
Oauth 2 0 Microservices Authentication Authorisation Stack Overflow In microservices, ensuring data security is paramount. authentication and authorization are two crucial components of this security framework. this article provides a straightforward overview of how authentication verifies user identity and how authorization controls access to resources within microservices. This article is the second in a series of articles about authentication and authorization in a microservice architecture. the complete series is: overview of authentication and authorization in a microservice architecture implementing authentication implementing jwt based authorization developing complex authorization implementing complex authorization using oso cloud part 1 implementing.
Github Imfelipedev Microservice Authentication Simple Authentication How #jwt is used for #authentication in #microservices system? authentication & authorisation in microservices short 1k dislike. An auth microservice is a centralized authority that grants authentication and authorization (auth for short) to a user to allow her him access to a resource provided by other systems (i.e. other microservices) that trust said authority. In microservices architectures, user authentication and authorization play pivotal roles, often leveraging a range of technologies. this article focuses on a best practice model grounded in jwt. Streamline authentication and authorization in microservices using api gateway and practical methods for seamless microservice communication.
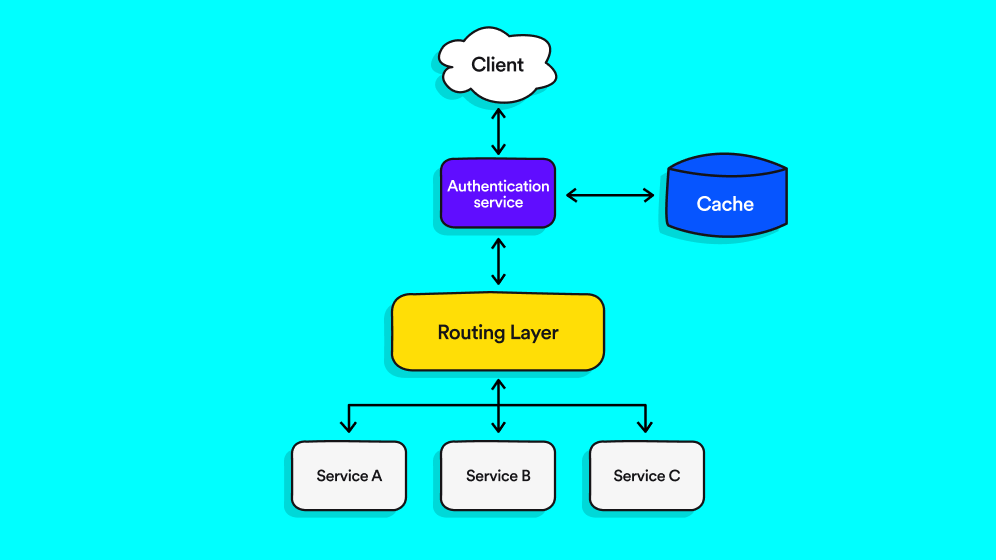
Authentication With Microservices Lusha Engineering Blog In microservices architectures, user authentication and authorization play pivotal roles, often leveraging a range of technologies. this article focuses on a best practice model grounded in jwt. Streamline authentication and authorization in microservices using api gateway and practical methods for seamless microservice communication. What's the difference between authentication and authorization in microservices? authentication in microservices is about confirming a user's or service's identity using credentials like passwords or tokens. For example, while authentication confirms an employee’s identity, authorization determines whether he or she has access to certain corporate data. leveraging openid connect and oauth2 for centralized security in the distributed ecosystem of microservices, traditional security methods fall short.

Rest Microservices Authentication Stack Overflow What's the difference between authentication and authorization in microservices? authentication in microservices is about confirming a user's or service's identity using credentials like passwords or tokens. For example, while authentication confirms an employee’s identity, authorization determines whether he or she has access to certain corporate data. leveraging openid connect and oauth2 for centralized security in the distributed ecosystem of microservices, traditional security methods fall short.
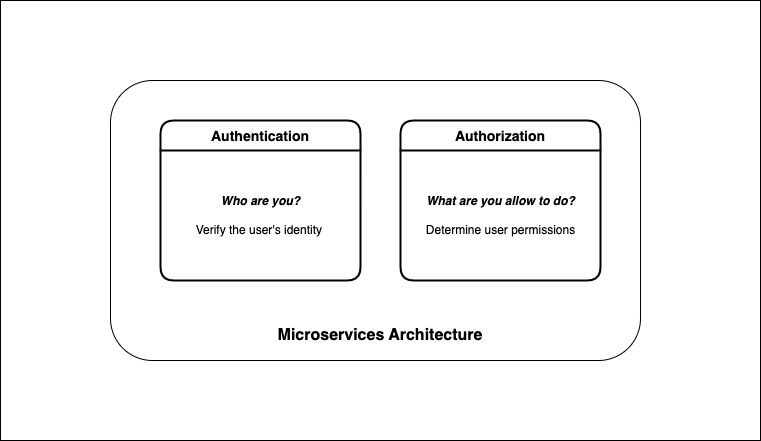
Microservices Architecture Authentication And Authorization

Authentication And Authorization In Microservices