
Github Mchowdhury2010 Malware Analysis Home Lab Analyse suspicious files, domains, ips and urls to detect malware and other breaches, automatically share them with the security community. Browse malware samplesmalwarebazaar database you are browsing the malware sample database of malwarebazaar. if you would like to contribute malware samples to the corpus, you can do so through either using the web upload or the api.
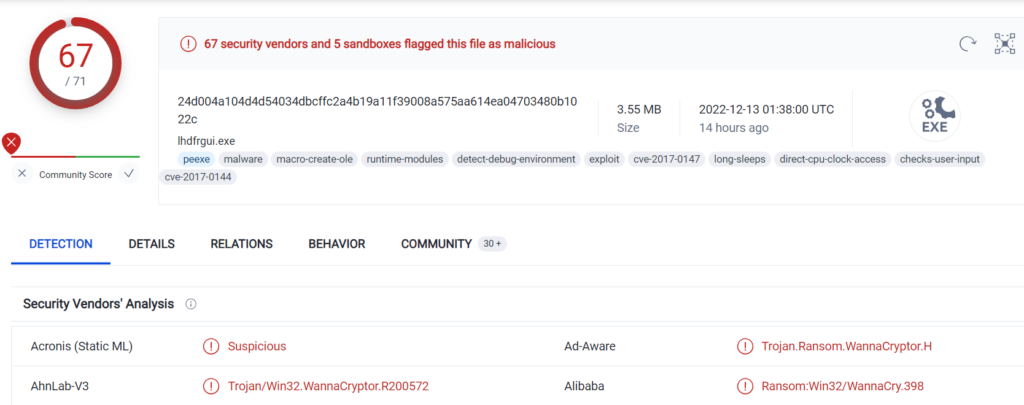
Basics Of Malware Analysis Part 1 Anoobishacking Submit malware for free analysis with falcon sandbox and hybrid analysis technology. hybrid analysis develops and licenses analysis tools to fight malware. Interactive malware hunting service. live testing of most type of threats in any environments. no installation and no waiting necessary. Free, open source and multi platform static malware analysis. Submit malware for analysis on this next gen malware assessment platform. filescan gmbh develops and licenses technology to fight malware with a focus on indicator of compromise (ioc) extraction at scale.

Malware Analysis A Beginner S Guide To Malware Analysis By Rewa Free, open source and multi platform static malware analysis. Submit malware for analysis on this next gen malware assessment platform. filescan gmbh develops and licenses technology to fight malware with a focus on indicator of compromise (ioc) extraction at scale. Cloud based malware analysis service. take your information security to the next level. analyze suspicious and malicious activities using our innovative tools. Malware analysis is a critical skill in cybersecurity, enabling professionals to detect, dissect, and mitigate malicious software. this guide explores yara rules, sigma detection, and hex analysis using tools like detect it easy (die) to identify malware behavior in binary (.bin), dynamic link library (.dll), and executable (.exe) files.

Flare Vm Windows Malware Analysis By Whoami Medium Cloud based malware analysis service. take your information security to the next level. analyze suspicious and malicious activities using our innovative tools. Malware analysis is a critical skill in cybersecurity, enabling professionals to detect, dissect, and mitigate malicious software. this guide explores yara rules, sigma detection, and hex analysis using tools like detect it easy (die) to identify malware behavior in binary (.bin), dynamic link library (.dll), and executable (.exe) files.

