
Navigating The Intersection Of Iot And Cybersecurity Providing solutions, and information from leading vendors and experts in the channel to help them successfully deliver security services. join our community to receive our monthly cybersecurity run down newsletter, recent podcasts, expert panels, virtual events and industry news. your cybersecurity resource!. South korea’s internet and security agency (kisa) has introduced a certification of iot cybersecurity (cic), which formally certifies iot devices into three grades—iot lite, basic, and standard—with each having a different timeline for certification (anywhere from 6 weeks to more than 12 weeks) and different costs for each level of.

Cybersecurity Measures For Industrial Iot Global Cybersecurity What is iot security? iot security is a subsect of cybersecurity that focuses on protecting, monitoring and remediating threats related to the internet of things (iot) — the network of connected devices equipped with sensors, software or other technologies to gather, store and share data via the internet. The growing tempo of iot adoption sets the stage for regulatory actions. get a clear overview of the main us and eu policy and regulatory initiatives regarding cyber security for connected devices!. Our stakeholders include iot hardware and software product vendors, network operators, system specifiers, integrators, distributors, retailers, insurers, local authorities, academic institutions, government agencies security professionals, researchers and risk managers – anybody with an interest in cyber safety, security and privacy. Iot cybersecurity related initiatives non regulatory agency and technical arm of the u.s. department of commerce nist’s mission is to promote u.s. innovation and industrial competitiveness by advancing measurement science, standards, and technology in ways that enhance economic security and improve our quality of life.

Internet Of Things Iot Security Services In Dubai Our stakeholders include iot hardware and software product vendors, network operators, system specifiers, integrators, distributors, retailers, insurers, local authorities, academic institutions, government agencies security professionals, researchers and risk managers – anybody with an interest in cyber safety, security and privacy. Iot cybersecurity related initiatives non regulatory agency and technical arm of the u.s. department of commerce nist’s mission is to promote u.s. innovation and industrial competitiveness by advancing measurement science, standards, and technology in ways that enhance economic security and improve our quality of life. As more devices in the home connect to the internet, the cyber security of the internet of things (iot) becomes a growing concern. people entrust their personal data to an increasing number of online devices and services. The gsma iot security guidelines overview (fs.60) promotes a methodology for developing secure iot services to ensure security best practices are implemented throughout the life cycle of iot products and services. it provides recommendations on how to mitigate common security threats and weaknesses within iot services.
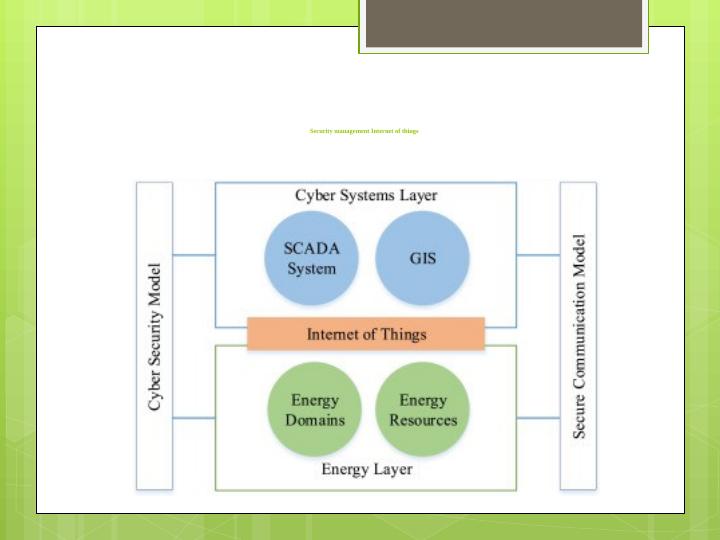
Scada Based Cyber Security Management In Iot Desklib As more devices in the home connect to the internet, the cyber security of the internet of things (iot) becomes a growing concern. people entrust their personal data to an increasing number of online devices and services. The gsma iot security guidelines overview (fs.60) promotes a methodology for developing secure iot services to ensure security best practices are implemented throughout the life cycle of iot products and services. it provides recommendations on how to mitigate common security threats and weaknesses within iot services.

Scada Based Cyber Security Management In Iot Desklib

Enabling Iot And Cyber Security

Running Iot Cyber Security Awareness Improving Iot Device Cybersecurity