
Api Security Checklist Pdf This document provides a checklist for securing apis according to the owasp top 10 security risks. it outlines best practices for object level authorization, broken authentication, excessive data exposure, lack of resources rate limiting, broken functional level authorization, mass assignment, security misconfiguration, injection, improper asset management, and insufficient logging. Check all possible ways to authenticate to all apis password reset apis and one time links also allow users to get authenticated and should be protected just as seriously use standard authentication, token generation, password storage, multi factor authentication use short lived access tokens authenticate your apps (so you know who is talking.

Account Security Checklist Download Free Pdf Password Security 3. authentication and password management: ges and resources, except those specifically intended to be public zed implementation for all authentication controls, including libraries that call external authentication services the centralized authentication control all authentication controls should fail securely. In this article, we provide a checklist that examines the essential api security measures to protect yourself from data breaches and other cyber threats. Https secure rest services must only provide https endpoints. this protects authentication credentials in transit, for example passwords, api keys or json web tokens. it also allows clients to authenticate the service and guarantees integrity of the transmitted data. see the transport layer security cheat sheet for additional information. Authentication don't use basic auth. use standard authentication instead (e.g., jwt). don't reinvent the wheel in authentication, token generation, password storage. use the standards. use max retry and jail features in login. use encryption on all sensitive data.

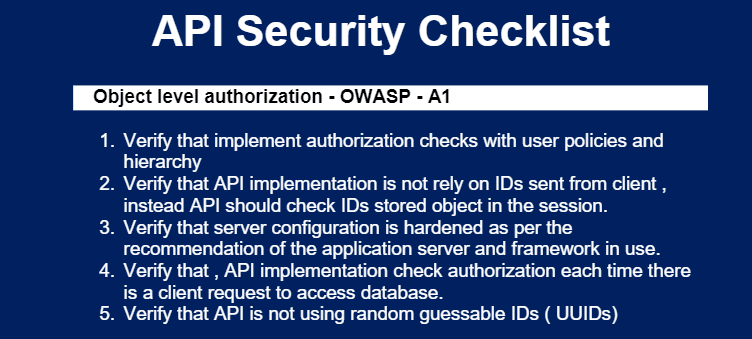
Api Security Checklist Ciso2ciso Com Cyber Security Group Verify password reset apis and one time links also allow users to get authenticated and should be strictly protected. token generation, password storage and mult verify , api uses short lived access token. verify that , api uses stricter rate limiting for authentication , implement lockout polices and weak password checks. Review access control check for authentication on every api point.
Disc Infosec Blogapi Security Checklist Disc Infosec Blog

The Ultimate Api Security Checklist Nordic Apis