
Handling Collisions In A Hash Table By Jon Sy Chan Medium By using a good hash function, hashing can work well. under reasonable assumptions, the average time required to search for an element in a hash table is o (1). Separate chaining is a collision handling technique. separate chaining is one of the most popular and commonly used techniques in order to handle collisions. in this article, we will discuss about what is separate chain collision handling technique, its advantages, disadvantages, etc. there are mainly two methods to handle collision: separate chaining open addressing in this article, only.

Handling Collisions In A Hash Table By Jon Sy Chan Medium In continuation to my data structure series, this article will cover hash tables in data structure, the fundamental operations of hash…. Learn how to handle collisions in java hash tables with this guide. explore separate chaining and open addressing techniques for efficient data storage. Collisions are a major issue in hash tables and require resolution strategies. 🛠️ collision resolution methods there are two primary techniques to resolve collisions: 1️⃣ separate. Probability of hash table collisions let’s explore how birthday paradox works with hash tables and what is the probability of collisions in a hash table. is it like 25% probability for a 25% filled hashtable? let’s find out. m is the number of locations in the hashtable and n is the number of items to be inserted.

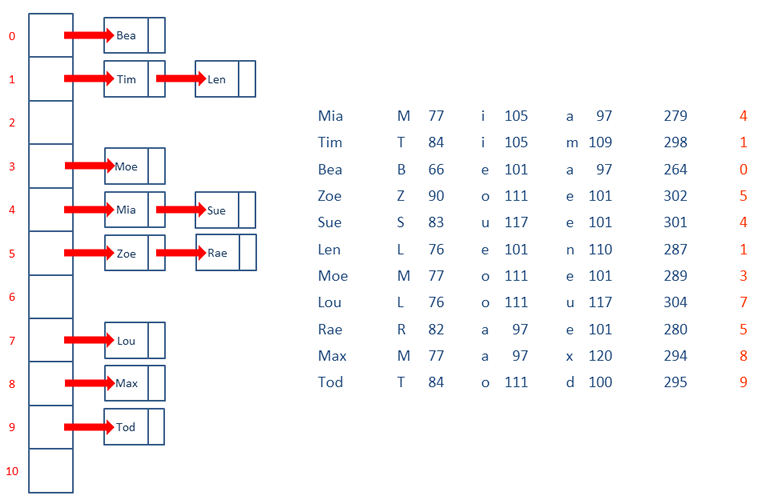
Handling Collisions In A Hash Table By Jon Sy Chan Medium Collisions are a major issue in hash tables and require resolution strategies. 🛠️ collision resolution methods there are two primary techniques to resolve collisions: 1️⃣ separate. Probability of hash table collisions let’s explore how birthday paradox works with hash tables and what is the probability of collisions in a hash table. is it like 25% probability for a 25% filled hashtable? let’s find out. m is the number of locations in the hashtable and n is the number of items to be inserted. The key serves as the input for the hash function. hash function: this is a special algorithm that transforms the key into a fixed size integer value, known as the hash index. ideally, the hash function should distribute keys uniformly across the available slots in the hash table to minimize collisions. Hash tables deal with collisions in one of two ways. option 1: by having each bucket contain a linked list of elements that are hashed to that bucket. this is why a bad hash function can make lookups in hash tables very slow. option 2: if the hash table entries are all full then the hash table can increase the number of buckets that it has and then redistribute all the elements in the table.
Collisions In Hash Table Prompts Stable Diffusion Online The key serves as the input for the hash function. hash function: this is a special algorithm that transforms the key into a fixed size integer value, known as the hash index. ideally, the hash function should distribute keys uniformly across the available slots in the hash table to minimize collisions. Hash tables deal with collisions in one of two ways. option 1: by having each bucket contain a linked list of elements that are hashed to that bucket. this is why a bad hash function can make lookups in hash tables very slow. option 2: if the hash table entries are all full then the hash table can increase the number of buckets that it has and then redistribute all the elements in the table.
Hash Table Collisions Computer Science Bytescomputer Science Bytes