
Mastering 4 Stages Of Malware Analysis Pdf Malware Intelligence Guide to malware analysis. here we discuss how to conduct malware analysis along with importance, 4 stages and use cases. Combining malware analysis stages the process of examining malicious software involves several stages, which could be listed in the order of increasing complexity and represented as a pyramid. however, viewing these stages as discrete and sequential steps over simplifies the steps malware analysis process.
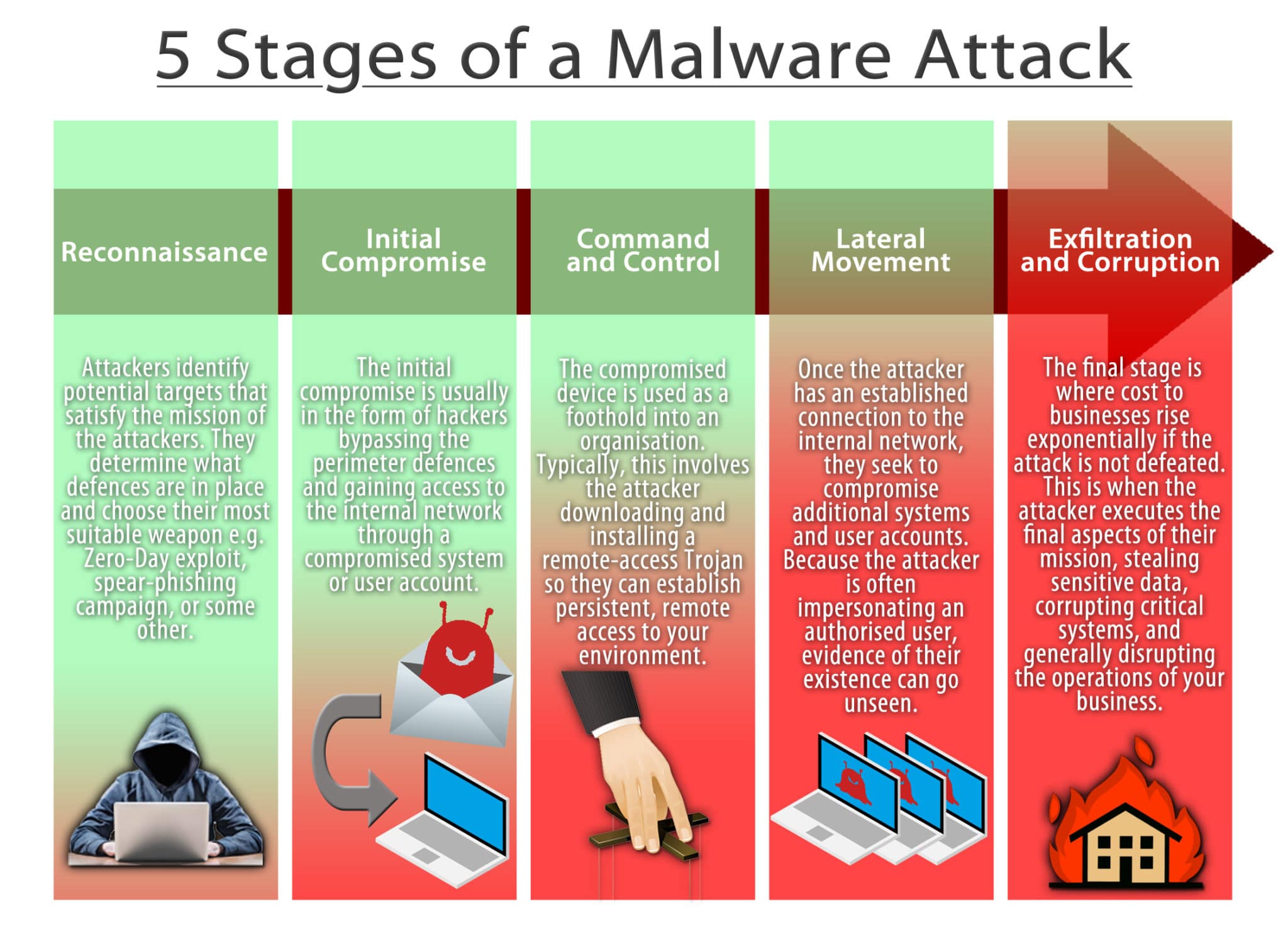
Malware Lifecycle Tesrex Learn what malware analysis is and how it can improve your enterprise security. discover the stages of malware analysis to better understand its benefits. Malware analysis: definition, use cases, stages updated on october 11, 2022, by xcitium malware analysis deals with the study of how malware functions and about the possible outcomes of infection of a given specific malware. it is important for any it security expert to know that malware can have different types of functions as they are of a type like worms, viruses, spyware, trojan horses. Malware analysis is the process of understanding the behavior and purpose of a malware sample to prevent future cyberattacks. Into two categor targeted malware. four general stages of malware analysis are manual code reversing, interactive behavior analysis, static properties analysis, and automated analysis. e paper goes over bas advanced are covered and cuckoo is talked about to cover automated analysis.
