
Classical Cryptography Pdf Cipher Encryption Classical cipher in cryptography, a classical cipher is a type of cipher that was used historically but for the most part, has fallen into disuse. in contrast to modern cryptographic algorithms, most classical ciphers can be practically computed and solved by hand. however, they are also usually very simple to break with modern technology. The security of classical cryptography is based on the high complexity of the mathematical problem for instance factorization of large numbers. in classical cryptography the original data i.e., the plain text is transformed into the encoded format i.e. cipher text so that we can transmit this data through insecure communication channels.

Lecture 1 Classical Cryptography Pdf Cryptography Cryptanalysis Classical ciphers, which are types of codes used in classical cryptography, include transposition ciphers, substitution ciphers, and concealment ciphers ( ). The running key cipher is similar to the vigenere cipher, but the key is usually a long piece of non repeating text. this makes it harder to break in general than the vigenere or autokey ciphers. vigenère and gronsfeld cipher a more complex polyalphabetic substitution cipher. code is provided for encryption, decryption and cryptanalysis. Geoffrey chaucer included several ciphers in his works leon alberti devised a cipher wheel, and described the principles of frequency analysis in the 1460s blaise de vigenère published a book on cryptology in 1585, & described the polyalphabetic substitution cipher increasing use, esp in diplomacy & war over centuries. Product ciphers use several ciphers in succession to make harder, but: two substitutions make a more complex substitution two transpositions make more complex transposition but a substitution followed by a transposition makes a new much harder cipher this is a bridge from classical to modern ciphers.

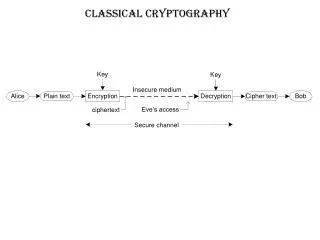
Solution Learn About Classical Cipher In Cryptography Studypool Geoffrey chaucer included several ciphers in his works leon alberti devised a cipher wheel, and described the principles of frequency analysis in the 1460s blaise de vigenère published a book on cryptology in 1585, & described the polyalphabetic substitution cipher increasing use, esp in diplomacy & war over centuries. Product ciphers use several ciphers in succession to make harder, but: two substitutions make a more complex substitution two transpositions make more complex transposition but a substitution followed by a transposition makes a new much harder cipher this is a bridge from classical to modern ciphers. Classical cryptosystems there are two classical symmetric key ciphers: transposition ciphers and substitution ciphers. we will look at both of these examples. Symmetric cipher model symmetric encryption is a form of cryptosystem in which encryption and decryption are performed using the same key. it is also known as conventional encryption. symmetric encryption transforms plaintext into cipher text using a secret key and an encryption algorithm.

Classical Cryptography Cipher Cryptography Classical cryptosystems there are two classical symmetric key ciphers: transposition ciphers and substitution ciphers. we will look at both of these examples. Symmetric cipher model symmetric encryption is a form of cryptosystem in which encryption and decryption are performed using the same key. it is also known as conventional encryption. symmetric encryption transforms plaintext into cipher text using a secret key and an encryption algorithm.

Ppt Classical Cryptography Powerpoint Presentation Free Download
Ppt Classical Cryptography Powerpoint Presentation Free Download