
Ids Ips And Their Role In Cybersecurity Hacker Combat Ids, ips and their role in cybersecurity in today’s world, when it security teams perpetually face threats of data breaches, compliance fines etc, ids and ips systems are of great help. these systems help enterprise it departments cover important areas of their cybersecurity strategies. Conclusion both intrusion detection systems (ids) and intrusion prevention systems (ips) play crucial roles in a comprehensive cybersecurity strategy. ids focuses on identifying and alerting administrators about abnormal network activity, while ips provides proactive defense by blocking malicious activities in real time.

Beginners Guide To Ids And Ips Hackercool Magazine This blog will explore the most common cyber attacks that ids can detect and ips can prevent, providing insights into how these systems protect modern networks. Intrusion detection and prevention systems (ids ips) act as cybersecurity watchdogs, monitoring and blocking threats in real time. learn how they protect networks from modern attacks. Photo by markus spiske on unsplash intrusion detection systems (ids) and intrusion prevention systems (ips) play a critical role in protecting modern organizations against the ever increasing threat of cyber attacks. these security solutions monitor network traffic and alert security personnel of any unusual activity that may indicate a potential threat. in this article, we will explore the. This article explores the significance of ids and ips in network security, their differences, functionalities, deployment strategies, and the future of these systems in the context of modern cybersecurity challenges.
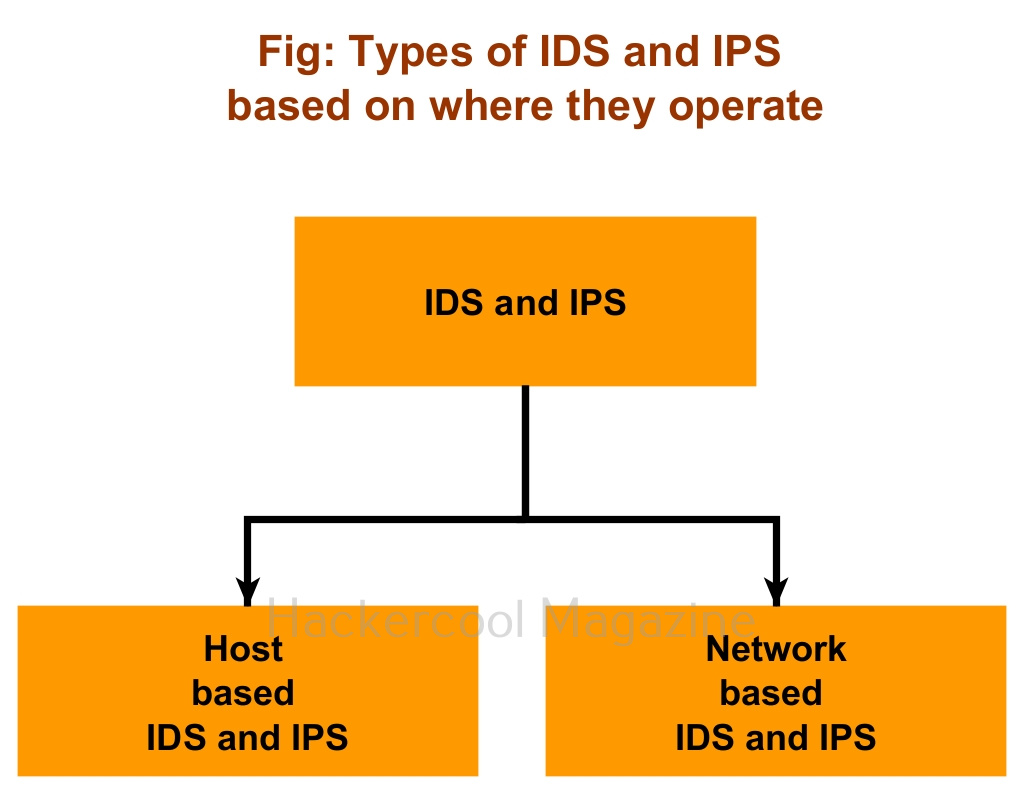
Beginners Guide To Ids And Ips Hackercool Magazine Photo by markus spiske on unsplash intrusion detection systems (ids) and intrusion prevention systems (ips) play a critical role in protecting modern organizations against the ever increasing threat of cyber attacks. these security solutions monitor network traffic and alert security personnel of any unusual activity that may indicate a potential threat. in this article, we will explore the. This article explores the significance of ids and ips in network security, their differences, functionalities, deployment strategies, and the future of these systems in the context of modern cybersecurity challenges. Learn the key differences between ids and ips, how they work, and why they are essential for protecting networks from cyber threats. According to cybersecurity researchers gartner, ips definitions have blurred to sometimes include ids capabilities for threat detection too. but at their core, the two systems have significant differences. [1] now let‘s break down how ids and ips work… examining ids and ips processes: detection vs prevention intrusion detection systems like snort or suricata work by continually analyzing.

Ids Vs Ips Exploring The Evolution Of Intrusion Detection And Prevention Learn the key differences between ids and ips, how they work, and why they are essential for protecting networks from cyber threats. According to cybersecurity researchers gartner, ips definitions have blurred to sometimes include ids capabilities for threat detection too. but at their core, the two systems have significant differences. [1] now let‘s break down how ids and ips work… examining ids and ips processes: detection vs prevention intrusion detection systems like snort or suricata work by continually analyzing.

Ids Vs Ips What S The Difference

Ids Vs Ips What S The Difference Rokacom