
How To Assess Your Company S Security Maturity Delap Cybersecurity guards against threats to your business or organization. it's important to assess the current state of your security maturity. That is why we use maturity models to measure and benchmark clients’ information security maturity during assessment consulting engagements. as described in our security assessments, we can assess an entire security program, or specific security domains. we calibrate our recommendations against the maturity level of the organization in each area.

How To Assess Your Company S Security Maturity Delap Learn how to enhance your cybersecurity posture with our step by step maturity assessment and measurement guide. Learn how to assess your cybersecurity maturity with frameworks like nist csf and c2m2 mil. discover key maturity models and their features. One way to do that is by evaluating your company’s cybersecurity posture. a strong posture is a great first line of defense for keeping your organization safe against known and unknown risks. if you're ready to see where your organization stands, dig into how to assess and improve your security posture below. Use a cybersecurity maturity assessment questionnaire to evaluate your organization’s security posture. learn key domains, best practices, and action steps.

How To Assess Your Company S Security Maturity Delap One way to do that is by evaluating your company’s cybersecurity posture. a strong posture is a great first line of defense for keeping your organization safe against known and unknown risks. if you're ready to see where your organization stands, dig into how to assess and improve your security posture below. Use a cybersecurity maturity assessment questionnaire to evaluate your organization’s security posture. learn key domains, best practices, and action steps. The security maturity assessment aims to determine the maturity level of your cybersecurity based on the cmm model, to help decide on the next steps to raise your cyber resilience. Conclusion assessing the cybersecurity maturity of your organization is essential to ensuring robust defenses against the myriad of cyber threats faced in the digital age. by understanding the current posture and working to improve it diligently, organizations can better protect their critical assets.
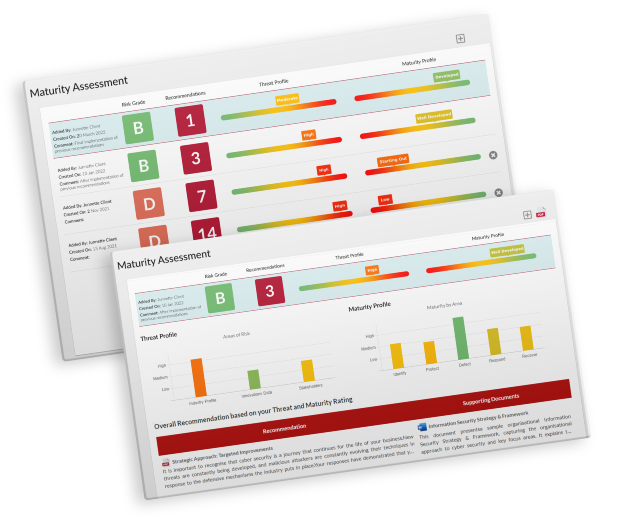
Trustwave Security Colony Maturity Assessment The security maturity assessment aims to determine the maturity level of your cybersecurity based on the cmm model, to help decide on the next steps to raise your cyber resilience. Conclusion assessing the cybersecurity maturity of your organization is essential to ensuring robust defenses against the myriad of cyber threats faced in the digital age. by understanding the current posture and working to improve it diligently, organizations can better protect their critical assets.

Trustwave Security Colony Maturity Assessment

How To Assess Security Maturity And Make Improvements Security