
How To Mitigate The Security Risks Of Cloud Computing How to avoid increased security vulnerabilities in cloud computing? in this insightful video, we delve into essential strategies to avoid increased security. Applications on the cloud are prone to numerous security issues. read on to learn about the most common cloud computing vulnerabilities and discover effective strategies to prevent them.

Melt Away Cloud Security Risks With A Refreshing Vulnerabilities Audit Explore the security risks associated with cloud computing and learn how to mitigate them. understand common threats and best practices for securing your cloud infrastructure. Understand the key security issues in cloud computing, including data breaches, misconfigurations, and compliance challenges. discover strategies and best practices to mitigate risks and protect your cloud infrastructure effectively. Mitigating cloud vulnerabilities while careful cloud adoption can enhance an organization’s security posture, cloud services can introduce risks that organizations should understand and address both during the procurement process and while operating in the cloud. fully evaluating security implications when shifting resources to the cloud will help ensure continued resource availability and. Security risks in cloud computing, like data breaches and misconfigurations, can put your business at risk. learn the top challenges and how to stay protected.

Cloud Computing Security Risks And Solutions Article View Cynf Mitigating cloud vulnerabilities while careful cloud adoption can enhance an organization’s security posture, cloud services can introduce risks that organizations should understand and address both during the procurement process and while operating in the cloud. fully evaluating security implications when shifting resources to the cloud will help ensure continued resource availability and. Security risks in cloud computing, like data breaches and misconfigurations, can put your business at risk. learn the top challenges and how to stay protected. Today’s cloud security landscape cloud security has upended traditional approaches to vulnerability management. historically, on premises environments provided clear perimeters and static infrastructure, making it easier to enforce security measures and track vulnerabilities. in the cloud, where ephemeral workloads and distributed architectures dominate, securing dynamic attack surfaces. Mitigating risks and cloud vulnerabilities: best practices for cloud security knowing about different types of vulnerability in cloud computing is crucial, but what’s even more important is understanding how to protect our digital assets from these threats. let’s break down the best practices for cloud security and see how emerging technologies change this realm. regular security audits.

Cloud Computing Security Risks In 2020 How To Avoid Them Today’s cloud security landscape cloud security has upended traditional approaches to vulnerability management. historically, on premises environments provided clear perimeters and static infrastructure, making it easier to enforce security measures and track vulnerabilities. in the cloud, where ephemeral workloads and distributed architectures dominate, securing dynamic attack surfaces. Mitigating risks and cloud vulnerabilities: best practices for cloud security knowing about different types of vulnerability in cloud computing is crucial, but what’s even more important is understanding how to protect our digital assets from these threats. let’s break down the best practices for cloud security and see how emerging technologies change this realm. regular security audits.

