
Github Mchowdhury2010 Malware Analysis Home Lab Software environment set and analysis options behavior activities add for printing. Uncover it is a simple to use malware analyzer that can return the configuration (such as c2) of a file statically.
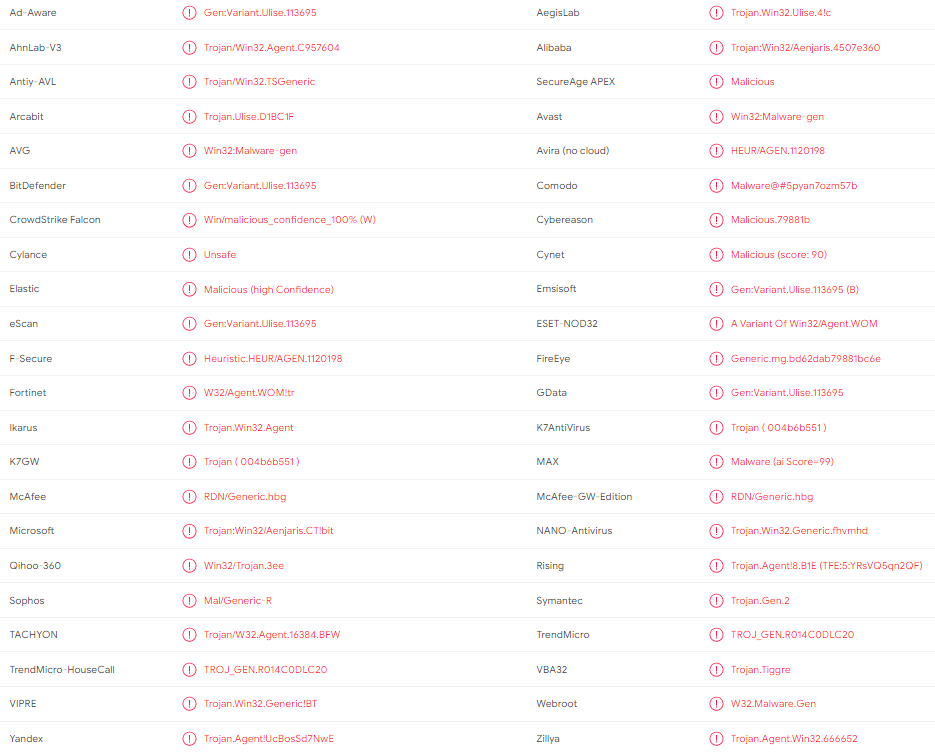
Introduction To Malware Analysis Forensicxs Deep malware analysis joe sandbox analysis reportchrome.exe (pid: 6460 cmdline: "c:\progra m files\go ogle\chrom e\applicat ion\chrome.exe" ty pe=utility utility sub type= network.mo jom wor kservice lang=en u s servic e sandbox type=none mojo pla tform chan nel handle =2164 fi eld trial handle=197 6,i,176823 0558371310 4170,17468 5743937832 15297,2621 44 disab le. Submit malware for free analysis with falcon sandbox and hybrid analysis technology. hybrid analysis develops and licenses analysis tools to fight malware. Ataware ransomware uses uac bypass using cmstplua com interface in atapiinit.exe (stage 1). it was downloaded from dropbox url when user open the malicious excel. Windows analysis report ucfcfc93cfdacefa08d2f6f82de8.dl.dropboxusercontent cd 0 get ciqj4bpzvuqptxdpg5ill7uwtot9hsz8rrdatmy9j xvpaqdzn7j3bgmqnv2jvtdo.
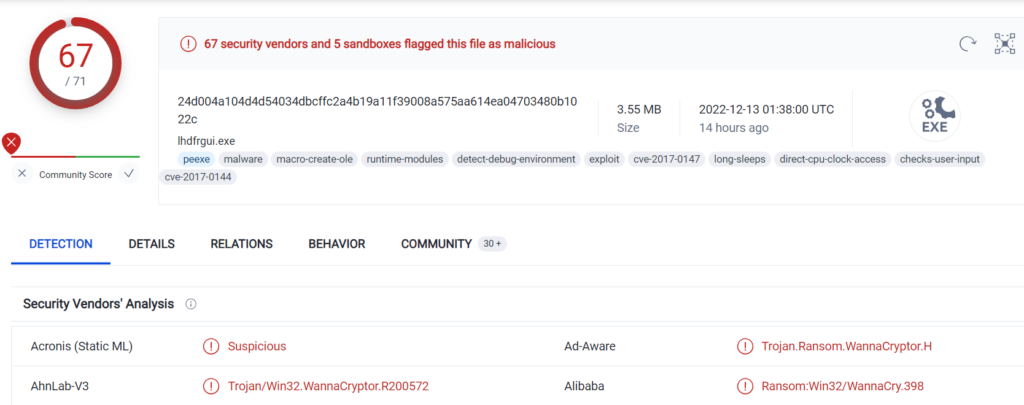
Basics Of Malware Analysis Part 1 Anoobishacking Ataware ransomware uses uac bypass using cmstplua com interface in atapiinit.exe (stage 1). it was downloaded from dropbox url when user open the malicious excel. Windows analysis report ucfcfc93cfdacefa08d2f6f82de8.dl.dropboxusercontent cd 0 get ciqj4bpzvuqptxdpg5ill7uwtot9hsz8rrdatmy9j xvpaqdzn7j3bgmqnv2jvtdo. Signatures found malware configuration yara detected rhadamanthys stealer writes to foreign memory regions tries to detect sandboxes and other dynamic analysis tools (process name or module or function) allocates memory in foreign processes injects a pe file into a foreign processes c2 urls ips found in malware configuration queries the volume information (name, serial number etc) of a. Some users with older dropbox accounts can share files via dl.dropboxusercontent download links. learn how they differ from other download links.