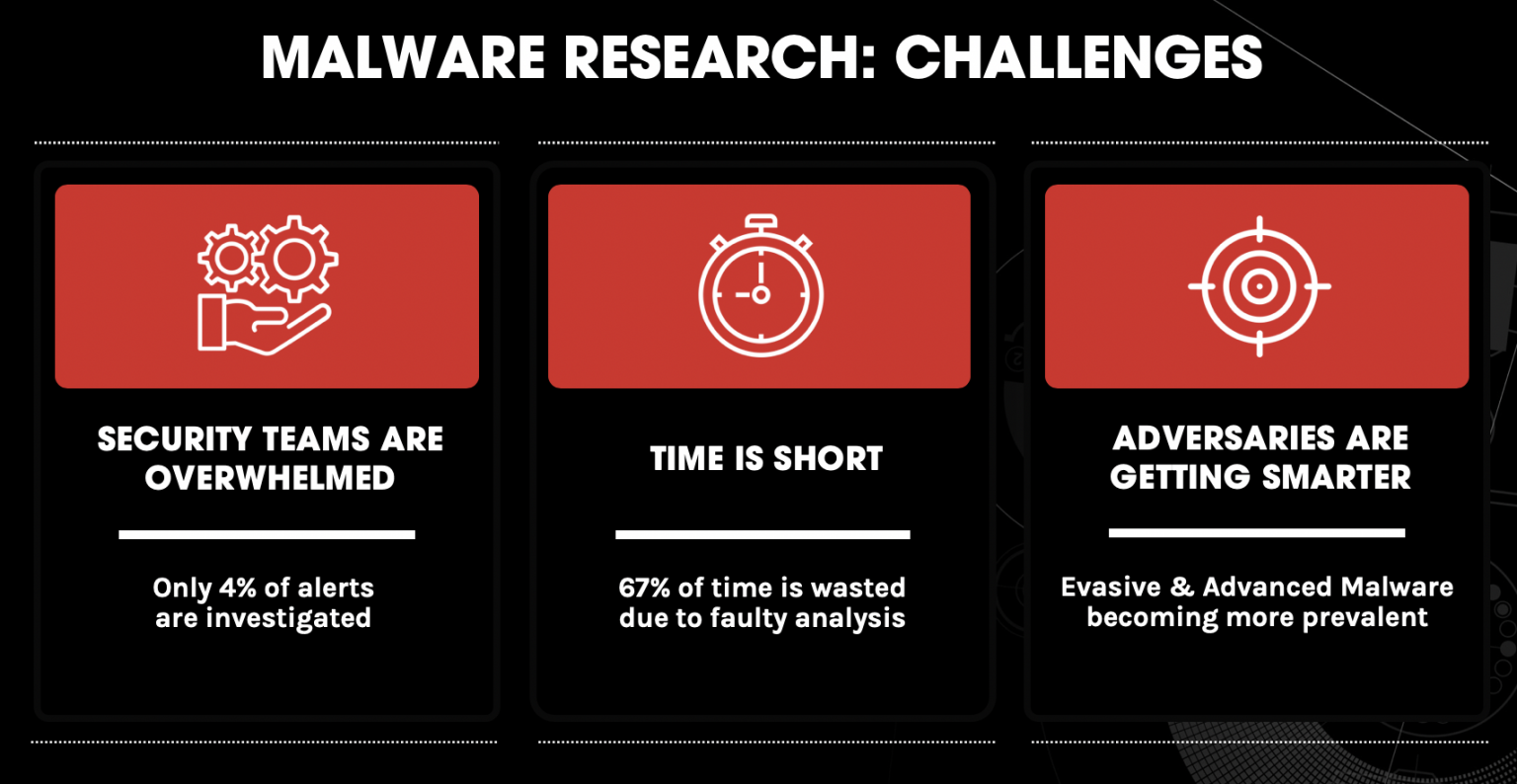
Malware Analysis Steps Examples Crowdstrike Malware analysis is the process of understanding the behavior and purpose of a malware sample to prevent future cyberattacks. Into two categor targeted malware. four general stages of malware analysis are manual code reversing, interactive behavior analysis, static properties analysis, and automated analysis. e paper goes over bas advanced are covered and cuckoo is talked about to cover automated analysis. Malware analysis is all about understanding how malware works, the different types it comes in, how it’s used in real situations, and the tools needed to investigate and analyze it thoroughly. it helps uncover the behavior, purpose, and potential impact of malicious software. this guide will walk you through the key aspects of malware analysis, its benefits, stages, types, and the tools used. Malware includes virus, ransomware, rootkits, trojan and a malware attack can adversely affect a business and its operations. appropriate security measures must be put in place by businesses to malware analysis tools as an incident response plan that will chart a proper procedure to ensure there are the recovery time and reduced costs.