Free Automated Malware Analysis Service Powered By Falcon Sandbox
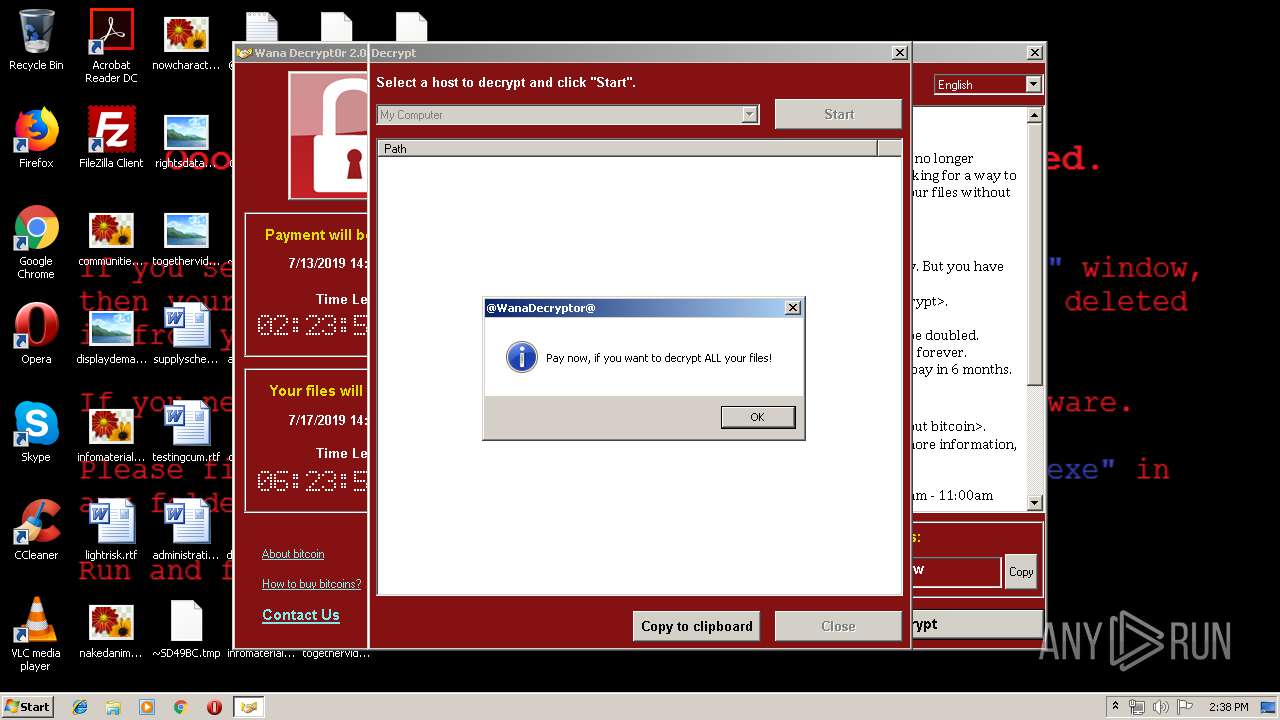
Analysis
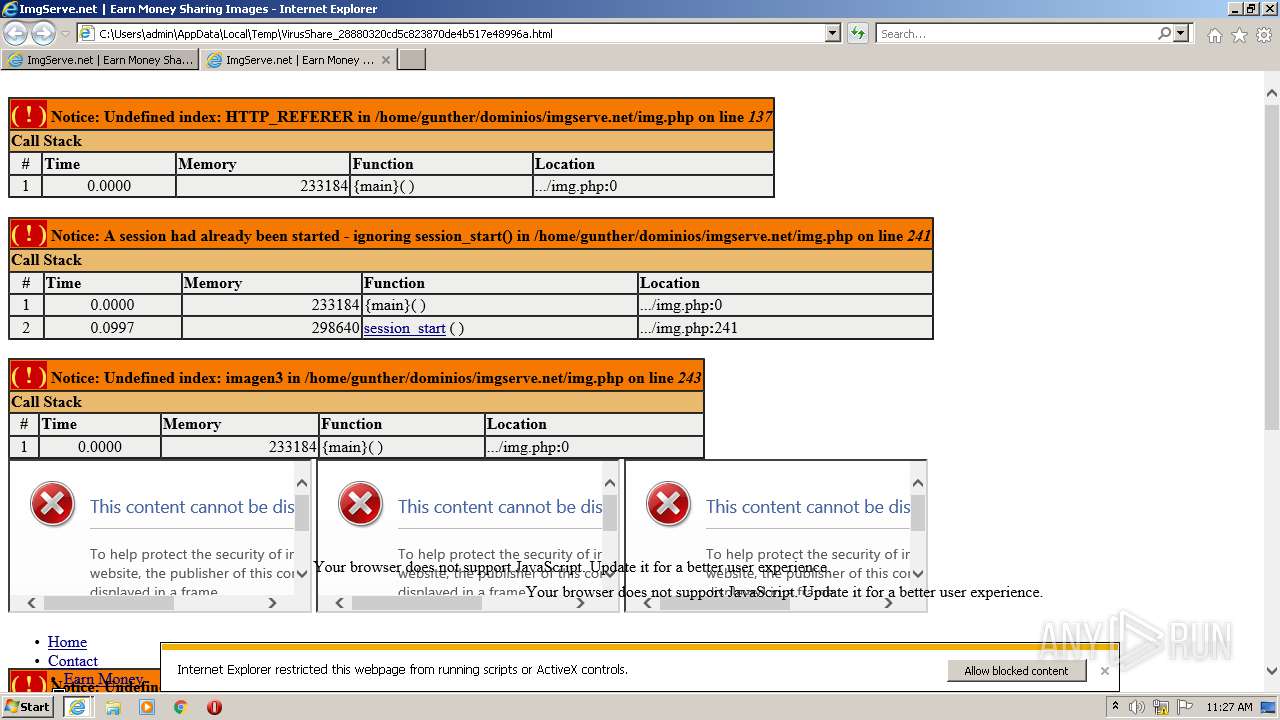
Analysis Virusshare 28880320cd5c823870de4b517e48996a Md5