Malware Analysis Threat Intel Uac Bypasses Learn about uac bypass methods in windows 11 that are used in modern malware and explore examples of their implementation in active threats. Jh.live anyrun ti || anyrun has just released their latest threat intelligence feature set, and it is super cool to track and hunt for malware famili.

Malicious Macro Bypasses Uac To Elevate Privilege For Fareit Malware User account control (uac) is one of the security measures introduced by microsoft to prevent malicious software from executing without the user’s knowledge. however, modern malware has found effective ways to bypass this barrier and ensure silent deployment on the host device. here are three methods commonly found in malware samples uploaded to any.run’s public submissions database. what. This cloud based platform detects malware in under 40 seconds, significantly accelerating threat analysis and reducing incident response times for soc teams. by isolating suspicious files and urls, it prevents risks to corporate infrastructure while enabling manual interaction with threats for deeper insights. Exploring windows uac bypasses: techniques and detection strategies in this research article, we will take a look at a collection of uac bypasses, investigate some of the key primitives they depend on, and explore detection opportunities. This uac bypass method, while effective, highlights the need for ongoing revision of security policies and access control implementations by microsoft. sharing and understanding these techniques is crucial to strengthening defenses against attacks that seek to exploit gaps in seemingly robust security mechanisms.
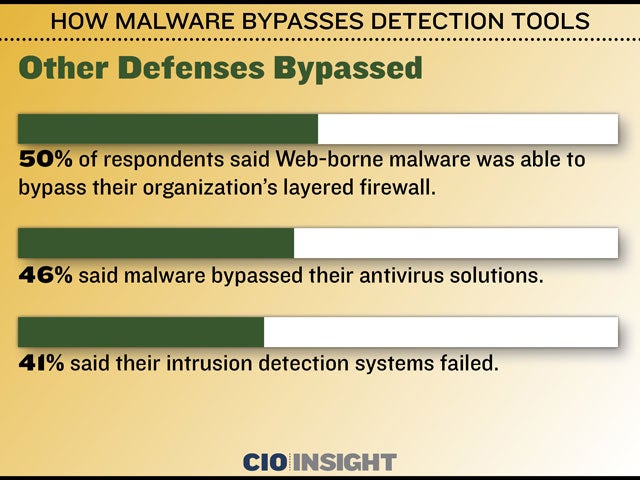
How Malware Bypasses Detection Tools Cio Insight Exploring windows uac bypasses: techniques and detection strategies in this research article, we will take a look at a collection of uac bypasses, investigate some of the key primitives they depend on, and explore detection opportunities. This uac bypass method, while effective, highlights the need for ongoing revision of security policies and access control implementations by microsoft. sharing and understanding these techniques is crucial to strengthening defenses against attacks that seek to exploit gaps in seemingly robust security mechanisms. Our interactive sandbox simplifies malware analysis of threats that target both windows and linux systems. our threat intelligence products, ti lookup, yara search, and feeds, help you find iocs or files to learn more about the threats and respond to incidents faster. Novel exploit chain enables windows uac bypass adversaries can exploit cve 2024 6769 to jump from regular to admin access without triggering uac, but microsoft says it's not really a vulnerability.

Uac Bypass Analysis Timothy S Bates Our interactive sandbox simplifies malware analysis of threats that target both windows and linux systems. our threat intelligence products, ti lookup, yara search, and feeds, help you find iocs or files to learn more about the threats and respond to incidents faster. Novel exploit chain enables windows uac bypass adversaries can exploit cve 2024 6769 to jump from regular to admin access without triggering uac, but microsoft says it's not really a vulnerability.

Malware Threat Intel Notes September 02