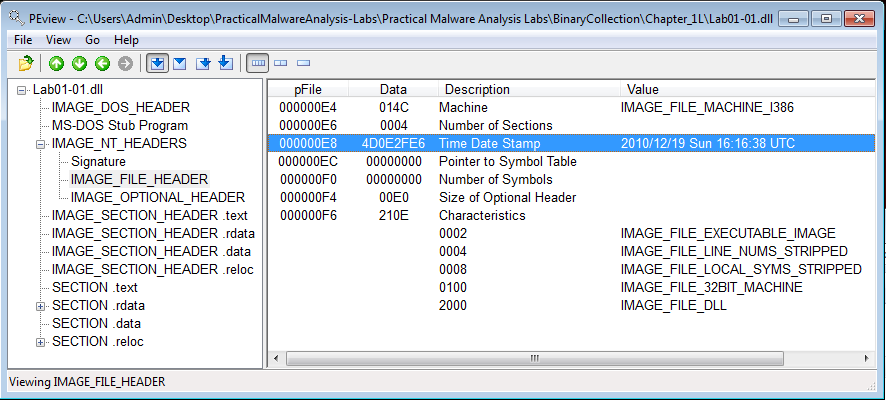
Practical Malware Analysis Lab 1 Write Up Malwarepenguin Blog Online sandbox report for documentsfolder 856491(feb03).one, verdict: malicious activity. Cisa's malware analysis service provides stakeholders a dynamic analysis of malicious code, including recommendations for malware removal and recovery activities.
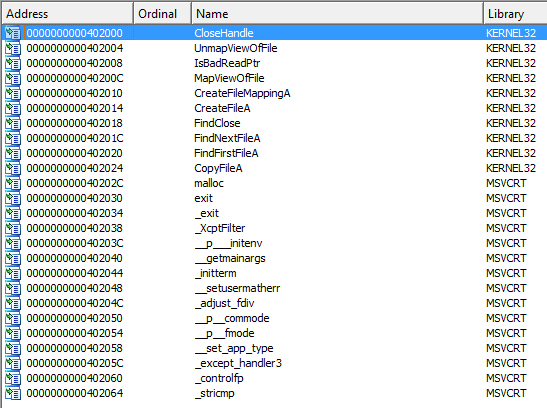
Practical Malware Analysis Lab 1 Write Up Malwarepenguin Blog Screen 10: exporting the object in the desktop for analysis. now we have the file with us what we can do is either check that file through our anti malware or navigate ourselves to virustotal (more preferable as it will show you the behavior of the file and it will be checked by the knowledge base of several anti malware. Submit malware for free analysis with falcon sandbox and hybrid analysis technology. hybrid analysis develops and licenses analysis tools to fight malware. Pcap analysis, malicious malware analysis . contribute to paras98 malicous pcap analysis development by creating an account on github. Malware analysis is the process of understanding the behavior and purpose of a malware sample to prevent future cyberattacks.

Understanding Malware Analysis Lab Setup And Research Course Hero Pcap analysis, malicious malware analysis . contribute to paras98 malicous pcap analysis development by creating an account on github. Malware analysis is the process of understanding the behavior and purpose of a malware sample to prevent future cyberattacks. Malware analysis for beginners (step by step) get familiar with industry standard tools and methodologies to identify, understand, and detect malware threats. Cloud based malware analysis service. take your information security to the next level. analyze suspicious and malicious activities using our innovative tools.
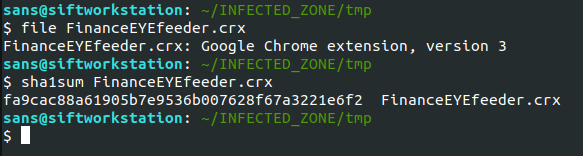
Letsdefend S Malware Analysis Suspicious Browser Extension Walk Malware analysis for beginners (step by step) get familiar with industry standard tools and methodologies to identify, understand, and detect malware threats. Cloud based malware analysis service. take your information security to the next level. analyze suspicious and malicious activities using our innovative tools.

Files Mostly Attacked During Malware Attack Ppt Example