Hashing Vs Encryption Vs Encoding The Differences Explained In cryptography, encryption (more specifically, encoding) is the process of transforming information in a way that, ideally, only authorized parties can decode. this process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Encryption is a cybersecurity measure that scrambles plain text so it can only be read by the user who has the secret code, or decryption key. it provides added security for sensitive information.

Hashing Vs Encryption Vs Encoding The Differences Explained The primary purpose of encryption is to protect the confidentiality of digital data stored on computer systems or transmitted over the internet or other computer networks. it is used to safeguard a wide range of data, from pii to sensitive corporate assets to government and military secrets. Encryption is a form of data security in which information is converted to ciphertext. only authorized people who have the key can decipher the code and access the original plaintext information. in even simpler terms, encryption is a way to render data unreadable to an unauthorized party. Data encryption keeps information distinct from the security of the device on which it is stored. encryption provides security by allowing administrators to store and send data via insecure channels. if the password or key is lost, the user will be unable to open the encrypted file. Encryption is the process of transforming readable plain text into unreadable ciphertext to mask sensitive information from unauthorized users. organizations regularly use encryption in data security to protect sensitive data from unauthorized access and data breaches.

Encryption Vs Hashing Explained For Beginners Data encryption keeps information distinct from the security of the device on which it is stored. encryption provides security by allowing administrators to store and send data via insecure channels. if the password or key is lost, the user will be unable to open the encrypted file. Encryption is the process of transforming readable plain text into unreadable ciphertext to mask sensitive information from unauthorized users. organizations regularly use encryption in data security to protect sensitive data from unauthorized access and data breaches. Encryption is the process of converting or scrambling data and information into an unreadable, encoded version that can only be read with authorized access. encryption is a widely used security tool that can prevent the interception of sensitive data, either while stored in files or while in transit across networks. Encryption is a mathematical process that alters data using an encryption algorithm and a key. imagine if alice sends the message "hello" to bob, but she replaces each letter in her message with the letter that comes two places later in the alphabet. instead of "hello," her message now reads "jgnnq.".

Hashing Vs Encryption Vs Encoding Explained By Experts Encryption is the process of converting or scrambling data and information into an unreadable, encoded version that can only be read with authorized access. encryption is a widely used security tool that can prevent the interception of sensitive data, either while stored in files or while in transit across networks. Encryption is a mathematical process that alters data using an encryption algorithm and a key. imagine if alice sends the message "hello" to bob, but she replaces each letter in her message with the letter that comes two places later in the alphabet. instead of "hello," her message now reads "jgnnq.".
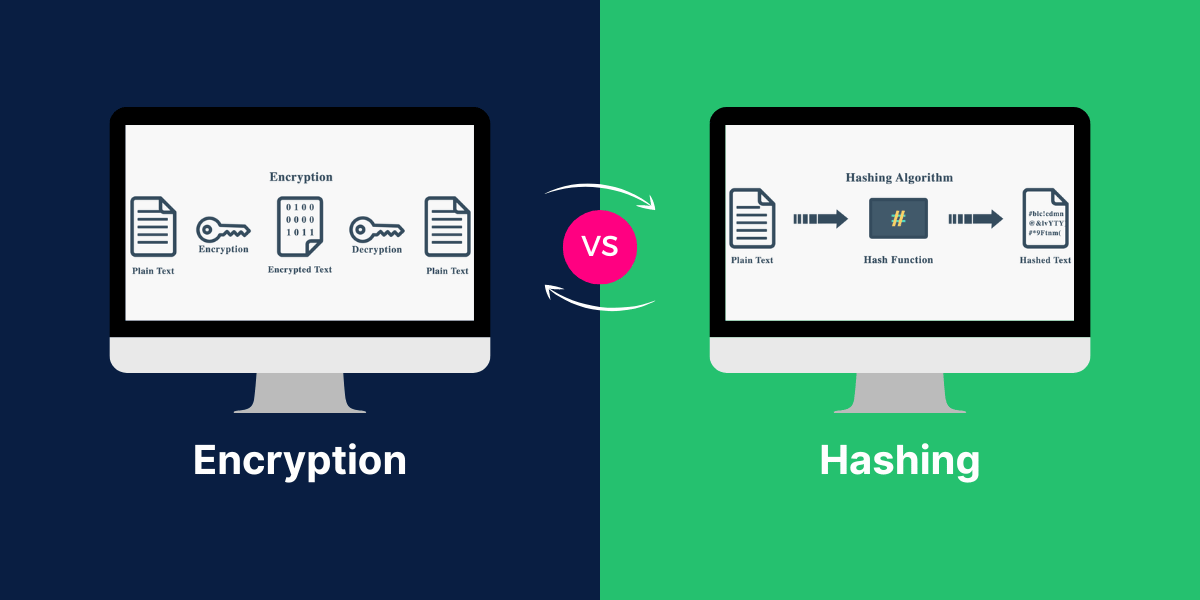
Difference Between Encryption And Hashing Sebastine