
Cloud Computing Security Risks And Risk Management Strategies We’ll cover what’s included in cloud risk management, common security risks, and what to do to keep vulnerabilities low over time. cloud risk management is a process used to find, evaluate, and reduce the risks of using cloud computing services. A leading national provider of hybrid it solutions, tierpoint helps organizations drive performance and manage risk. no u.s. provider comes close to matching tierpoint’s unique combination of thousands of clients; more than 40 edge capable data centers and 8 multitenant cloud pods coast to coast; and a comprehensive portfolio of cloud.
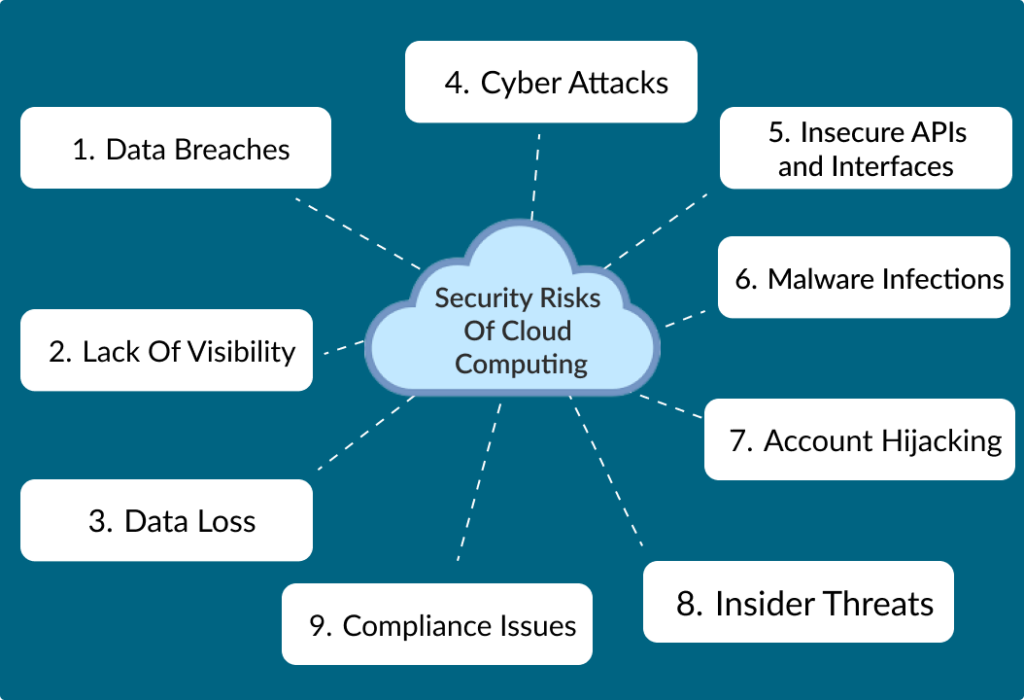
What Are The Security Risks Of Cloud Computing Leed Uncover the 17 critical security risks of cloud computing in 2025 and explore best practices to secure your cloud environment effectively. Tierpoint helps organizations like yours reduce risk through proactive monitoring of data, applications, and infrastructure. as your trusted cloud and managed services partner, we are already managing your critical systems and infrastructure. Get our 9 best tips for improving your cloud computing security in order to protect your valuable and sensitive business data!. As the use of cloud technology grows, the security risks also increase. organizations must proactively approach cloud security by implementing thorough strategies to reduce these threats effectively. businesses can take advantage of cloud computing benefits while upholding strong security by using: 1. technical controls 2. policies 3. employee.

What Are The Top Security Risks In Cloud Computing Jelvix Get our 9 best tips for improving your cloud computing security in order to protect your valuable and sensitive business data!. As the use of cloud technology grows, the security risks also increase. organizations must proactively approach cloud security by implementing thorough strategies to reduce these threats effectively. businesses can take advantage of cloud computing benefits while upholding strong security by using: 1. technical controls 2. policies 3. employee. A cloud native application protection platform (cnapp) consolidates and simplifies the management of various public cloud security tools, allowing you to view the state of security in your environment through a single pane of glass. Planning of security in cloud computing : as security is a major concern in cloud implementation, so an organization have to plan for security based on some factors like below represents the three main factors on which planning of cloud security depends. resources that can be moved to the cloud and test its sensitivity risk are picked. the type of cloud is to be considered. the risk in the.
