
Confluent Cloud Security Controls Pdf Cloud Computing Computer Setting acls is important – if a resource does not have associated acls, only super users can access the resource. to learn more about authorization using acls, see authorization module of the free confluent developer course, apache kafka security. Understand how to use role based access controls (rbac) and access control lists (acls) to provide important authorization controls for your enterprise's kafka cluster data.

Kafka Authorization Using Rbac And Acls In Confluent Cloud Authorization | rbac and acls | confluent cloud security confluent 87.3k subscribers 6.6k views 2 years ago #kafka #cloudsecurity #cloudnative. Security is a primary consideration for any system design. for a kafka deployment to be production ready, it needs to be configured with security features such as authentication, authorization, encryption, etc. this article will helps you enable rbac authorization feature for confluent kafka using metadata service. Confluent cloud cause client applications may return errors like topicauthorizationfailederror, topic authorization failed when producing or consuming to a topic in confluent cloud. typically, the issue arises from insufficient permissions. reference: role based access control (rbac) on confluent cloud use access control lists (acls) on. Use role based access control (rbac) for authorization in confluent platform role based access control (rbac) is a method for controlling system access based on roles assigned to users within an organization. rbac is defined around predefined roles and the privileges associated with those roles (also known as role bindings).

Kafka Authorization Using Rbac And Acls In Confluent Cloud Confluent cloud cause client applications may return errors like topicauthorizationfailederror, topic authorization failed when producing or consuming to a topic in confluent cloud. typically, the issue arises from insufficient permissions. reference: role based access control (rbac) on confluent cloud use access control lists (acls) on. Use role based access control (rbac) for authorization in confluent platform role based access control (rbac) is a method for controlling system access based on roles assigned to users within an organization. rbac is defined around predefined roles and the privileges associated with those roles (also known as role bindings). Confluent provides saml sso so you can utilize your preferred identity provider to authenticate user logins to confluent cloud. you have granular access control across your cloud kafka deployment through service accounts and access control lists (acls) in order to gate application access to critical kafka resources like topics and consumer groups. We will review the documentation to make this clearer. one point of clarification in the question: we’d recommend using a service account, and api keys (with acls potentially specified) represent the service account. so, whether using acls or rbac, the authorization settings are associated with the service account identity in either case.

Kafka Authorization Using Rbac And Acls In Confluent Cloud Confluent provides saml sso so you can utilize your preferred identity provider to authenticate user logins to confluent cloud. you have granular access control across your cloud kafka deployment through service accounts and access control lists (acls) in order to gate application access to critical kafka resources like topics and consumer groups. We will review the documentation to make this clearer. one point of clarification in the question: we’d recommend using a service account, and api keys (with acls potentially specified) represent the service account. so, whether using acls or rbac, the authorization settings are associated with the service account identity in either case.

