
Identity Verification Regulations Technology Gov Capital Bring required documents federal information processing standards publication 201 3, or fips 201 3, provides the regulations for personal identity verification requirements. you must have two physical and current forms of identification: at least one must be a primary form of id. This document establishes a standard for a personal identity verification (piv) system that meets the control and security objectives of homeland security presidential directive 12. it is based on secure and reliable forms of identity credentials issued by the federal government to its employees and contractors. these credentials are used by mechanisms that authenticate individuals who require.

Identity Verification Benefits Technology Gov Capital Homeland security presidential directive 12 (hspd 12) establishes policy for a common identification standard for federal employees and contractors and subsequently directed the government wide use of personal identity identification (piv) cards. on june 30, 2008, in executive order 13467 (pdf file), “reforming processes related to suitability for government employment, fitness for. Identity verification is therefore crucial for safeguarding both individuals and organizations. it helps prevent identity theft, financial loss, reputational damage, and legal issues by ensuring only authorized individuals can access protected resources. Dhs s&t has announced the second phase of the remote identity validation rally (rivr), a series of challenges hosted by dhs s&t where the tech industry is invited to test, refine, and improve its id verification technology. Identity verification gsa needs to address nist guidance, technical issues, and lessons learned what gao found login.gov collects a variety of personally identifiable information (pii) from users accessing government applications and websites.

The Evolution Of Identity Verification Technology Exclusive Guide Dhs s&t has announced the second phase of the remote identity validation rally (rivr), a series of challenges hosted by dhs s&t where the tech industry is invited to test, refine, and improve its id verification technology. Identity verification gsa needs to address nist guidance, technical issues, and lessons learned what gao found login.gov collects a variety of personally identifiable information (pii) from users accessing government applications and websites. Business drivers and program authority federal identity, credential, and access management (ficam), is an enterprise level framework comprised of programs, processes, technologies, and personnel. ficam is used to create trusted digital identity representations for individuals and non person entities (npes) (e.g., applications and systems); and to bind identities to credentials for use within. Federal ciso council icam subcommittee use this interagency forum as a resource for identity management, secure access, authentication, authorization, credentials, privileges, and access lifecycle management. the subcommittee aligns identity management activities of the federal government and supports collaborative governmentwide efforts.

Shufti Electronic Identity Verification Technology And Regulations Business drivers and program authority federal identity, credential, and access management (ficam), is an enterprise level framework comprised of programs, processes, technologies, and personnel. ficam is used to create trusted digital identity representations for individuals and non person entities (npes) (e.g., applications and systems); and to bind identities to credentials for use within. Federal ciso council icam subcommittee use this interagency forum as a resource for identity management, secure access, authentication, authorization, credentials, privileges, and access lifecycle management. the subcommittee aligns identity management activities of the federal government and supports collaborative governmentwide efforts.
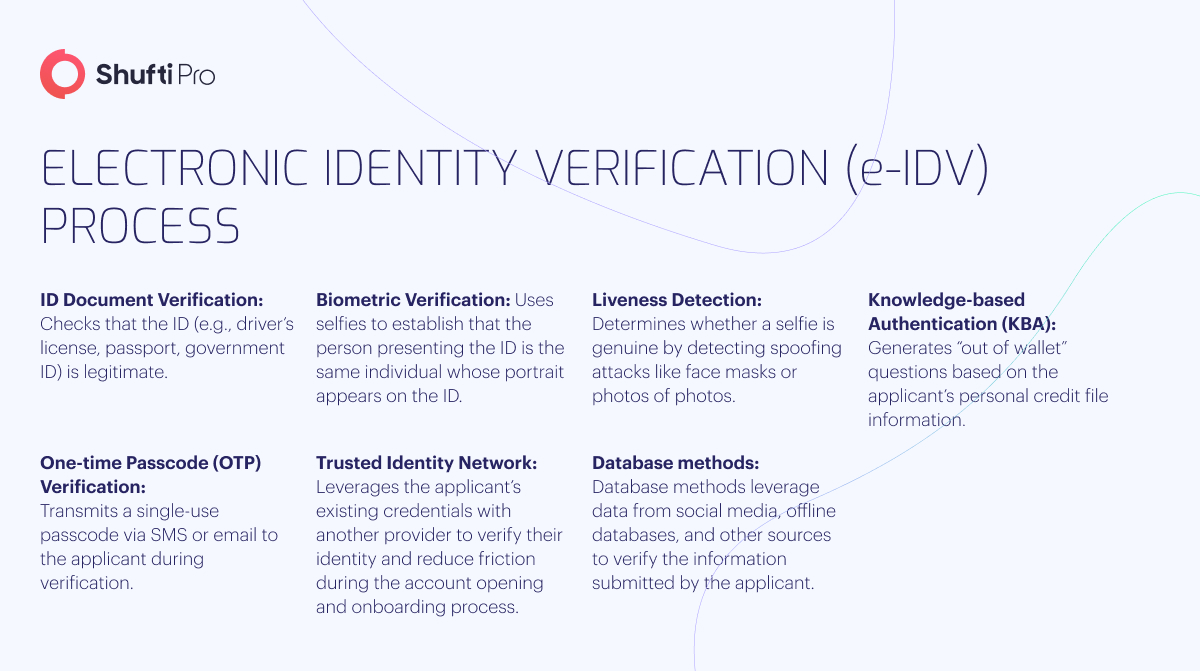
Shufti Electronic Identity Verification Technology And Regulations