Free Automated Malware Analysis Service Powered By Falcon Sandbox Signatures found malware configuration yara detected rhadamanthys stealer writes to foreign memory regions tries to detect sandboxes and other dynamic analysis tools (process name or module or function) allocates memory in foreign processes injects a pe file into a foreign processes c2 urls ips found in malware configuration queries the volume information (name, serial number etc) of a. Some users with older dropbox accounts can share files via dl.dropboxusercontent download links. learn how they differ from other download links.
Malware Analysis Threat Intel Uac Bypasses Youtube
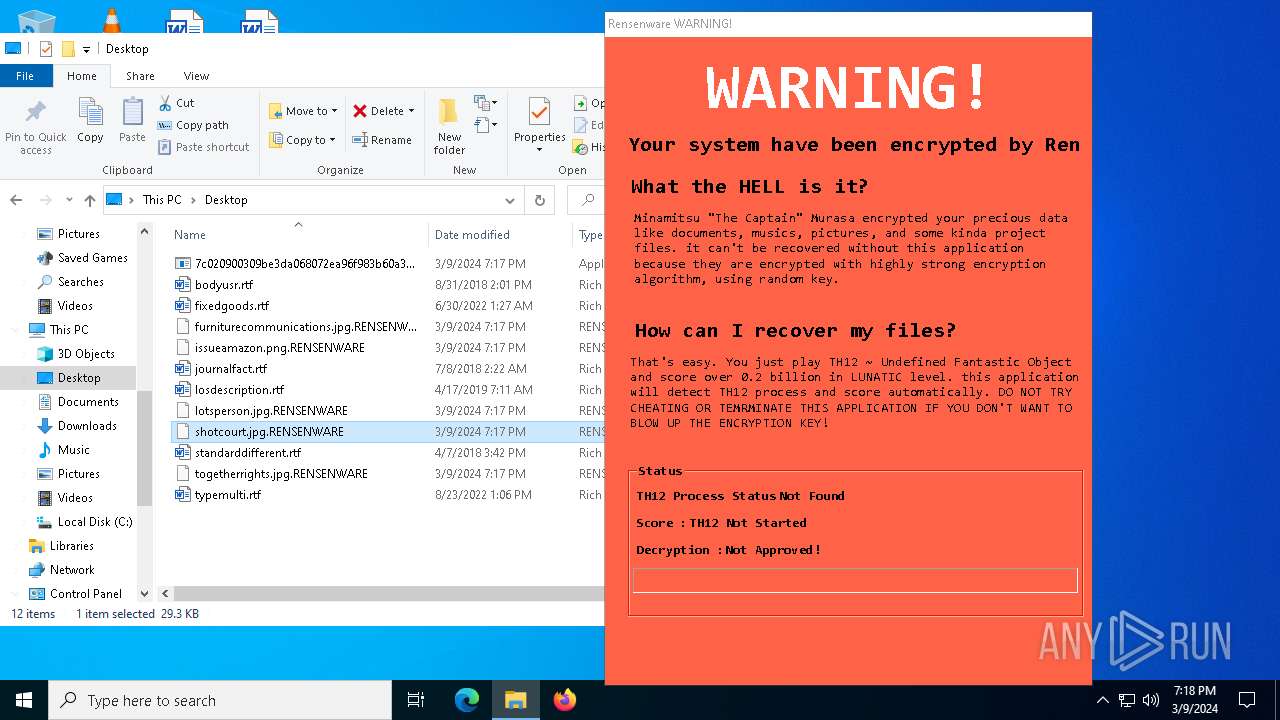
Malware Analysis
Malware Analysis 56a61aeb75d8f5be186c26607f4bb213abe7c5ec Tbres No