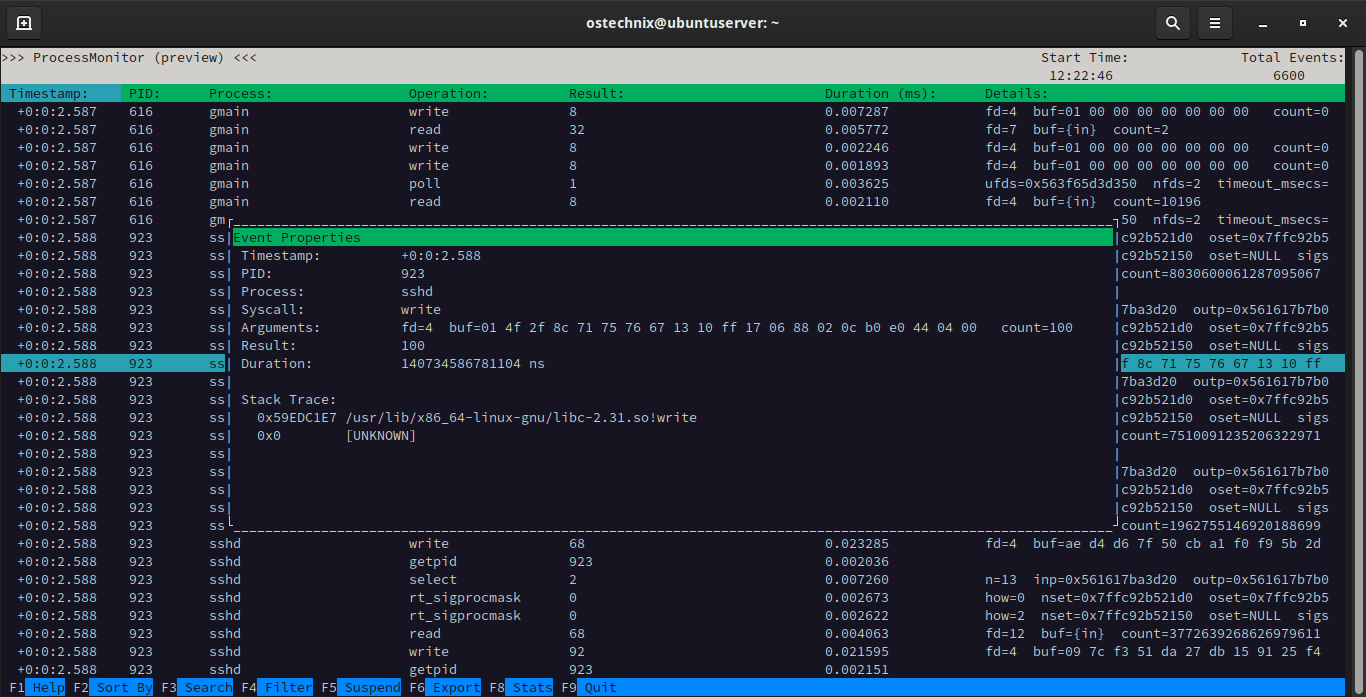
Trace Syscall Activity In Linux With Process Monitor Procmon Ostechnix