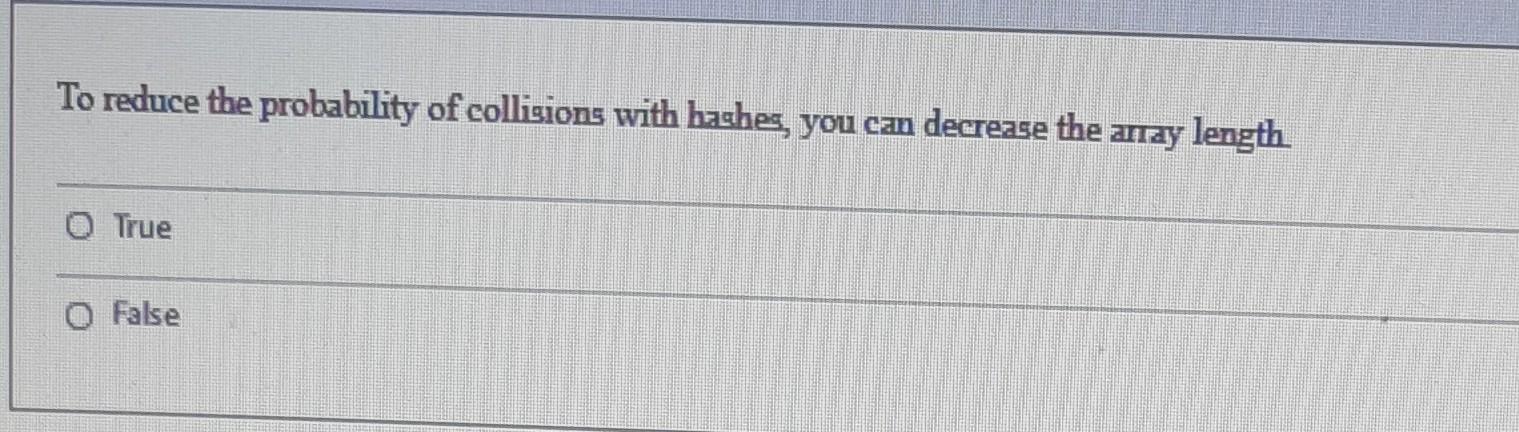
Solved To Reduce The Probability Of Collisions With Hashes Chegg Hash collisions can be unavoidable depending on the number of objects in a set and whether or not the bit string they are mapped to is long enough in length. when there is a set of n objects, if n is greater than | r |, which in this case r is the range of the hash value, the probability that there will be a hash collision is 1, meaning it is guaranteed to occur. [4] another reason hash. Hash collisions: understanding the fundamentals what is a hash collision? a hash collision occurs when two different inputs produce the same hash output when processed through a hash function. due to the pigeonhole principle (where we're mapping an infinite input space to a finite output space), collisions are mathematically inevitable the question is not if they exist, but how hard they are.

Number Of Collisions Related To The Size Of Hashes Each Line In hashing, hash functions were used to generate hash values. the hash value is used to create an index for the keys in the hash table. the hash function may return the same hash value for two or more keys. when two or more keys have the same hash value, a collision happens. to handle this collision, we use collision resolution techniques. If we have a "perfect" hash function with output size n, and we have p messages to hash (individual message length is not important), then probability of collision is about p2 2n 1 (this is an approximation which is valid for "small" p, i.e. substantially smaller than 2n 2). 1.3. collisions in hashing # in computer science, hash functions assign a code called a hash value to each member of a set of individuals. it’s important that each individual be assigned a unique value. if two individuals are assigned the same value, there is a collision, and this causes trouble in identification. yet it is cumbersome to keep track of which hash values have and have not been. Hash collision what is a hash collision? it’s a case when two different keys have the same hash value. mathematically, h(k1) = h(k2) when k1 ≠ k2 why is this a problem?.

Hash Collisions In Computer Security The Silicon Underground 1.3. collisions in hashing # in computer science, hash functions assign a code called a hash value to each member of a set of individuals. it’s important that each individual be assigned a unique value. if two individuals are assigned the same value, there is a collision, and this causes trouble in identification. yet it is cumbersome to keep track of which hash values have and have not been. Hash collision what is a hash collision? it’s a case when two different keys have the same hash value. mathematically, h(k1) = h(k2) when k1 ≠ k2 why is this a problem?. While hash tables offer o (1) average time complexity for operations like insertion and search, they come with a common challenge: hash collisions. in this blog, we’ll dive into what hash collisions are, how they occur, and the techniques used to handle them effectively. Learn about collision in hashing, including types of collisions and methods to resolve them effectively.
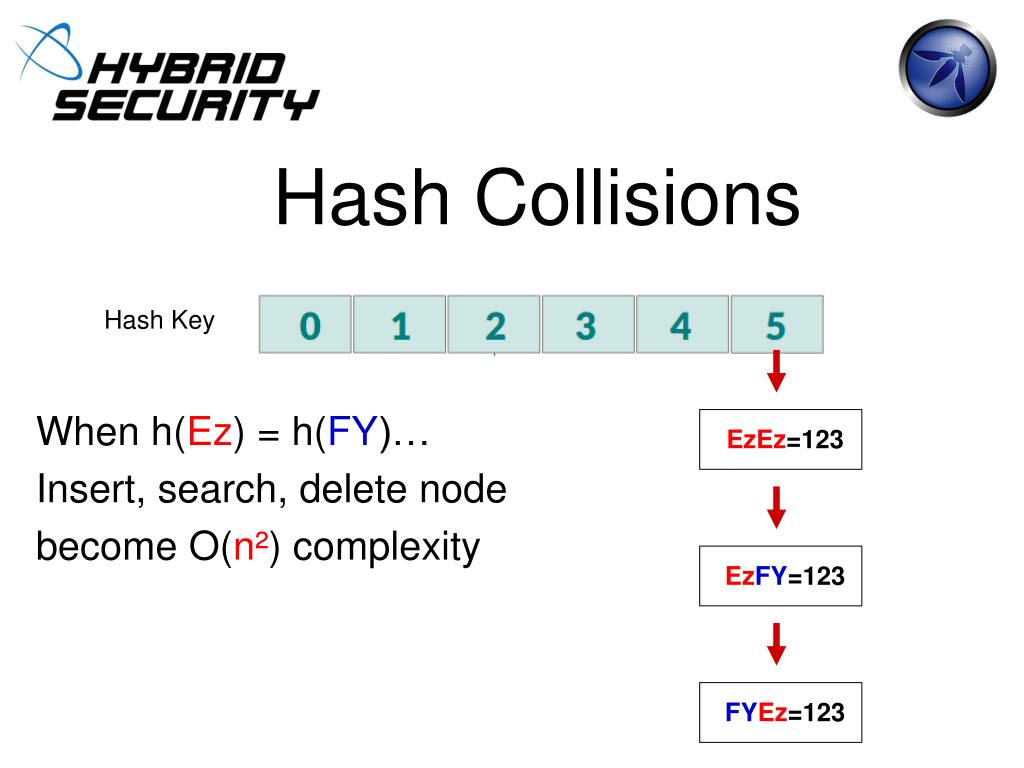
Ppt Layer 7 Dos Hash Collisions Powerpoint Presentation Free While hash tables offer o (1) average time complexity for operations like insertion and search, they come with a common challenge: hash collisions. in this blog, we’ll dive into what hash collisions are, how they occur, and the techniques used to handle them effectively. Learn about collision in hashing, including types of collisions and methods to resolve them effectively.

Solution Types Of Hashing Collisions Studypool