Malware Analysis Steps Examples Crowdstrike Malware analysis is all about understanding how malware works, the different types it comes in, how it’s used in real situations, and the tools needed to investigate and analyze it thoroughly. it helps uncover the behavior, purpose, and potential impact of malicious software. this guide will walk you through the key aspects of malware analysis, its benefits, stages, types, and the tools used. Malware includes virus, ransomware, rootkits, trojan and a malware attack can adversely affect a business and its operations. appropriate security measures must be put in place by businesses to malware analysis tools as an incident response plan that will chart a proper procedure to ensure there are the recovery time and reduced costs.

Malware Analysis Steps Examples Crowdstrike
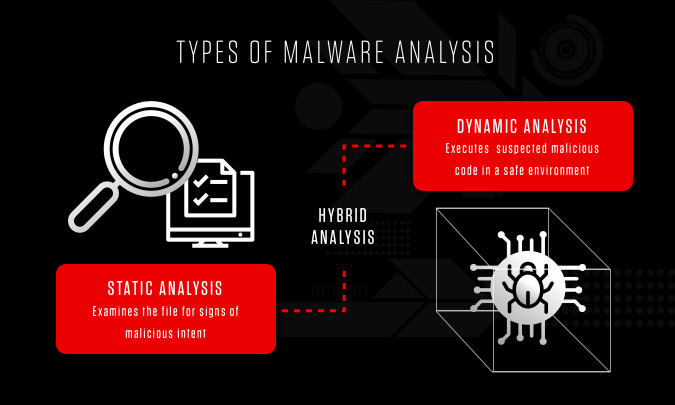
Malware Analysis Steps Examples Crowdstrike
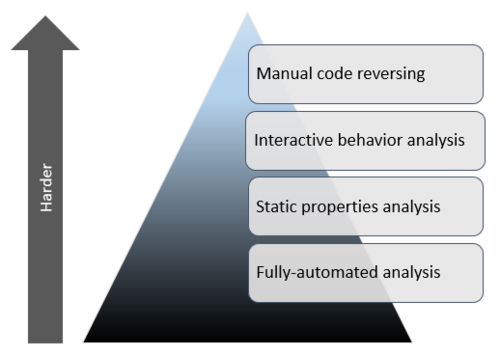
Mastering 4 Stages Of Malware Analysis