
Public Key Encryption Pdf Public Key Cryptography Cryptography Goals: authenticating users and their public keys with certificates signed by certificate authorities (ca) exchanging session keys with public key cryptography x.509 certificates or harvesting rsa moduli from x.509 certifica. Unit 3 public key cryptography principles, public key cryptography algorithms, digital signatures, digital certificates, certificate authority and key management kerberos, x.509 directory authentication service.

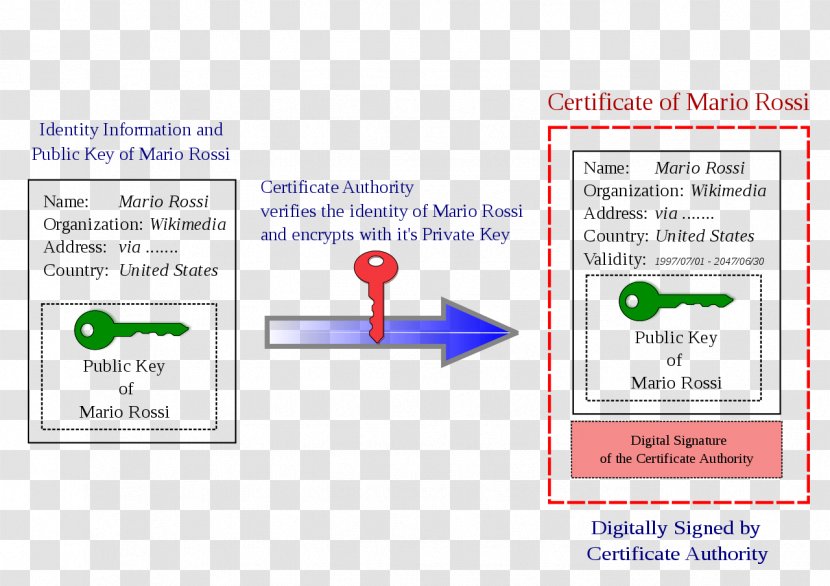
Digital Signature Pdf Cryptography Public Key Cryptography A digital signature is a specific type of electronic signature that uses cryptographic techniques such as public and private key pairs to verify the authenticity and integrity of a message or document. Public key is a very appealing and exciting technology, embedding both encryption and digital signature. this constitutes a breakthrough over symmetric key cryptosystems. A digital certificate binds a public key to the entity that holds the corresponding private key. the ca verifies this binding to ensure that the entity presenting the certificate is the actual owner of the public key. Out of all cryptographic primitives, the digital signature using public key cryptography is considered as very important and useful tool to achieve information security.

Digital Signature Pdf Public Key Cryptography Cryptography A digital certificate binds a public key to the entity that holds the corresponding private key. the ca verifies this binding to ensure that the entity presenting the certificate is the actual owner of the public key. Out of all cryptographic primitives, the digital signature using public key cryptography is considered as very important and useful tool to achieve information security. Asymmetric keys two related keys – a public key and a private key, that are used to perform complemetatry operations, such as encryption and decryption or signature generation and signature verification public key certificate a digital document issued and digitally signed by the private key of the certification authority that binds. Public key cryptography fulfills an extremely important role in the overall design and operation of secure computer networks. because it leads to superior protocols for managing and distributing secret session keys.

Digital Signature Standard Pdf Public Key Cryptography Cryptography Asymmetric keys two related keys – a public key and a private key, that are used to perform complemetatry operations, such as encryption and decryption or signature generation and signature verification public key certificate a digital document issued and digitally signed by the private key of the certification authority that binds. Public key cryptography fulfills an extremely important role in the overall design and operation of secure computer networks. because it leads to superior protocols for managing and distributing secret session keys.

Digital Signature And Encryption Example Pdf Public Key
Public Key Certificate Public Key Cryptography Chiave Pubblica Dijital