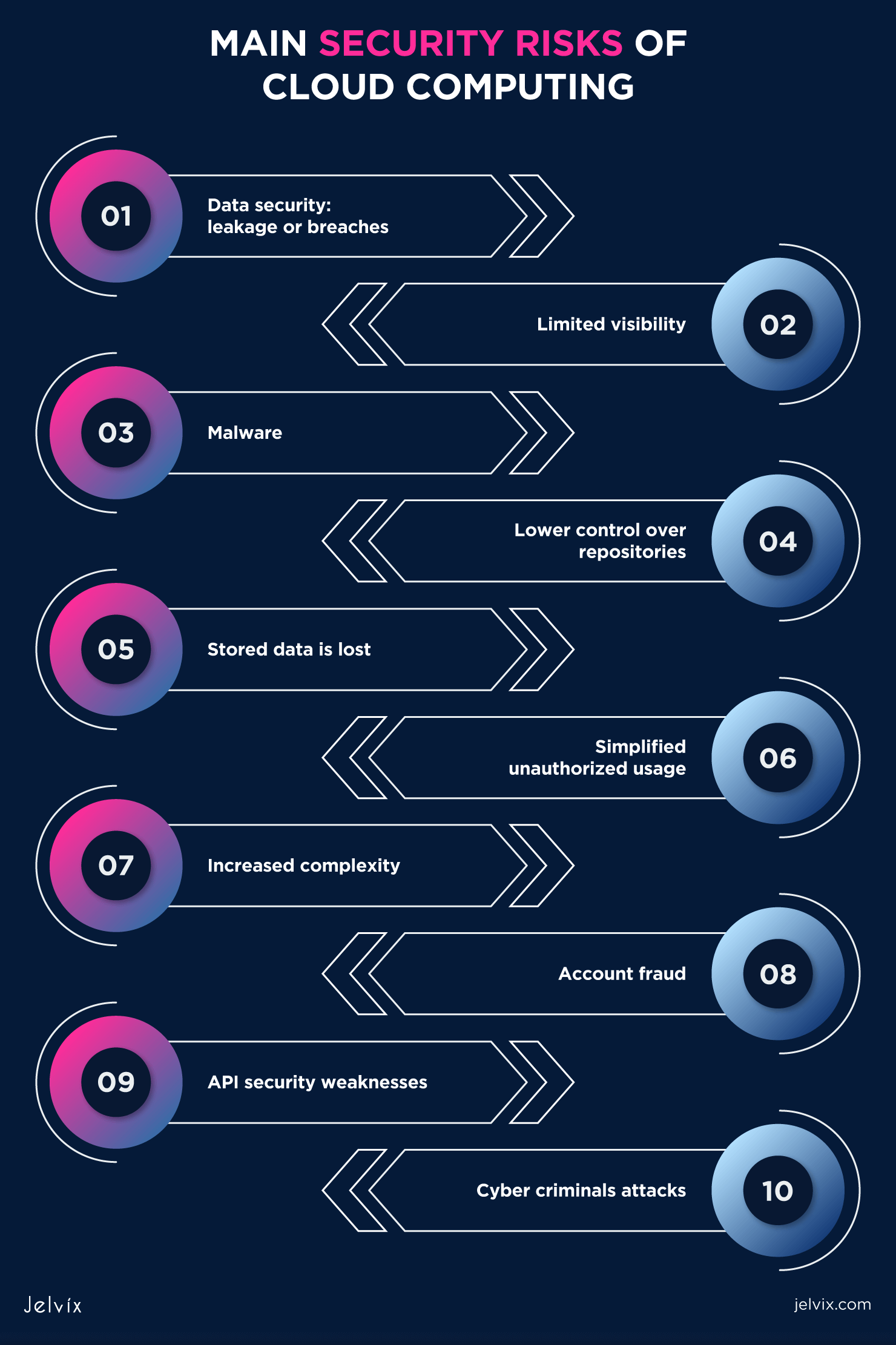
What Are The Top Security Risks In Cloud Computing Jelvix A cloud native application protection platform (cnapp) consolidates and simplifies the management of various public cloud security tools, allowing you to view the state of security in your environment through a single pane of glass. Planning of security in cloud computing : as security is a major concern in cloud implementation, so an organization have to plan for security based on some factors like below represents the three main factors on which planning of cloud security depends. resources that can be moved to the cloud and test its sensitivity risk are picked. the type of cloud is to be considered. the risk in the.
What Are The Top Security Risks In Cloud Computing Jelvix