
Cyber Security Firewall Pdf Kernel Operating System Operating In this way, the bastion host and router protects the data and is more effective and secure implementation. dual homed host firewalls this architecture is a more complex implementation of screened host firewalls. in this architectural approach, the bastion host accommodates two nics (network interface cards) in the bastion host configuration. This document provides an overview of firewall technologies and discusses their security capabilities and relative advantages and disadvantages in detail. it also provides examples of where firewalls can be placed within networks, and the implications of deploying firewalls in particular locations.
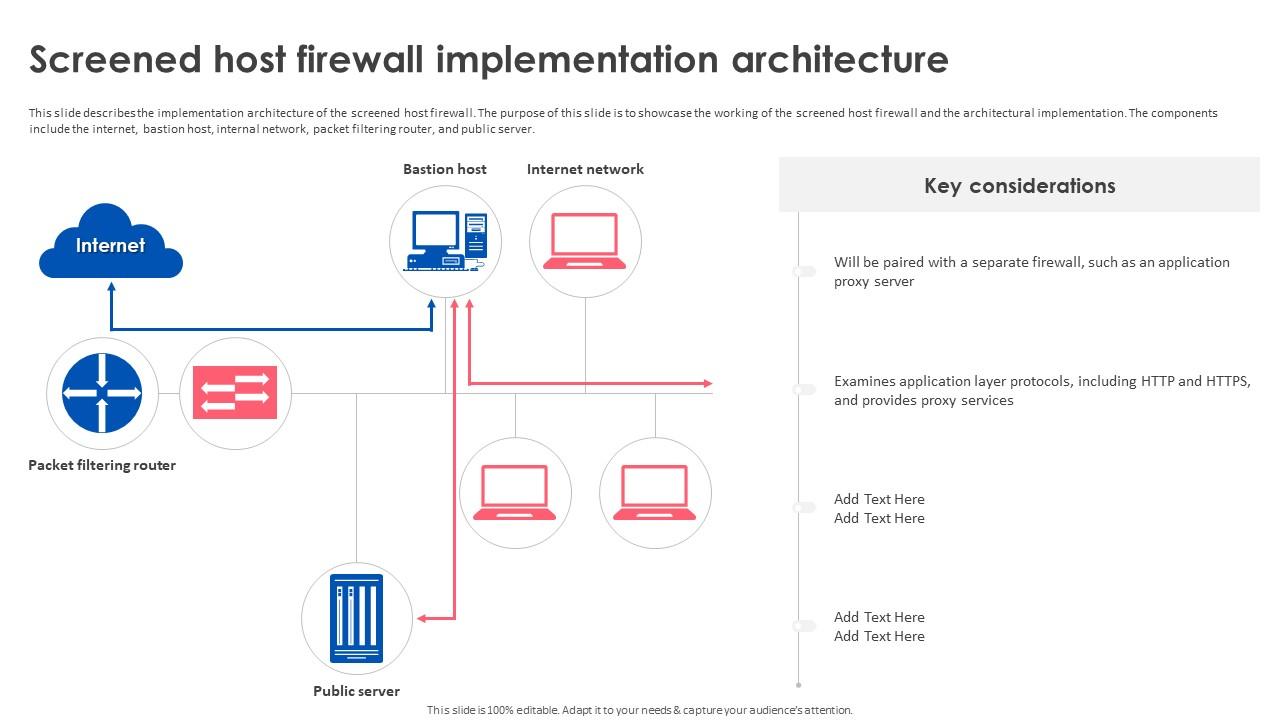
Firewall Implementation For Cyber Security Screened Host Firewall There are several types of firewalls that work on different layers of the osi model. depending on the kind of service and security you need for your network, you need to choose the right type of firewall. the following are the list of seven different types firewalls that are widely used for network security. screened host firewalls screened subnet firewalls packet filter firewalls stateful. Discover the different types of firewalls and their functions. learn which firewall solution best fits your organization's cybersecurity needs. A firewall is a hardware or software to prevent a private computer or a network of computers from unauthorized access, it acts as a filter to avoid unauthorized users from accessing private computers and networks. it is a vital component of network security. it is the first line of defense for network security. it filters network packets and stops malware from entering the user's computer or. A firewall is a network security device designed to monitor, filter, and control incoming and outgoing network traffic based on predetermined security rules. the primary purpose of a firewall is to establish a barrier between a trusted internal network and untrusted external networks. firewalls come in both hardware and software forms, and they work by inspecting data packets and determining.
