
Fortgale Blog Malware Analysis Malware Analysis Fortgale blog è lo spazio di approfondimento di temi del settore cyber security con particolare focus ai cyber attack e ransomware. al link ulteriori dettagli sul tema. Malware analysis: malware analysis is the process of examining malicious software to understand its functionality, origin, and potential impact. this involves studying the malware's code, behavior, and structure to identify how it operates, how it spreads, and what kind of harm it can cause.

Malware Analysis Pdf Malware File Format Malware analysis blog has been created to share my malware analysis and reverse engineering articles, but also malware research, threat hunt, threat landscape new trends, osint, threat intelligence, malware removal, forensics articles and much much more all related to cybersecurity. Analisi del malware strelastealer, le fasi dell'attacco ed indicatori di compromissione. identificato in italia, germania, spagna e polonia. After recent online publications regarding the truebot malware (vmware, bleeping and thn), we have decided to contributing with our analysis of this potential new threat. at the end, you will find the indicators of compromise and a yara rule to identify it. Truebot malware analysis (16 06 2023) after recent online publications regarding the truebot malware (vmware, bleeping and thn), we […].
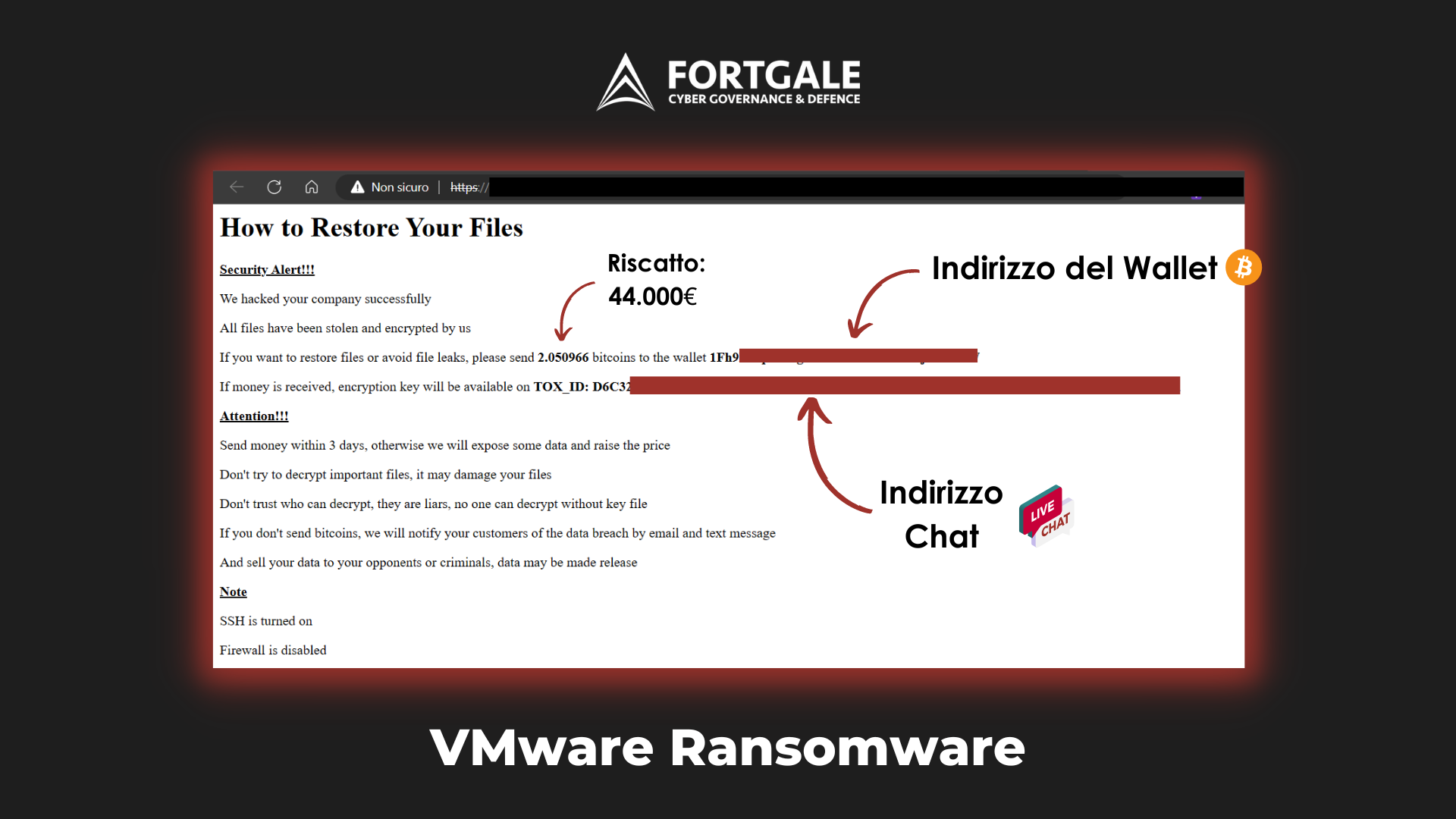
Fortgale Blog Server Vmware Esxi Ransomware Attacks In Italy After recent online publications regarding the truebot malware (vmware, bleeping and thn), we have decided to contributing with our analysis of this potential new threat. at the end, you will find the indicators of compromise and a yara rule to identify it. Truebot malware analysis (16 06 2023) after recent online publications regarding the truebot malware (vmware, bleeping and thn), we […]. In april 2021, an unidentified gold southfield operator carried out a ransomware attack against a european company. the initial access is performed by gold cabin, an access broker, that deploys iceid (bokbot), a remote access tool (rat) malware [link]. once inside the company, the access broker passes privileges to the main operator who deploys the revil ransomware. this threat actor uses. Fortgale has been tracking an italian threat actor, internally dubbed as nebula broker, since march 2022. the actor uses self made malware (brokerloader) to compromise italian systems. further analysis revealed that the attacker has been operating since the end of 2020. although this threat is not well known, the number of compromises is particularly extensive. indeed, fortgale has observed.

Digital Malware Analysis V2 Pdf Malware Virtual Machine In april 2021, an unidentified gold southfield operator carried out a ransomware attack against a european company. the initial access is performed by gold cabin, an access broker, that deploys iceid (bokbot), a remote access tool (rat) malware [link]. once inside the company, the access broker passes privileges to the main operator who deploys the revil ransomware. this threat actor uses. Fortgale has been tracking an italian threat actor, internally dubbed as nebula broker, since march 2022. the actor uses self made malware (brokerloader) to compromise italian systems. further analysis revealed that the attacker has been operating since the end of 2020. although this threat is not well known, the number of compromises is particularly extensive. indeed, fortgale has observed.

Strelastealer Malware Analysis
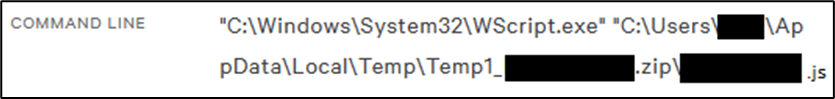
Strelastealer Malware Analysis