
How Malware Bypasses Detection Tools Cio Insight The average cost to detect and contain one security breach because of the failure of malware detection is about $62,000. this means organizations could have spent $3.2 million to deal with the security breach due to web borne malware. How evasive malware is made, and how it bypasses edr’s detections. introduction to malware development.
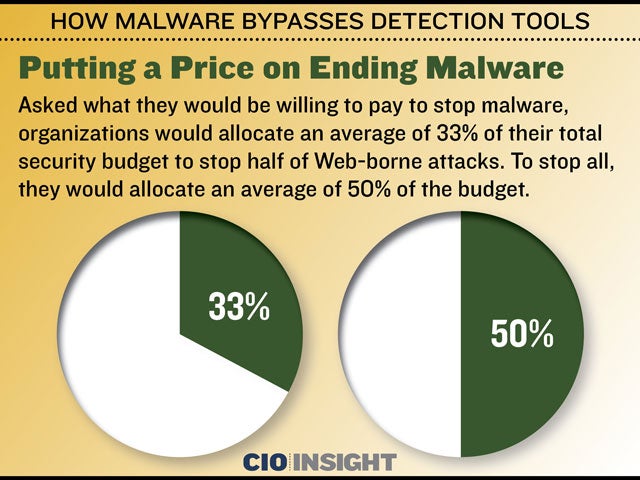
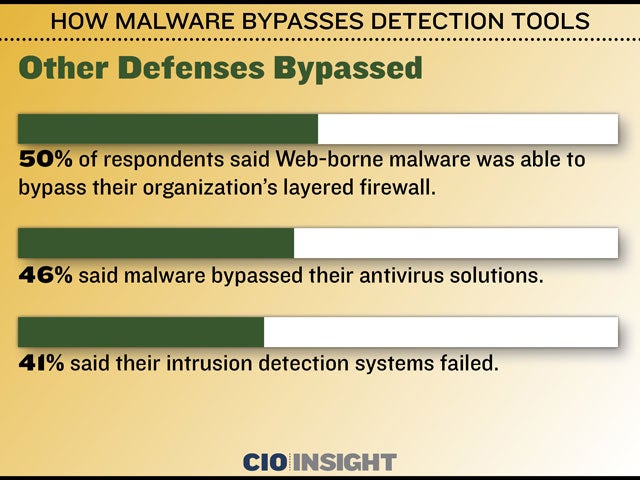
How Malware Bypasses Detection Tools Cio Insight These delivery mechanisms share three core attributes: trust mimicry user initiation platform agnosticism because the user initiates the action (by clicking a link, downloading a file or responding to a prompt) the attack often bypasses traditional perimeter defenses and evades early detection by endpoint tools. A lack of integration hampers threat detection lack of automation integration and workflow between security and response are hindering organizations’ ability to prevent, detect and respond to cyber threats. Explore the growing threat of web borne malware and how it easily bypasses detection tools. dive into the statistics with a detailed bar chart analysis. In any.run’s sandbox, these operations are surfaced automatically, revealing how the malware bypasses file locks and avoids detection. this level of insight allows soc teams to quickly identify advanced techniques that traditional tools might overlook.
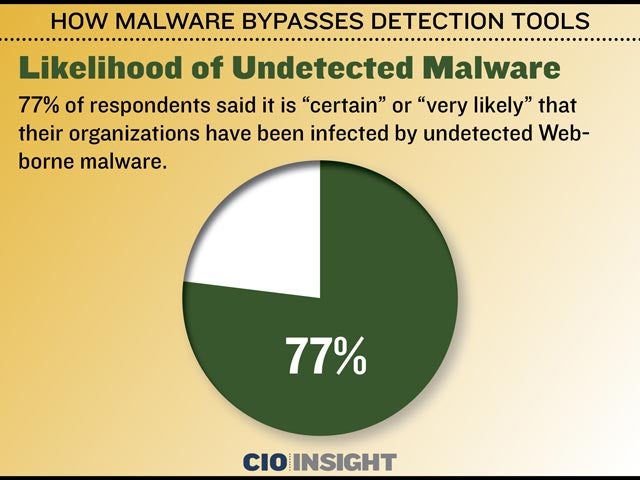
How Malware Bypasses Detection Tools Cio Insight Explore the growing threat of web borne malware and how it easily bypasses detection tools. dive into the statistics with a detailed bar chart analysis. In any.run’s sandbox, these operations are surfaced automatically, revealing how the malware bypasses file locks and avoids detection. this level of insight allows soc teams to quickly identify advanced techniques that traditional tools might overlook. Examining how persistent malware conceals itself in cloud vms, bypasses cloud security tools, and ways to strengthen defenses. Cio insight offers thought leadership and best practices in the it security and management industry while providing expert recommendations on software solutions for it leaders.
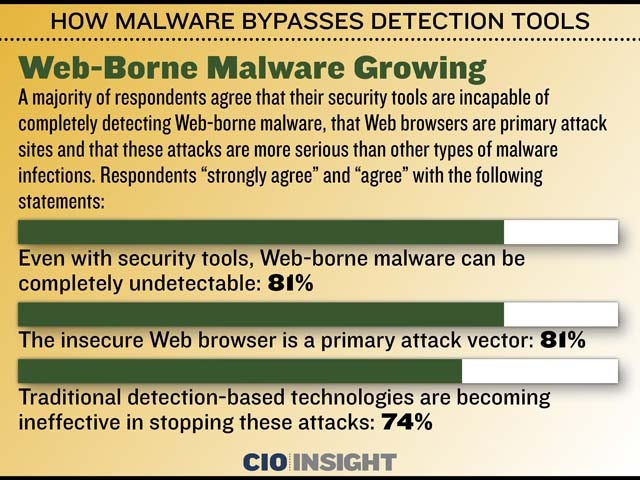
How Malware Bypasses Detection Tools Cio Insight Examining how persistent malware conceals itself in cloud vms, bypasses cloud security tools, and ways to strengthen defenses. Cio insight offers thought leadership and best practices in the it security and management industry while providing expert recommendations on software solutions for it leaders.
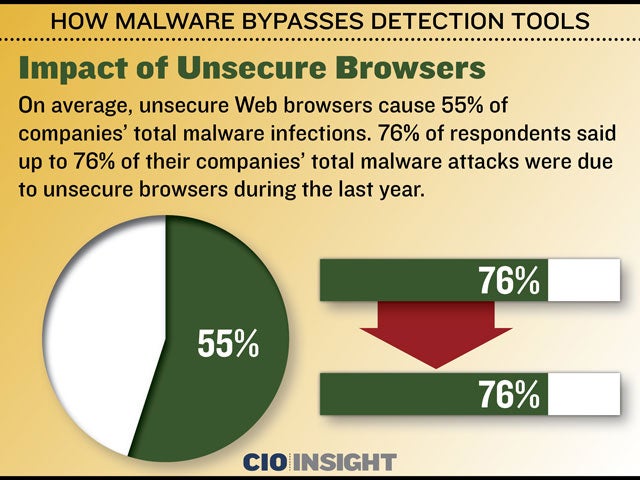
How Malware Bypasses Detection Tools Cio Insight
How Malware Bypasses Detection Tools Cio Insight