
Malware Analysis Tools 25 Best Malware Analysis Tools And Techniques Online sandbox report for d4ac4633ebd6440fa397b84f1bc94a3c.7z, verdict: no threats detected. Interactive malware hunting service. live testing of most type of threats in any environments. no installation and no waiting necessary.

Github Mchowdhury2010 Malware Analysis Home Lab Uncover it is a simple to use malware analyzer that can return the configuration (such as c2) of a file statically. The d4ac4633ebd6440fa397b84f1bc94a3c.7z file analysis updated on 2024 12 18 (3 months ago) checked by online virus scanner. Virustotal assistant bot offers a platform for users to interact with virustotal's threat intelligence suite and explore artifact related information effectively. This is a free malware analysis service for the community that detects and analyzes unknown threats using a unique hybrid analysis technology.

Windows Malware Analysis For Hedgehogs Couse Expert Training Virustotal assistant bot offers a platform for users to interact with virustotal's threat intelligence suite and explore artifact related information effectively. This is a free malware analysis service for the community that detects and analyzes unknown threats using a unique hybrid analysis technology. Malware analysis is the process of understanding the behavior and purpose of a malware sample to prevent future cyberattacks. Regular scans: run weekly system scans to detect new threats before they can cause damage. keep software updated: ensure your operating system and all applications have the latest security patches. safe browsing: avoid suspicious websites and never download software from untrusted sources.
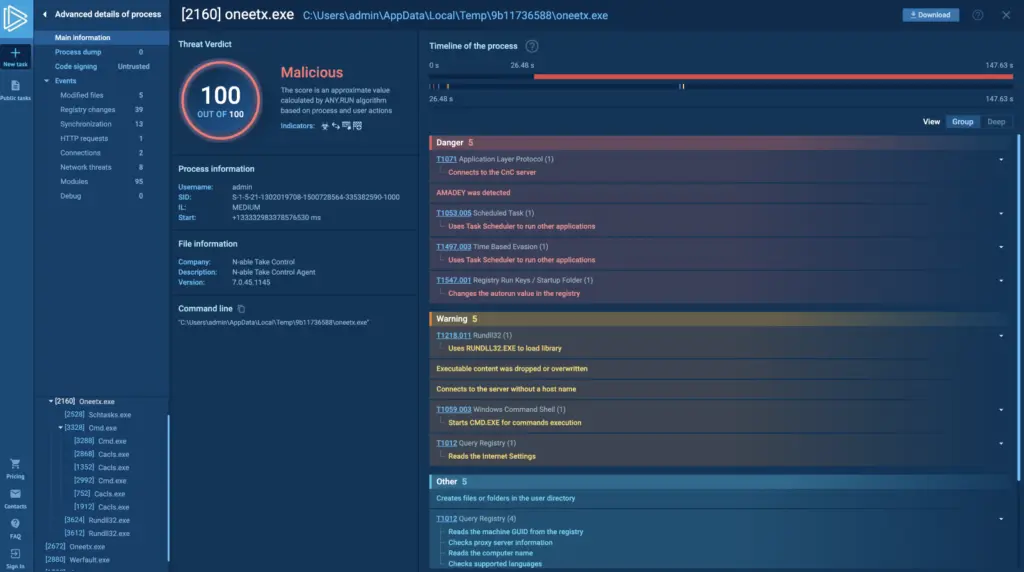
A Guide To Malware Analysis With A Sandbox Malware analysis is the process of understanding the behavior and purpose of a malware sample to prevent future cyberattacks. Regular scans: run weekly system scans to detect new threats before they can cause damage. keep software updated: ensure your operating system and all applications have the latest security patches. safe browsing: avoid suspicious websites and never download software from untrusted sources.
Malware Analysis I Detecting Indicators Of Compromise And Malicious