
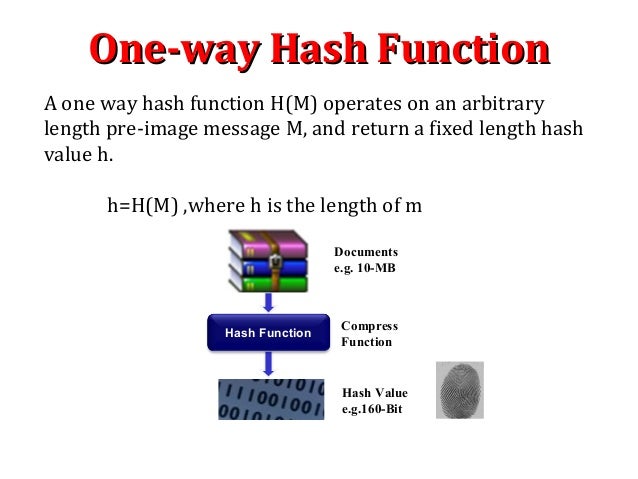
What Is Hashing Hashing allows for faster search and dynamic operations on data structures, arrays, and sorted arrays. this lecture discusses comparison models, decision trees, and hash functions. Hashing refers to the process of generating a small sized output (that can be used as index in a table) from an input of typically large and variable size. hashing uses mathematical formulas known as hash functions to do the transformation. this technique determines an index or location for the storage of an item in a data structure called hash table. introduction to hashing hash table data.

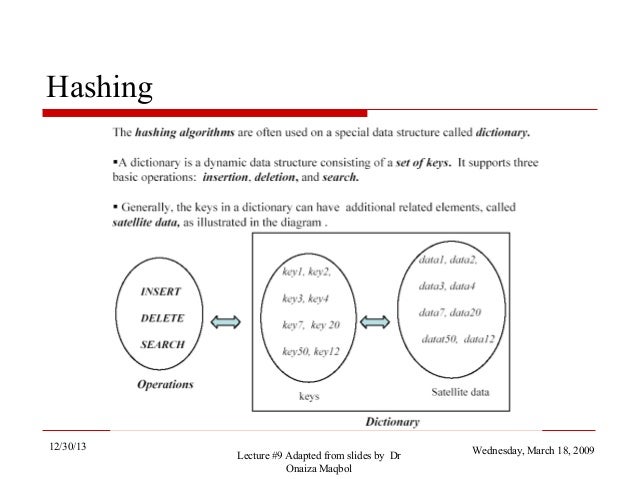
Hashing Techniques Interviewbit Hashing allows for faster search and dynamic operations on data structures, arrays, and sorted arrays. this lecture discusses comparison models, decision trees, and hash functions. Hash collision some hash functions are prone to too many hash collisions for instance, you’re hashing pointers of int64 t, using modular hashing h = with = 2 buckets completely empty for some d is going to leave many. 4. hashing hashing is a technique that is frequently used in implementing efficient algorithms. in python, the data structures set and dict (dictionary) are based on hashing. in this chapter, we take a look at data structures based on hashing and their use in algorithm design. we will also cover some theory underlying the data structures. set the python data structure set, based on hashing. 4.2 insertion to insert an element k, the algorithm hashes it with the first table’s hash function, placing it in the hash table’s index. however, if there was something in that slot before, that value is stored, hashed with the second table’s hash function, and stored in that hash table’s index instead. and again, if there was something in that index already, it will be stored, hashed.

What Is Hashing In Cybersecurity Coursera 4. hashing hashing is a technique that is frequently used in implementing efficient algorithms. in python, the data structures set and dict (dictionary) are based on hashing. in this chapter, we take a look at data structures based on hashing and their use in algorithm design. we will also cover some theory underlying the data structures. set the python data structure set, based on hashing. 4.2 insertion to insert an element k, the algorithm hashes it with the first table’s hash function, placing it in the hash table’s index. however, if there was something in that slot before, that value is stored, hashed with the second table’s hash function, and stored in that hash table’s index instead. and again, if there was something in that index already, it will be stored, hashed. Learn about hashing data structures, their implementation, and applications in computer science. explore key concepts and examples to enhance your understanding. 21.1.6 lab – hashing things out (instructor version) instructor note: red font color or gray highlights indicate text that appears in the instructor copy only. objectives part 1: hashing a text file with openssl part 2: verifying hashes background scenario hash functions are mathematical algorithms designed to take data as input and generate a fixed size, unique string of characters, also.
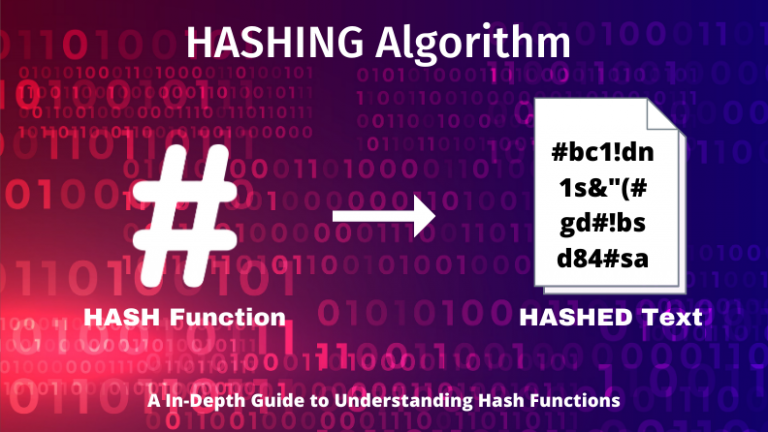
Read The Hashing Algorithms And Hash Functions Appsealing Learn about hashing data structures, their implementation, and applications in computer science. explore key concepts and examples to enhance your understanding. 21.1.6 lab – hashing things out (instructor version) instructor note: red font color or gray highlights indicate text that appears in the instructor copy only. objectives part 1: hashing a text file with openssl part 2: verifying hashes background scenario hash functions are mathematical algorithms designed to take data as input and generate a fixed size, unique string of characters, also.
Hashing
Hashing