
Applied Cryptography Tutorial Computer Engineering Studocu Tutorial cse 654 session 2o2i1e abubakar tafawa balewa university, bauchi department of mathematical sciences first semester examinations session m.sc cyber. A collection of awesome software, learning tutorials, theoretical resources, books and videos, best practices in applied cryptography. thanks to all contributors, you're awesome and wouldn't be possible without you!.

Chapter 2 Cryptography Cryptography Chapter 2 Amol D Vibhute Phd In this cryptography tutorial, we've covered basics and advanced concepts of cryptography including symmetric key cryptography, asymmetric key cryptography as well as cryptanalysis, public key cryptography and more. it provides a solid foundation in the core concepts of cryptography, as well as insights into its practical applications. Studocu provides a comprehensive help center with resources and support for students and educators. Nice notes applied cryptography department of cyber security lecture notes on applied cryptography tech semester prepared mrs. c.gazala akhtar asst.professor. This repository is dedicated to providing detailed and well organized lecture notes for the "cryptography and network security" course. each lecture note is designed to help students understand fundamental concepts and practical implementations essential for understanding a particular topic.
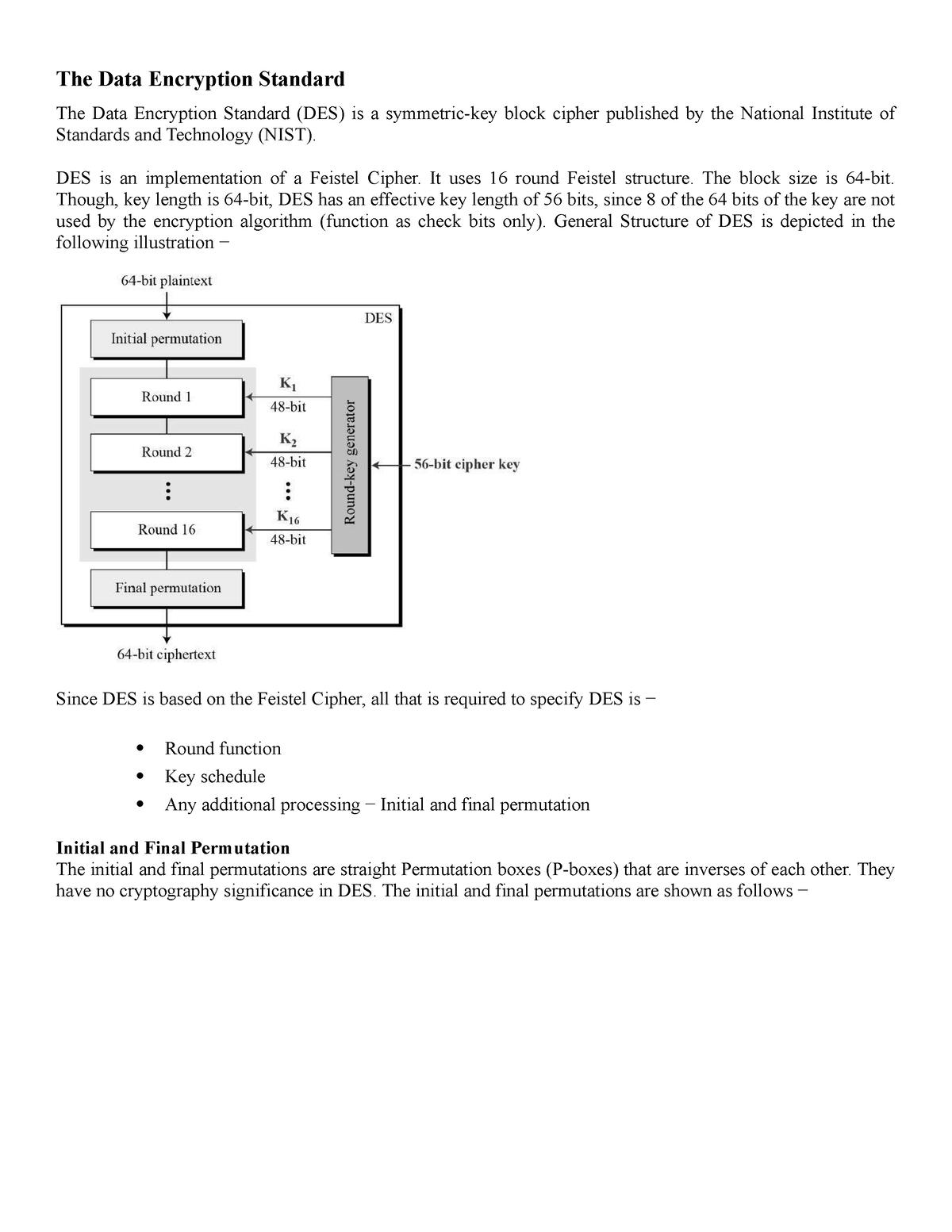
Cryptography To Study The Data Encryption Standard The Data Nice notes applied cryptography department of cyber security lecture notes on applied cryptography tech semester prepared mrs. c.gazala akhtar asst.professor. This repository is dedicated to providing detailed and well organized lecture notes for the "cryptography and network security" course. each lecture note is designed to help students understand fundamental concepts and practical implementations essential for understanding a particular topic. The aim: this cryptography course in computer science and engineering aims to develop your ability to understand how cryptographic algorithms work, to identify the problems associated with the application of cryptography in real world scenarios, and explain the operation of various cryptographic mechanisms. For those who want a more current book, i recommend cryptography engineering, which i wrote in 2010 with niels ferguson and tadayoshi kohno. but for a review of those heady times of the mid 1990s, and an introduction to what has become an essential tech nology of the internet, applied cryptography still holds up surprisingly well.

Cryptography And Network Security Easy Notes Bachelor Of Computer The aim: this cryptography course in computer science and engineering aims to develop your ability to understand how cryptographic algorithms work, to identify the problems associated with the application of cryptography in real world scenarios, and explain the operation of various cryptographic mechanisms. For those who want a more current book, i recommend cryptography engineering, which i wrote in 2010 with niels ferguson and tadayoshi kohno. but for a review of those heady times of the mid 1990s, and an introduction to what has become an essential tech nology of the internet, applied cryptography still holds up surprisingly well.