
Firewall Implementation For Cyber Security Post Firewall Implementation The firewall is one of the most fundamental parts of any cybersecurity architecture. learn how to elevate your firewall implementation and optimize your cyberdefenses. Discover how a strategic firewall implementation project plan can bolster your network security. this article outlines key steps and considerations for a successful deployment.

Firewall Implementation For Cyber Security Post Firewall Implementation Learn how proper firewall implementation and optimization protect against cyber threats. explore best practices and zero trust for stronger network security. Learn the complete process of firewall implementation and configuration with our expert guide. protect your network with proper setup, deployment, and ongoing management. Furthermore, this firewall as a service integration for advanced cyber defense template caters to the deployment method and firewall type selection process, different architectural implementation strategies, and steps for choosing a suitable architecture implementation strategy. This firewall implementation plan outlines the key steps, responsibilities, timelines, and resources necessary to successfully implement a firewall in accordance with the company's security policies. this document serves as a comprehensive guide for all stakeholders involved in the implementation process.
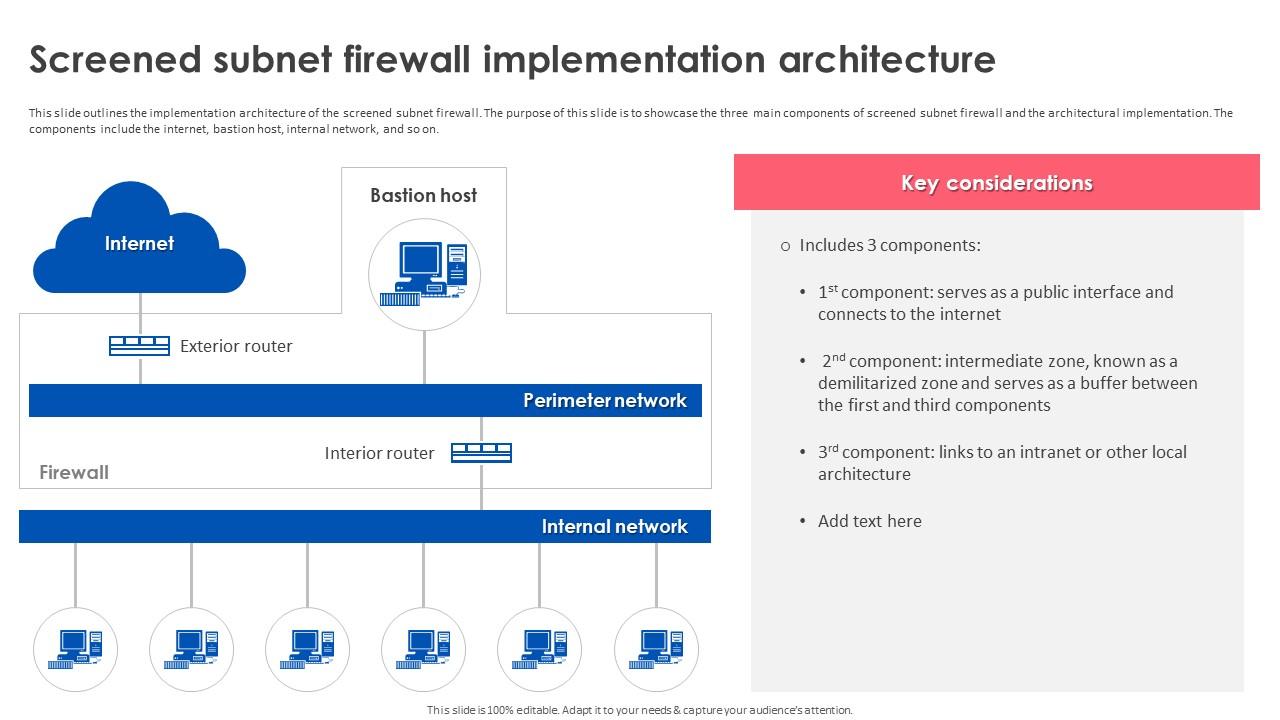
Firewall Implementation For Cyber Security Screened Subnet Firewall Furthermore, this firewall as a service integration for advanced cyber defense template caters to the deployment method and firewall type selection process, different architectural implementation strategies, and steps for choosing a suitable architecture implementation strategy. This firewall implementation plan outlines the key steps, responsibilities, timelines, and resources necessary to successfully implement a firewall in accordance with the company's security policies. this document serves as a comprehensive guide for all stakeholders involved in the implementation process. The firewall is an essential first line of network defense, filtering traffic and blocking malicious outsiders from gaining access to your critical systems. businesses today commonly use multiple firewalls to create a system of protected network segments with varying security needs. in this post, we’ll take a brief look at five primary types of firewalls and the three main implementation. Abstract in an era where digital threats are increasingly sophisticated, the mastery of firewalls remains a cornerstone of effective cybersecurity. "firewall mastery: advanced strategies for implementation and digital defense" delves into the critical role firewalls play in safeguarding organizational assets and ensuring secure communications in both on premises and cloud environments. this.
