
Cyber Security Firewall Pdf Kernel Operating System Operating Windows firewall keeps bringing up randomly the firewall permission windows alert. in other words it doesn't remember that i allowed a program. hey folks, i've been having some alzheimer issues with windows, since windows 8, after i have used the command netstat renew. since then (even after upgrading to windows 10). Both interfaces are assigned to the wan firewall zone. i'm guessing this initial fw4 implementation won't represent a 100% native nftables approach, but a way to represent the existing firewall rules in nftables. i'd like to see more verdict maps and concatenations.

Cybersecurity Firewalls Protocols Needs Algorithm Pdf Firewall If i go to network > firewall > general settings, and set 'forward' to 'drop' in the general settings and zones, how is it possible that openwrt continues to forward traffic?. I have 2 issues. if i disable firewall completely via etc init.d firewall stop then i am able to access my ipv6 entities outside network and if i restart firewall, it doesn't work to access my ipv6 entities outside the …. Hello great team. i have a device running the last version of openwrt, which seem to work so far. however, i would like to manage the firewall rules using an nftables script i would upload over sftp on the device. my preliminary tests seem to work, and are replacing the firewall rules accordingly. however, i would like to know, if i can disable the web interfaces that manage the firewall rules. Yes, between two subnets, you can absolutely control the allowed denied routing with the firewall. you'll create firewall rules with the source and destination ip addresses. you can even use ip sets to make this an easy 1 rule configuration. 2 likes amd.64 january 19, 2025, 9:45pm 3.

Firewall Implementation For Cyber Security Firewall Architecture Hello great team. i have a device running the last version of openwrt, which seem to work so far. however, i would like to manage the firewall rules using an nftables script i would upload over sftp on the device. my preliminary tests seem to work, and are replacing the firewall rules accordingly. however, i would like to know, if i can disable the web interfaces that manage the firewall rules. Yes, between two subnets, you can absolutely control the allowed denied routing with the firewall. you'll create firewall rules with the source and destination ip addresses. you can even use ip sets to make this an easy 1 rule configuration. 2 likes amd.64 january 19, 2025, 9:45pm 3. Disclaimer: i have no clue about nftables and the firewall settings in this regard, just picking brains here. nftales not knowing about local dates and time zones would mean time based rules are fundamentally broken in nftables. Have to create 2 rule each for lan (main) and guest network even if they do they same thing foreach zone. it would be nice to combine them into one multiple destination for example, allow port 443 from lan to wan and vpn.
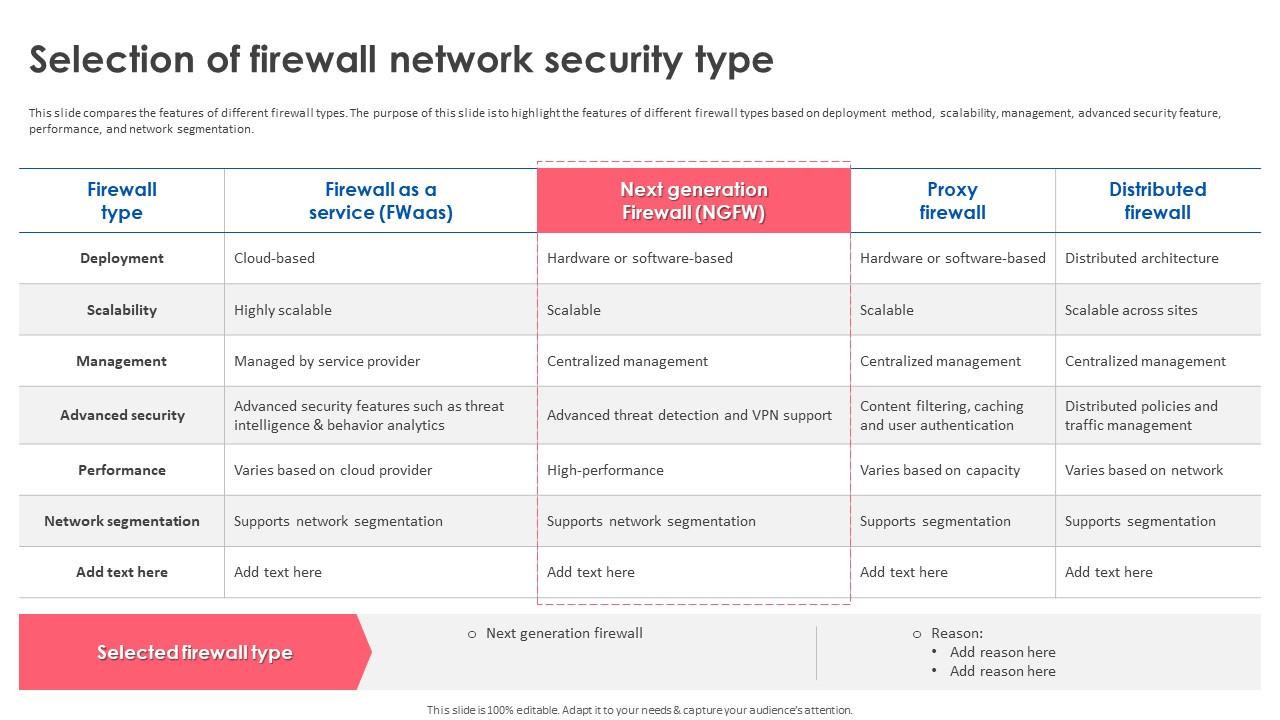
Firewall Implementation For Cyber Security Selection Of Firewall Disclaimer: i have no clue about nftables and the firewall settings in this regard, just picking brains here. nftales not knowing about local dates and time zones would mean time based rules are fundamentally broken in nftables. Have to create 2 rule each for lan (main) and guest network even if they do they same thing foreach zone. it would be nice to combine them into one multiple destination for example, allow port 443 from lan to wan and vpn.