
M 3 Cryptographic Hash Functions Pdf Public Key Cryptography Lecture 21: cryptography: hashing in this lecture, we will be studying some basics of cryptography. specifically, we will be covering hash functions. Cryptographic hash functions are mathematical algorithms that transform input data into a fixed length sequence of characters, referred to as a hash value. cryptographic hash functions are intended to be fast, deterministic, and one way, meaning that even a minor change in input yields a very different hash. these functions are important for securing information digitally by allowing data.

Unit 4 Cryptographic Hash Functions And Digital Signature Pdf 21. cryptography: hash functions mit opencourseware 5.68m subscribers subscribed. A cryptographic hash function (chf) is a hash algorithm (a map of an arbitrary binary string to a binary string with a fixed size of bits) that has special properties desirable for a cryptographic application: [1] the probability of a particular n {\displaystyle n} bit output result (hash value) for a random input string ("message") is 2 − n {\displaystyle 2^ { n}} (as for any good hash. In cryptography, hash functions transform input data of arbitrary size (e.g. a text message) to a result of fixed size (e.g. 256 bits), which is called hash value (or hash code, message digest, or simply hash). hash functions (hashing algorithms) used in computer cryptography are known as " cryptographic hash functions ". examples of such functions are sha 256 and sha3 256, which transform. Learn about cryptography hash functions, their properties, and applications in data integrity and security. explore types of hash functions and their significance in cryptography.
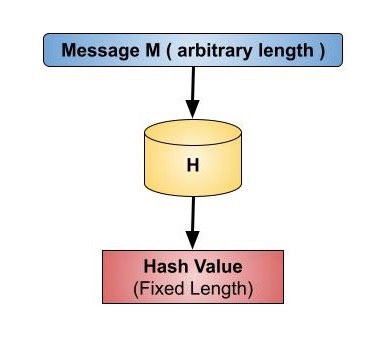
Cryptography Hash Functions In cryptography, hash functions transform input data of arbitrary size (e.g. a text message) to a result of fixed size (e.g. 256 bits), which is called hash value (or hash code, message digest, or simply hash). hash functions (hashing algorithms) used in computer cryptography are known as " cryptographic hash functions ". examples of such functions are sha 256 and sha3 256, which transform. Learn about cryptography hash functions, their properties, and applications in data integrity and security. explore types of hash functions and their significance in cryptography. Cs 312 lecture 21 hash functions hash functions hash tables are one of the most useful data structures ever invented. unfortunately, they are also one of the most misused. code built using hash tables often falls far short of achievable performance. there are two reasons for this: clients choose poor hash functions that do not act like random number generators, invalidating the simple uniform. Cryptographic hash functions a cryptographic hash function has the same properties as ordinary hash functions: it is easy to compute, takes an arbitrarily long input string (or file), and it produces a random looking, fixed length, output string. for example, the most common hash function used today, sha2 256, outputs 256 bits (32 bytes), no matter the length of the input.

Ch11 Cryptographic Hash Functions مختصر Pdf Cs 312 lecture 21 hash functions hash functions hash tables are one of the most useful data structures ever invented. unfortunately, they are also one of the most misused. code built using hash tables often falls far short of achievable performance. there are two reasons for this: clients choose poor hash functions that do not act like random number generators, invalidating the simple uniform. Cryptographic hash functions a cryptographic hash function has the same properties as ordinary hash functions: it is easy to compute, takes an arbitrarily long input string (or file), and it produces a random looking, fixed length, output string. for example, the most common hash function used today, sha2 256, outputs 256 bits (32 bytes), no matter the length of the input.

Understanding Cryptography Hash Functions Explained