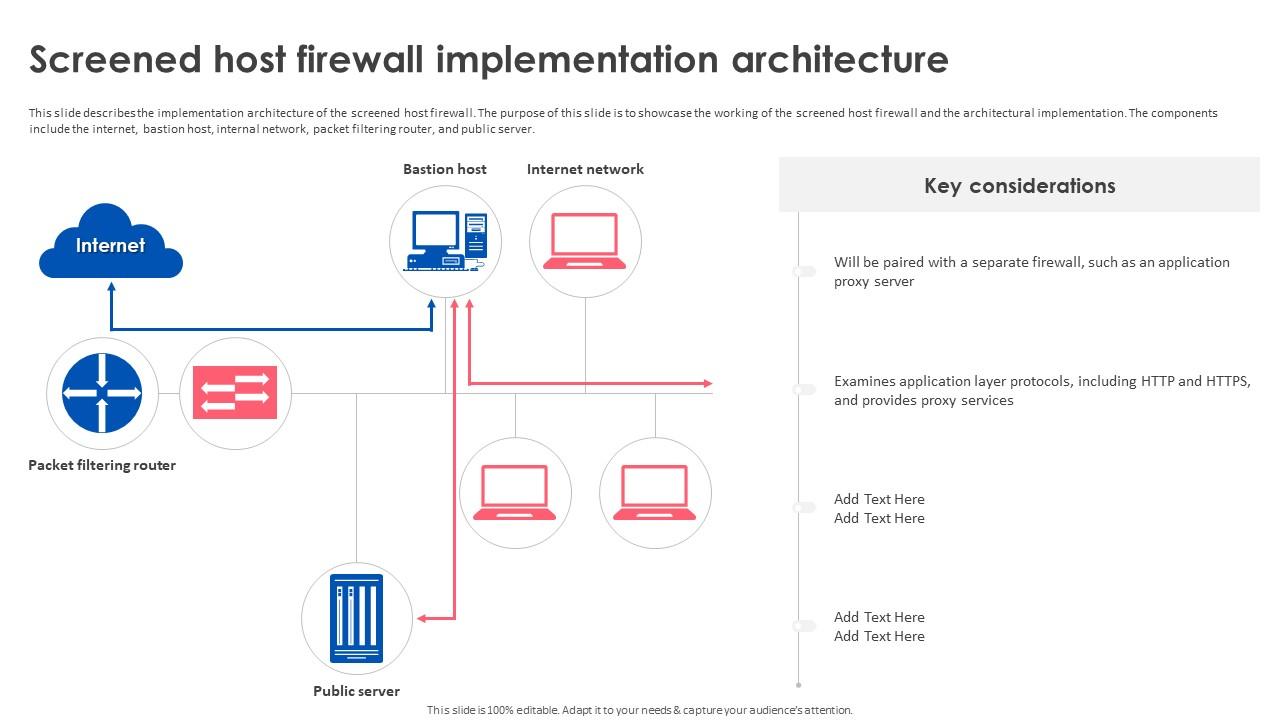
Firewall Implementation For Cyber Security Screened Host Firewall The firewall is an essential first line of network defense, filtering traffic and blocking malicious outsiders from gaining access to your critical systems. businesses today commonly use multiple firewalls to create a system of protected network segments with varying security needs. in this post, we’ll take a brief look at five primary types of firewalls and the three main implementation. Abstract in an era where digital threats are increasingly sophisticated, the mastery of firewalls remains a cornerstone of effective cybersecurity. "firewall mastery: advanced strategies for implementation and digital defense" delves into the critical role firewalls play in safeguarding organizational assets and ensuring secure communications in both on premises and cloud environments. this.

