Managing Risks Vulnerabilities Io How to identify vulnerabilities in your go application ardan labs 14.7k subscribers 33. Learn how to secure your go applications by identifying and addressing common security vulnerabilities. explore mitigation techniques and best practices to safeguard your code.

What Are Web Application Vulnerabilities And How To Prevent Risks Cybri Burp suite can be used to identify different types of vulnerabilities, such as sql injection or cross site scripting, by testing the web application beyond its graphical user interface (gui). Reassess the security vulnerability after changes to an application like patch application or upgrade to higher version. what are the sources to identify security vulnerability within an application?. Checkmarx static application security testing (sast) offers comprehensive source code scanning to identify vulnerabilities early in the development cycle. the tool is ideal for enterprises looking to integrate security into their development lifecycle. Web application penetration testing finds security flaws in your apps & infrastructure before attackers do. discover its process to identify & fix vulnerabilities.

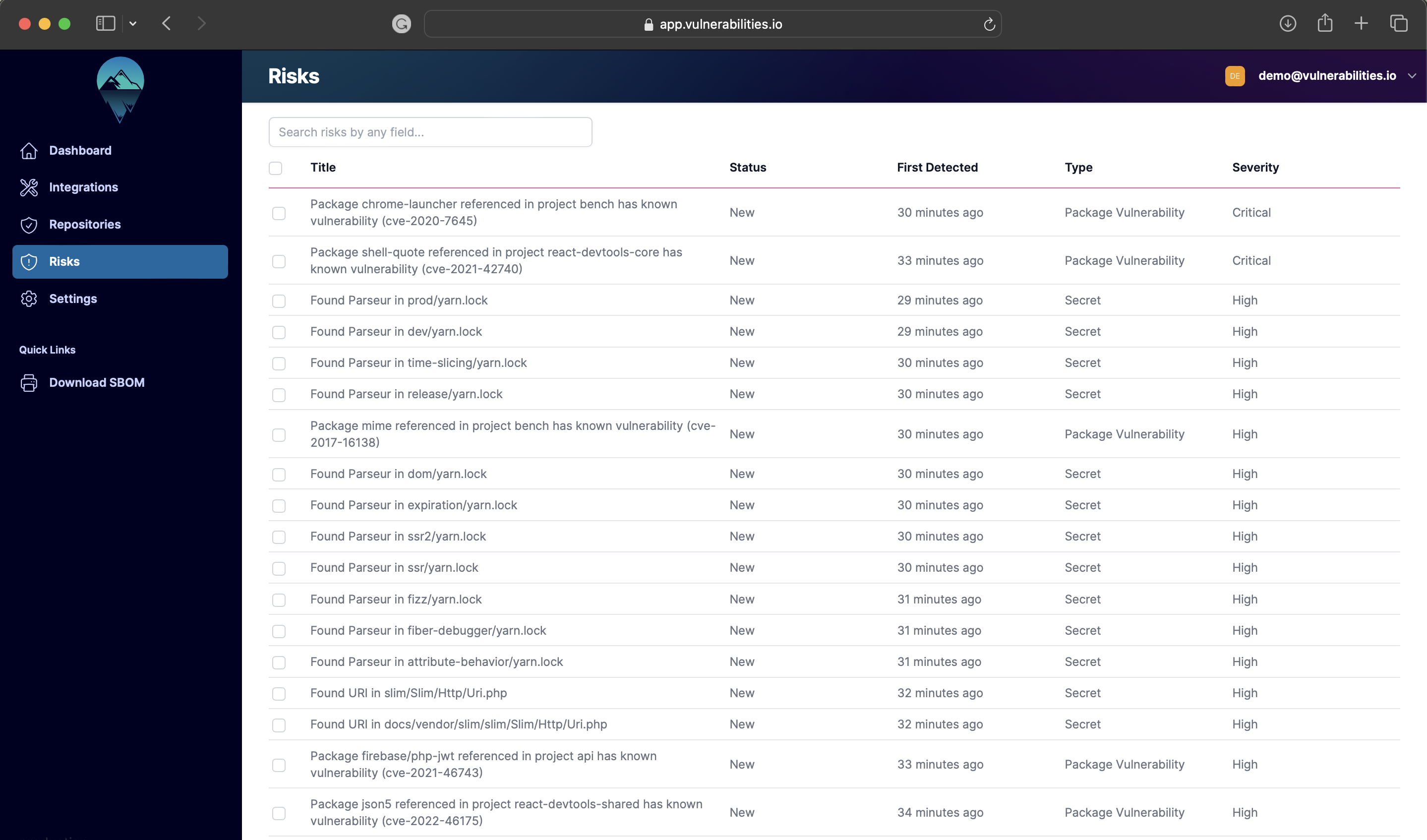
The 16 Most Common Web Application Vulnerabilities Explained Wpscan Checkmarx static application security testing (sast) offers comprehensive source code scanning to identify vulnerabilities early in the development cycle. the tool is ideal for enterprises looking to integrate security into their development lifecycle. Web application penetration testing finds security flaws in your apps & infrastructure before attackers do. discover its process to identify & fix vulnerabilities. Dynamic application security testing (dast) aims to spot application security vulnerabilities in real time while the application is active. it is a security measure within contemporary software delivery pipelines. within this article, we will take you on a comprehensive journey through the dynamic application security testing process, step by step. Identifying system, network, and application weaknesses is a critical step in securing your it infrastructure. proactively finding and addressing these vulnerabilities can help prevent cyberattacks, data breaches, and system failures. here’s a comprehensive guide on how to identify weaknesses across these areas: 1.

The 16 Most Common Web Application Vulnerabilities Explained Wpscan Dynamic application security testing (dast) aims to spot application security vulnerabilities in real time while the application is active. it is a security measure within contemporary software delivery pipelines. within this article, we will take you on a comprehensive journey through the dynamic application security testing process, step by step. Identifying system, network, and application weaknesses is a critical step in securing your it infrastructure. proactively finding and addressing these vulnerabilities can help prevent cyberattacks, data breaches, and system failures. here’s a comprehensive guide on how to identify weaknesses across these areas: 1.