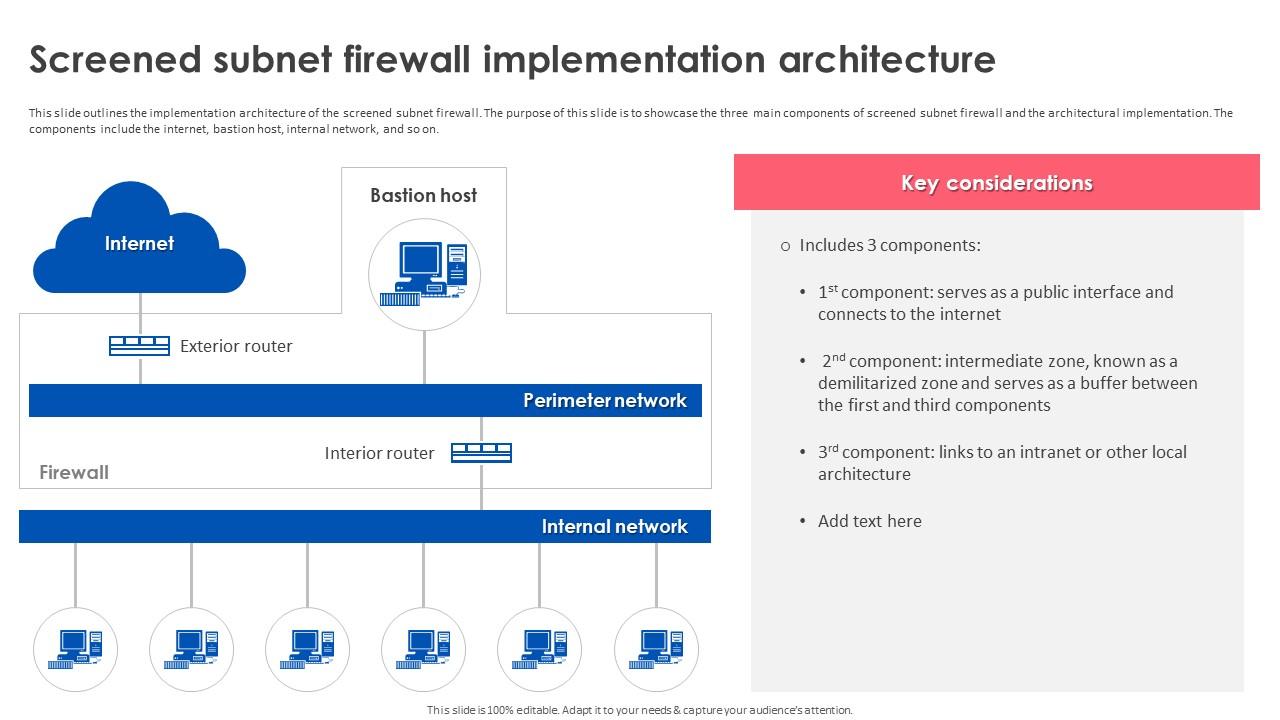
Firewall Implementation For Cyber Security Screened Subnet Firewall A firewall is a hardware or software to prevent a private computer or a network of computers from unauthorized access, it acts as a filter to avoid unauthorized users from accessing private computers and networks. it is a vital component of network security. it is the first line of defense for network security. it filters network packets and stops malware from entering the user's computer or. A firewall is a network security device designed to monitor, filter, and control incoming and outgoing network traffic based on predetermined security rules. the primary purpose of a firewall is to establish a barrier between a trusted internal network and untrusted external networks. firewalls come in both hardware and software forms, and they work by inspecting data packets and determining. What is a firewall, and what does a firewall do? learn the different ways to monitor your network activity, and find your ideal network security device. Firewall architectures the configuration that works best for a particular organization depends on three factors: the objectives of the network, the organization‘s ability to develop and implement the architectures, and the budget available for the function. there are four common architectural implementations of firewalls.these implementations are packet filtering routers, screened host.

Cybersecurity Firewalls Protocols Needs Algorithm Pdf Firewall What is a firewall, and what does a firewall do? learn the different ways to monitor your network activity, and find your ideal network security device. Firewall architectures the configuration that works best for a particular organization depends on three factors: the objectives of the network, the organization‘s ability to develop and implement the architectures, and the budget available for the function. there are four common architectural implementations of firewalls.these implementations are packet filtering routers, screened host.