Kafka Authorization Using Rbac And Acls In Confluent Cloud
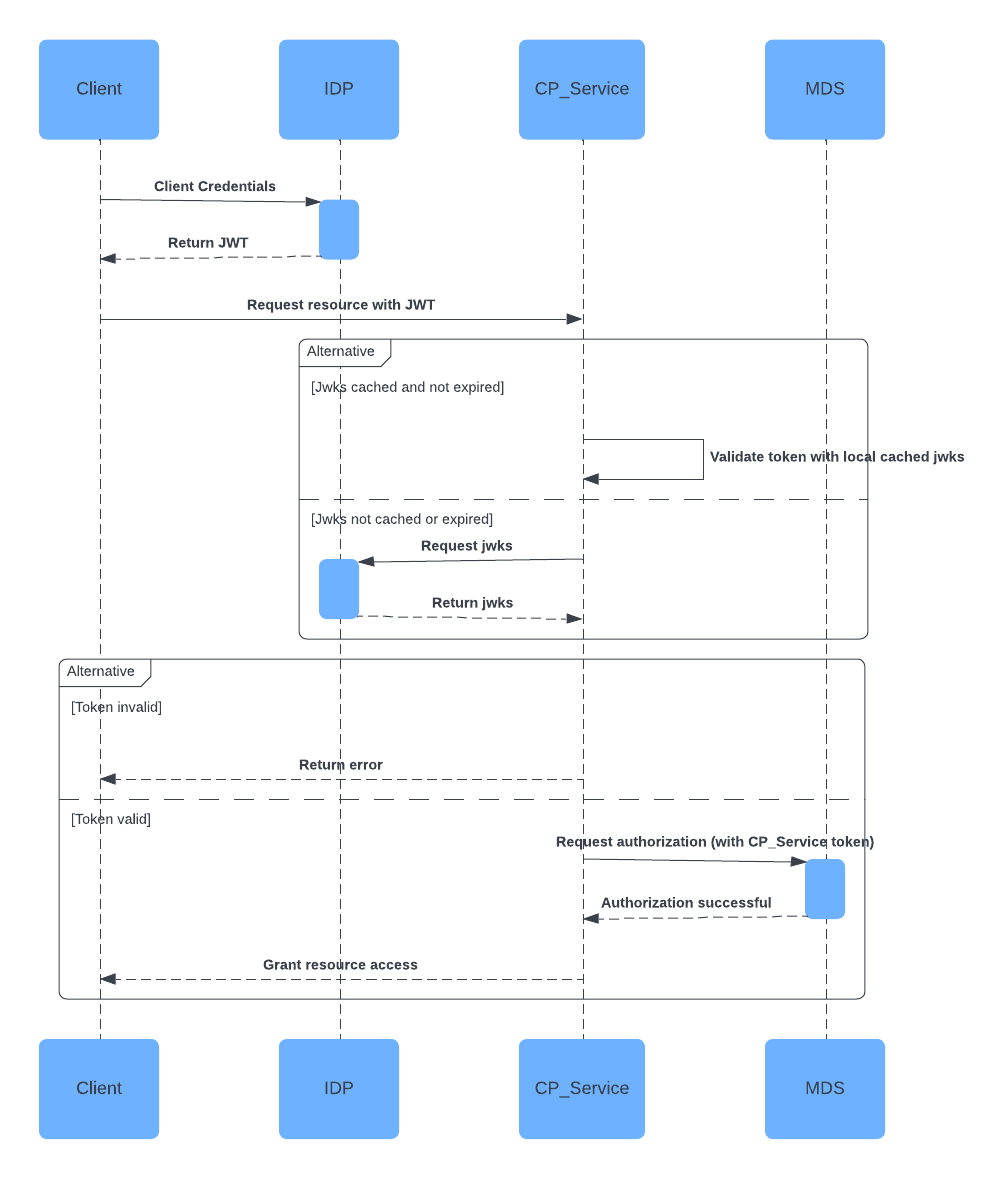
Use Rbac With Oauth Oidc In Confluent Platform Clusters Confluent
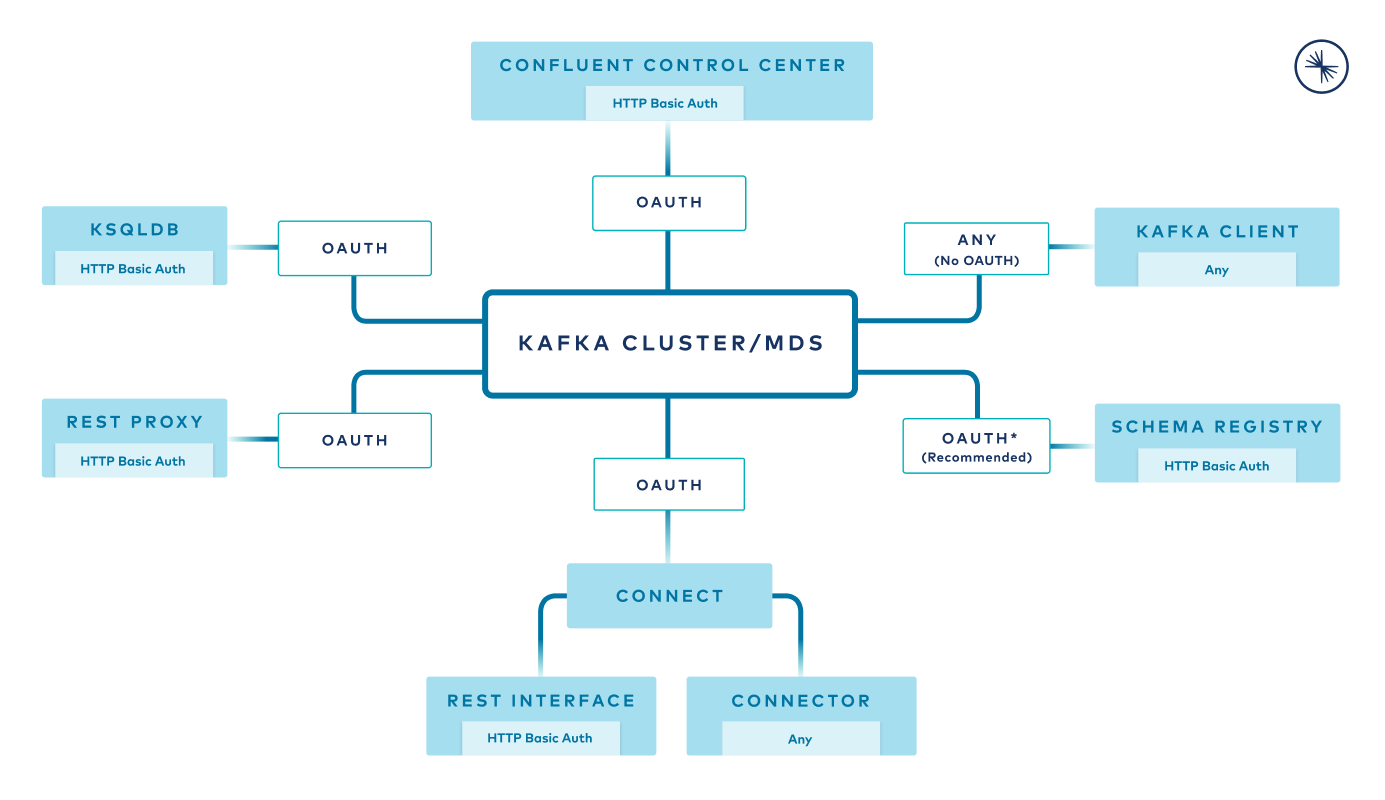
Authorize Using Role Based Access Control Rbac In Confluent Platform