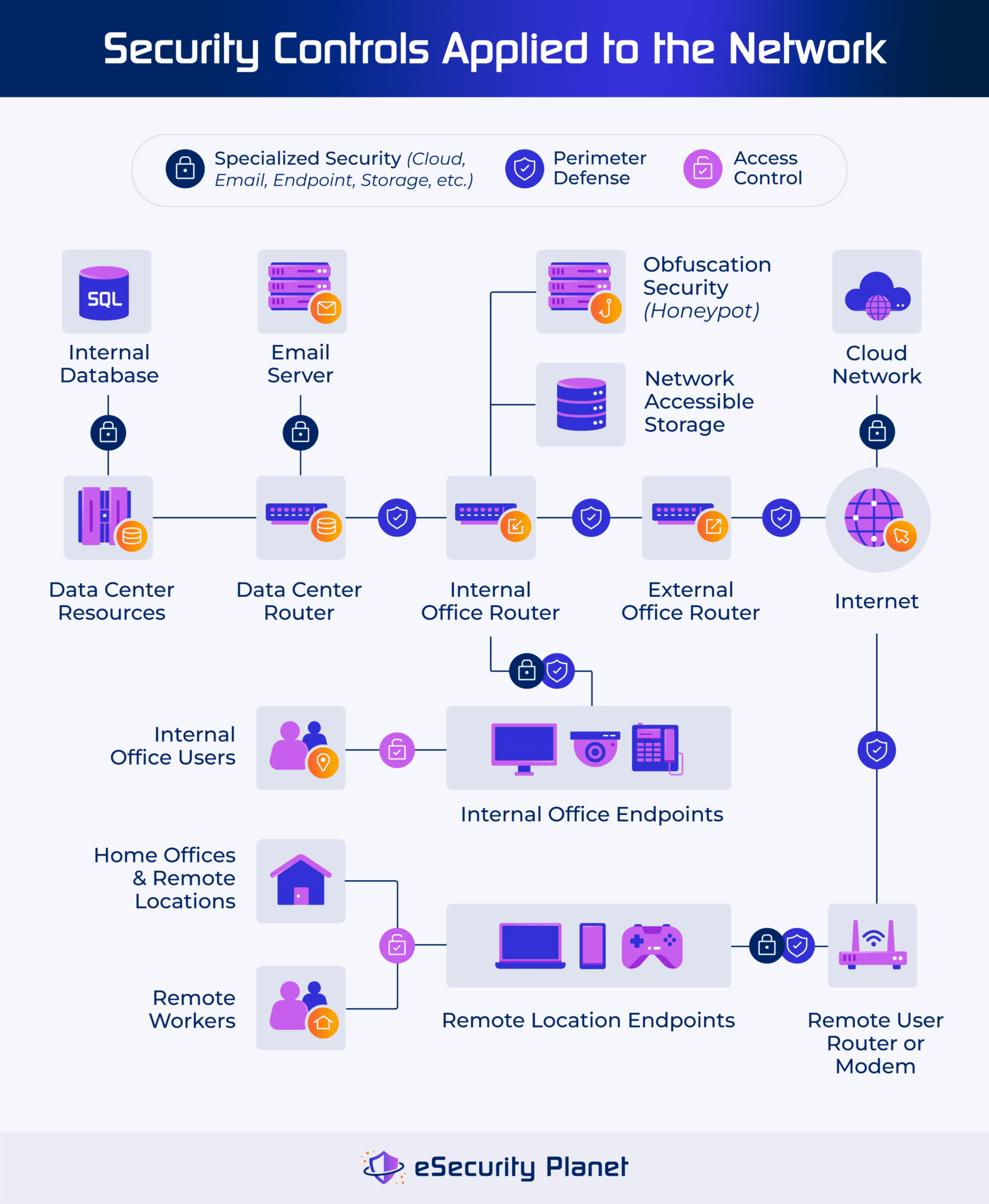
Network Security Architecture Best Practices Tools Mobile work is now the norm To stay secure, businesses must combine layered defenses, AI tools, and continuous employee training in a flexible, tested strategy In a groundbreaking move set to reshape the cybersecurity landscape, Palo Alto Networks, a leading global cybersecurity company, has announced

Secure Network Architecture Global Cyber Security Solutions Letting your guard down is not the most reasonable thing to do at a time when cybersecurity risks are on the rise; cyber attackers are not resting What's more, they are well aware of what happens at Despite best efforts, the collective cybersecurity profession has been unable to effectively prepare for how attackers’ techniques and trends will change That is due in large part to a failure FinTech ecosystems, which include banks, insurance firms, lending agencies, and startups, are increasingly targeted by cybercriminals leveraging sophisticated techniques The study sheds light on how CISA's "microsegmentation" guidance will help agencies adopt practices that stop hackers from moving laterally within networks - a key aspect of zero trust

Cyber Security Architecture Cosmos Cyber Security FinTech ecosystems, which include banks, insurance firms, lending agencies, and startups, are increasingly targeted by cybercriminals leveraging sophisticated techniques The study sheds light on how CISA's "microsegmentation" guidance will help agencies adopt practices that stop hackers from moving laterally within networks - a key aspect of zero trust Bitwarden, the trusted leader in password, passkey, and secrets management, today announced that Convergence Networks, a North American managed service provider (MSP) serving highly regulated Overview: The global cybersecurity market is projected to hit $300 billion by 2027, and these top 10 players are leading the chargeCompanies like Palo Alto Net US cybersecurity stocks remain in focus following a massive attack on Microsoft’s on-premises SharePoint servers that enabled hackers infiltrate more than 100 organisations globally – including WASHINGTON — Without the right level and right kind of cybersecurity architecture in place, adversary nations will continue to infiltrate US military and partner networks, including

What Is Cyber Security Architecture Architecture Bitwarden, the trusted leader in password, passkey, and secrets management, today announced that Convergence Networks, a North American managed service provider (MSP) serving highly regulated Overview: The global cybersecurity market is projected to hit $300 billion by 2027, and these top 10 players are leading the chargeCompanies like Palo Alto Net US cybersecurity stocks remain in focus following a massive attack on Microsoft’s on-premises SharePoint servers that enabled hackers infiltrate more than 100 organisations globally – including WASHINGTON — Without the right level and right kind of cybersecurity architecture in place, adversary nations will continue to infiltrate US military and partner networks, including Cybersecurity Review 2023: Our Top Picks Palo Alto Networks And Fortinet Jan 31, 2023 11:01 AM ET Fortinet, Inc (FTNT) Stock, PANW Stock CHKP, CRWD, ZS S FTNT PANW 36 Comments 36 Likes Convequity Floods, fires and earthquakes can physically destroy servers and data centres If there are no backups stored safely in other locations, years of records can vanish in an instant This can affect

Cyber Security Architecture Building Digital Fortresses US cybersecurity stocks remain in focus following a massive attack on Microsoft’s on-premises SharePoint servers that enabled hackers infiltrate more than 100 organisations globally – including WASHINGTON — Without the right level and right kind of cybersecurity architecture in place, adversary nations will continue to infiltrate US military and partner networks, including Cybersecurity Review 2023: Our Top Picks Palo Alto Networks And Fortinet Jan 31, 2023 11:01 AM ET Fortinet, Inc (FTNT) Stock, PANW Stock CHKP, CRWD, ZS S FTNT PANW 36 Comments 36 Likes Convequity Floods, fires and earthquakes can physically destroy servers and data centres If there are no backups stored safely in other locations, years of records can vanish in an instant This can affect