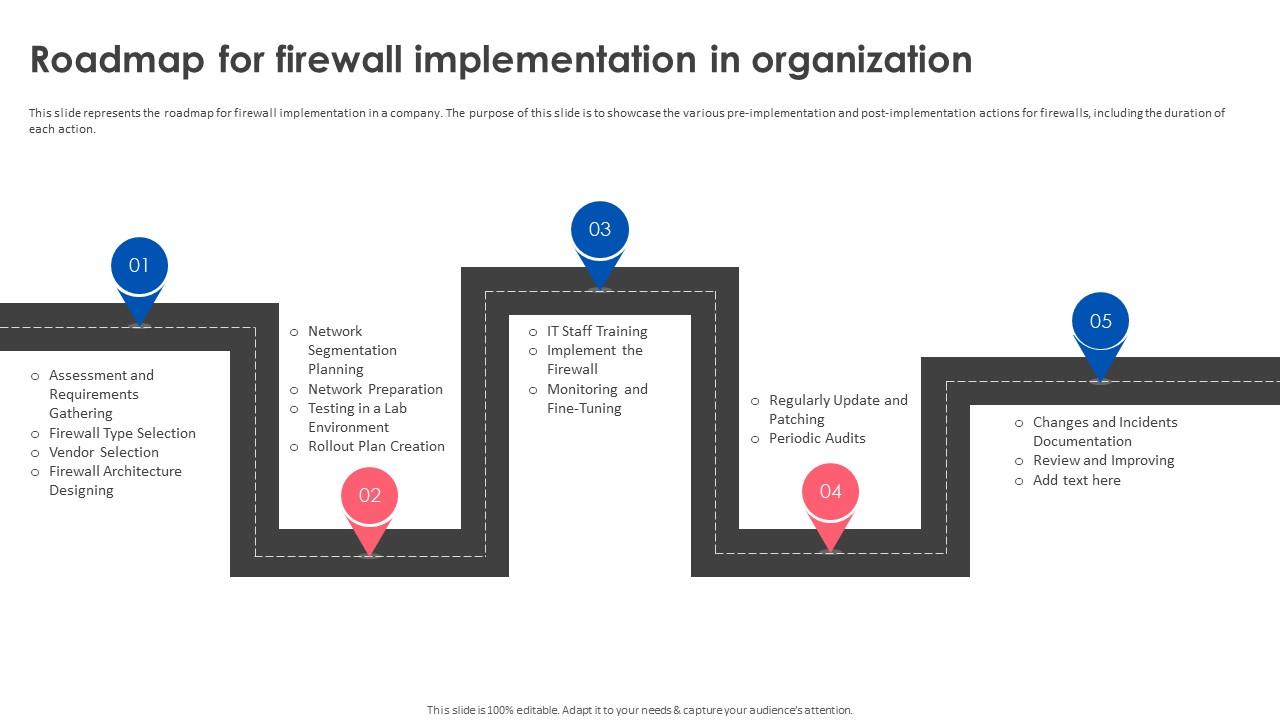
Firewall Implementation For Cyber Security Roadmap For Firewall Discover how a strategic firewall implementation project plan can bolster your network security. this article outlines key steps and considerations for a successful deployment. The firewall is one of the most fundamental parts of any cybersecurity architecture. learn how to elevate your firewall implementation and optimize your cyberdefenses.

Cybersecurity Firewalls Protocols Needs Algorithm Pdf Firewall This document provides an overview of firewall technologies and discusses their security capabilities and relative advantages and disadvantages in detail. it also provides examples of where firewalls can be placed within networks, and the implications of deploying firewalls in particular locations. Lastly, this firewall implementation for cyber security powerpoint presentation includes a roadmap and kpis dashboard to monitor performance, post implementation impact, and before versus after business scenarios. Learn how proper firewall implementation and optimization protect against cyber threats. explore best practices and zero trust for stronger network security. The implementation of a secured perimeter and internal firewall network architecture and conducting vulnerability assessments and penetration tests (vapt) are often seen as enough to protect critical business information and guard against unexpected cybersecurity threats. however, as we will discover and despite this approach being a good start, there is substantially more to information.