Firewall Implementation For Cyber Security Firewall Architecture
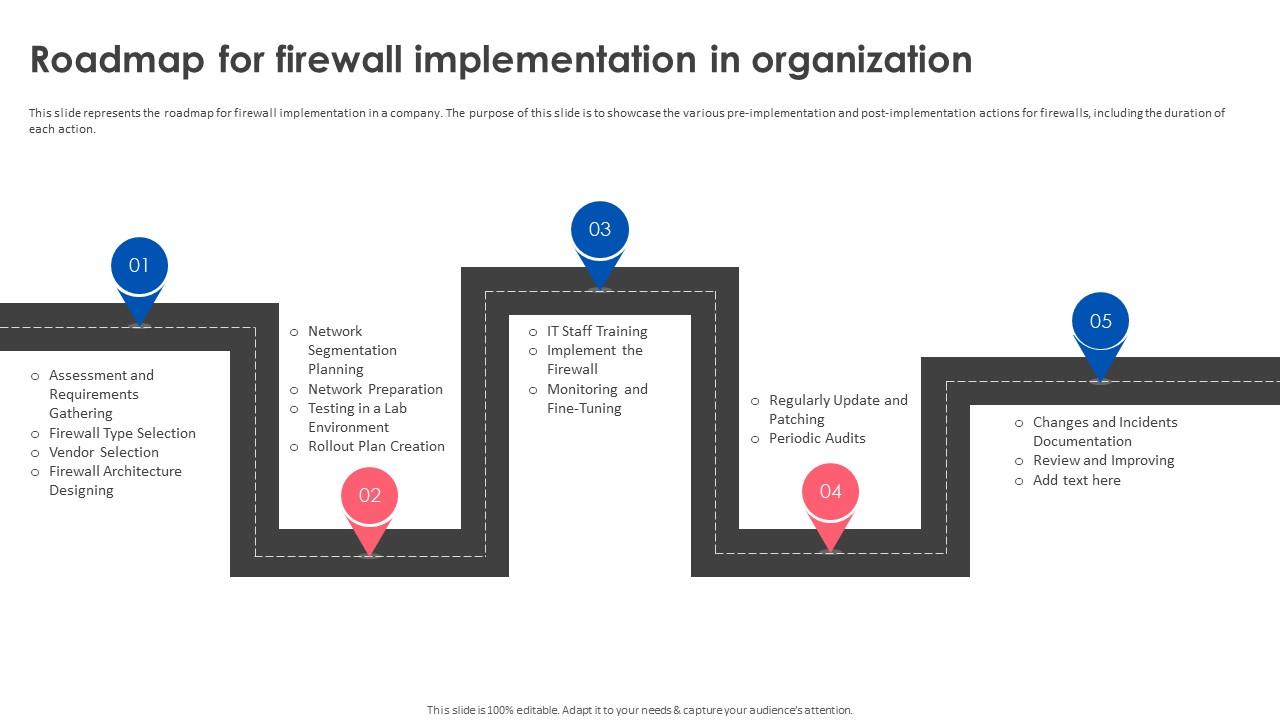
Firewall Implementation For Cyber Security Roadmap For Firewall

Firewall Implementation For Cyber Security Timeline For Firewall