
Cisco Ips Ids Interview Questions And Answers Vol 1 0 Pdf Identifying malicious traffic on the network signature based ips ids a signature is just a set of rules looking for some specific pattern or characteristic in either a single packet or a stream of packets. a new sensor may have thousands of default signatures provided by cisco. you can use them, modify them or create new ones. Cisco intrusion detection systems (ids) and intrusion prevention systems (ips) are some of many systems used as part of a defense in depth approach to protecting the network against malicious traffic.

Cisco Ids Ips Fundamentals Badly Connected Hi, i would like to confirm the apt placement of ids ips, whether it should be before or after firewall. i have cisco ips (two) which inspects packet till layer 7 which are in front of firewall and hence after inspection of traffic for malicious content, the traffic is further passed on to firewall. This cisco cyber security training course introduces readers and medium members to the fundamentals of network security. during this course, we will learn how to secure network using different. Cisco ids ips fundamentals atomic click the card to flip 👆 signatures that can match on a single packet, as compared to a string of packets. Cisco sd wan devices implement the ids ips functionality by leveraging the snort open source network intrusion prevention system (ips). snort is deployed in a linux container (lxc) hosted within the ios xe app hosting space.

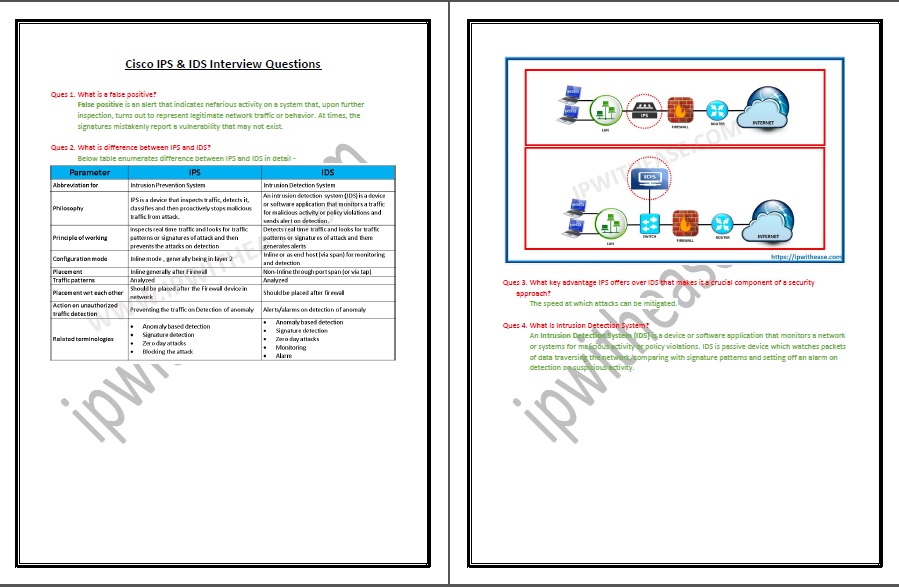
Cisco Ids Ips Fundamentals Sensor Platforms Dedicated Ips Appliance Cisco ids ips fundamentals atomic click the card to flip 👆 signatures that can match on a single packet, as compared to a string of packets. Cisco sd wan devices implement the ids ips functionality by leveraging the snort open source network intrusion prevention system (ips). snort is deployed in a linux container (lxc) hosted within the ios xe app hosting space. Ips rules cover both network bsed ips and host based ips. multicloud defense combines both of these systems within a singular profile to create an easy to configure network intrusion profile made to detect malicious probes or new network patterns from a compromised system that both detects, rejects, and reports supsicious traffic. An ids (intrusion detection system) is the predecessor of ips and is passive in nature. as shown from the network above (firewall with ids), this device is not inserted in line with the traffic but rather it is in parallel (placed out of band).

Cisco Ips Ids Network Interview Ips rules cover both network bsed ips and host based ips. multicloud defense combines both of these systems within a singular profile to create an easy to configure network intrusion profile made to detect malicious probes or new network patterns from a compromised system that both detects, rejects, and reports supsicious traffic. An ids (intrusion detection system) is the predecessor of ips and is passive in nature. as shown from the network above (firewall with ids), this device is not inserted in line with the traffic but rather it is in parallel (placed out of band).
Cisco Ips Ids Ip With Ease