Quarterly Cyber Security Implementation Approach Roadmap Presentation Learn how proper firewall implementation and optimization protect against cyber threats. explore best practices and zero trust for stronger network security. The implementation of a secured perimeter and internal firewall network architecture and conducting vulnerability assessments and penetration tests (vapt) are often seen as enough to protect critical business information and guard against unexpected cybersecurity threats. however, as we will discover and despite this approach being a good start, there is substantially more to information. Syslogs netflow packet captures firewall logs understand hardening concepts mac based nac based. A firewall is a network security device designed to monitor, filter, and control incoming and outgoing network traffic based on predetermined security rules. the primary purpose of a firewall is to establish a barrier between a trusted internal network and untrusted external networks. firewalls come in both hardware and software forms, and they work by inspecting data packets and determining.

Cyber Security Roadmap Syslogs netflow packet captures firewall logs understand hardening concepts mac based nac based. A firewall is a network security device designed to monitor, filter, and control incoming and outgoing network traffic based on predetermined security rules. the primary purpose of a firewall is to establish a barrier between a trusted internal network and untrusted external networks. firewalls come in both hardware and software forms, and they work by inspecting data packets and determining.
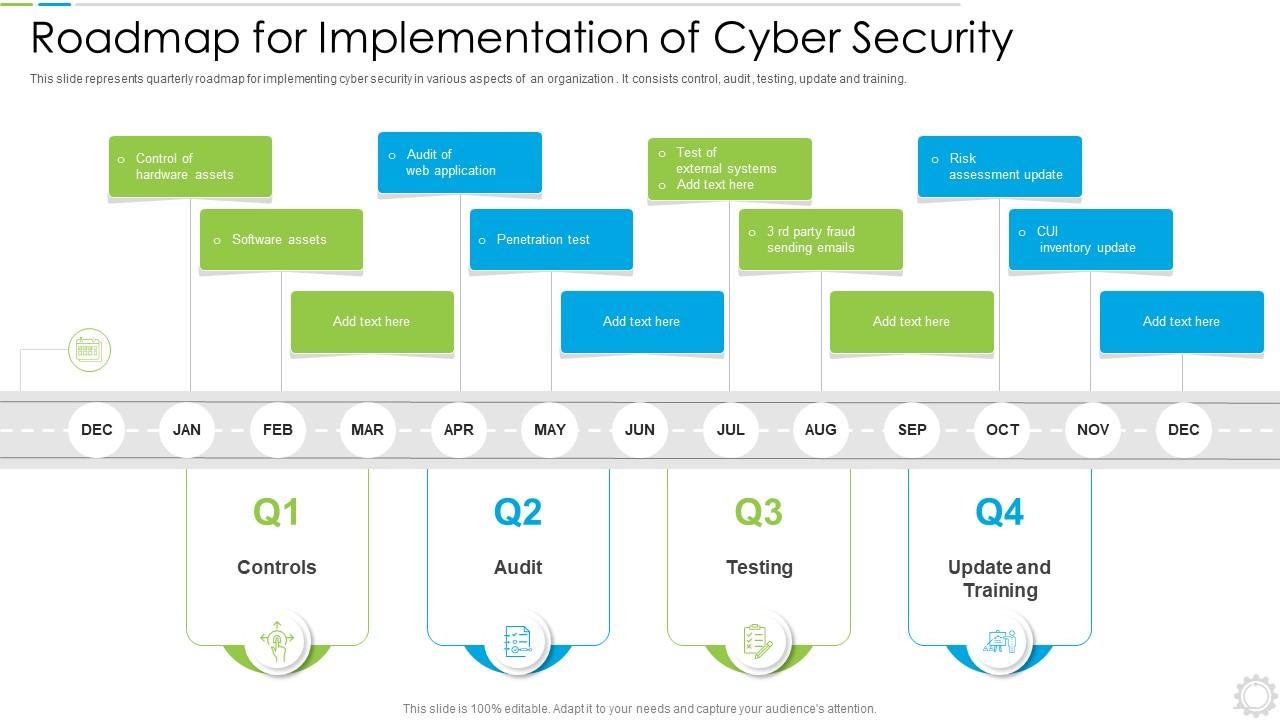
Roadmap For Implementation Of Cyber Security Presentation Graphics