Dealing With Cloud Security Vulnerabilities Infosys Bpm
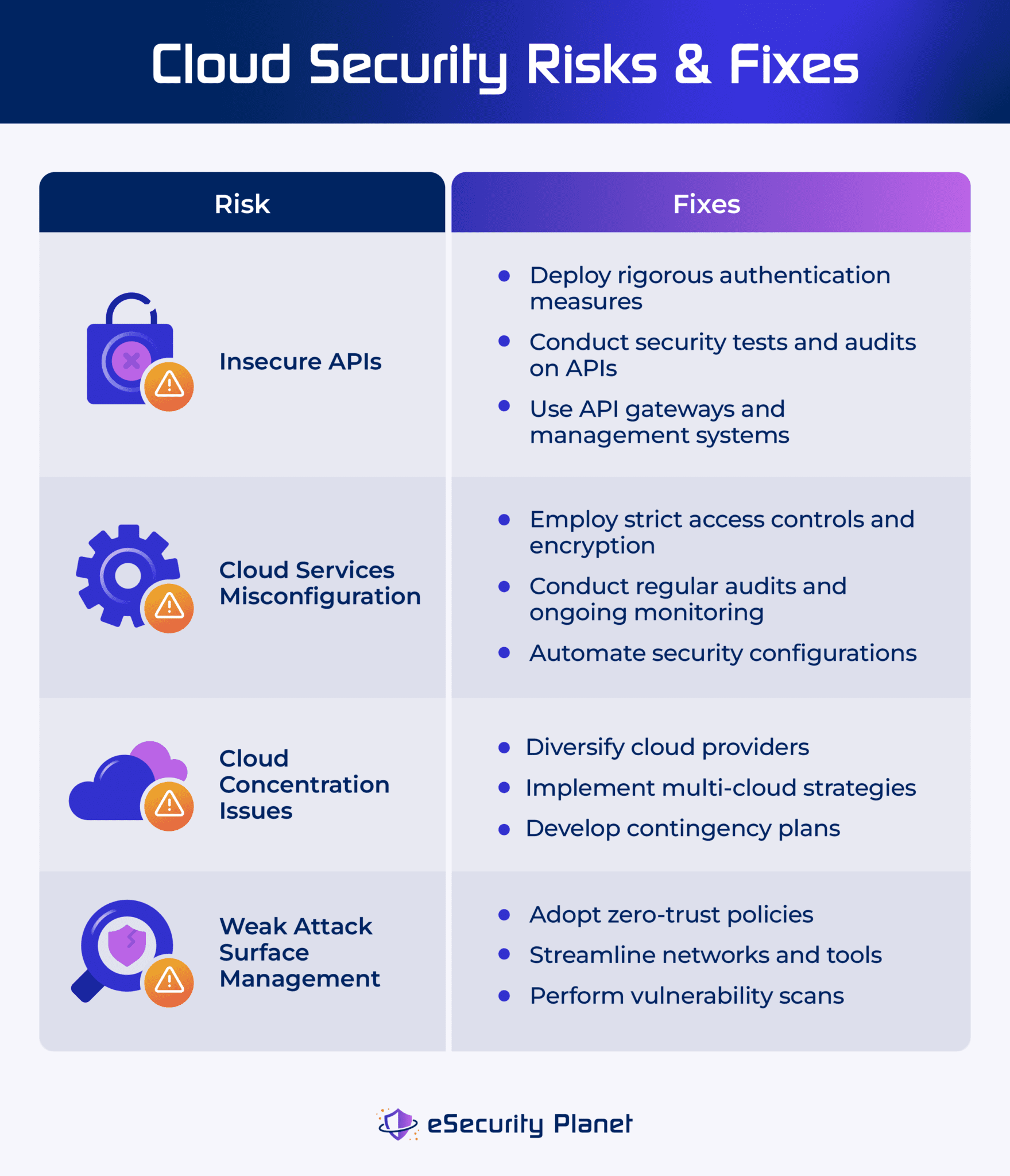
Top Cloud Security Issues Threats Risks Challenges Solutions
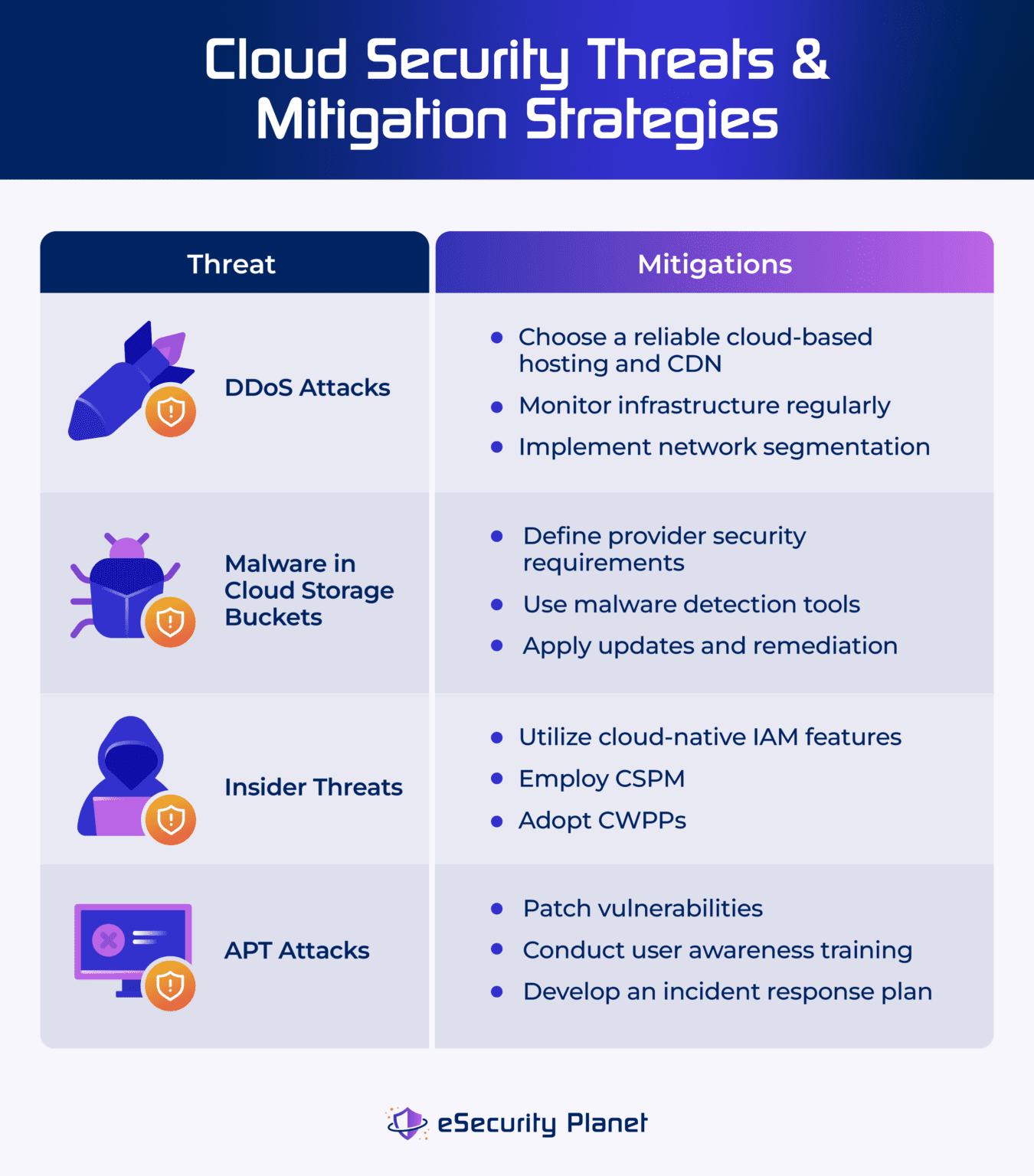
Top Cloud Security Issues Threats Risks Challenges Solutions