
Cryptography And Network Security Pdf Encryption Cryptography This document provides an overview of cryptography including: 1. cryptography is the process of encoding messages to protect information and ensure confidentiality, integrity, authentication and other security goals. 2. there are symmetric and asymmetric encryption algorithms that use the same or different keys for encryption and decryption. examples include aes, rsa, and des. 3. other. 3 bill figg security services x.800 defines it as: a service provided by a protocol layer of communicating open systems, which ensures adequate security of the systems or of data transfers rfc 2828 defines it as: a processing or communication service provided by a system to give a specific kind of protection to system resources x.800 defines it.

Network Security Cryptography Ppt Network security (summary) cryptography (symmetric and public) basic techniques & tradeoffs authentication common styles of attack key distribution why needed …. used in many different security scenarios secure email, secure transport (ssl), ip sec, 802.11 wep outline security: cryptography introduction security: authentication security: key. Cryptography and network security, fourth edition,william stallings ppt slides. Learn the fundamentals of network security, including cryptography, authentication, message integrity, and securing different layers of the network. explore practical applications such as securing email, tcp connections, wireless lans, and operational security with firewalls and intrusion detection systems. 1 introduction network security cryptography free download as powerpoint presentation (.ppt), pdf file (.pdf), text file (.txt) or view presentation slides online. this document provides details about a network security and cryptography course, including: the course meets for 3 lectures per week and uses the textbook "cryptography and network security" by behrouz a. forouzan. student.
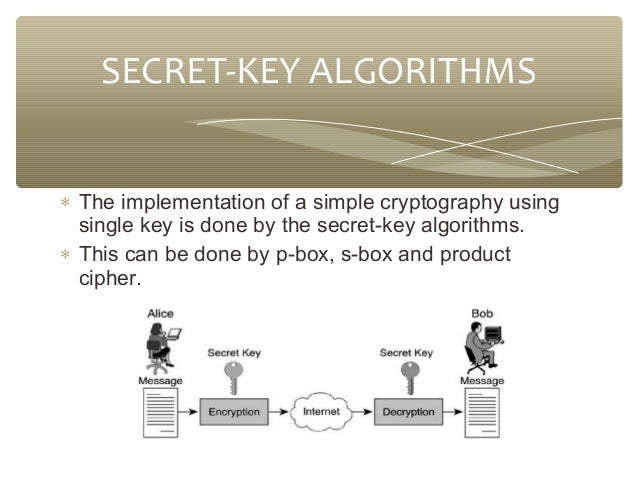
Network Security Cryptography Ppt Learn the fundamentals of network security, including cryptography, authentication, message integrity, and securing different layers of the network. explore practical applications such as securing email, tcp connections, wireless lans, and operational security with firewalls and intrusion detection systems. 1 introduction network security cryptography free download as powerpoint presentation (.ppt), pdf file (.pdf), text file (.txt) or view presentation slides online. this document provides details about a network security and cryptography course, including: the course meets for 3 lectures per week and uses the textbook "cryptography and network security" by behrouz a. forouzan. student. * * chapter 1 summary. * * lecture slides by lawrie brown for “cryptography and network security”, 5 e, by william stallings, briefly reviewing the text outline from ch 0, and then presenting the content from chapter 1 – “introduction”. * * this quote from the start of ch0 ”reader’s guide” sets the scene for why we want to study these issues. * the material in this book is. This document discusses network security and cryptography. it begins by defining a network and common network threats. it then discusses network security, including transit and traffic security. it covers problems and attacks like secrecy, authentication, and integrity control. the document introduces cryptography and its use in encryption and decryption to securely transmit data. it describes.

Network Security Cryptography Ppt * * chapter 1 summary. * * lecture slides by lawrie brown for “cryptography and network security”, 5 e, by william stallings, briefly reviewing the text outline from ch 0, and then presenting the content from chapter 1 – “introduction”. * * this quote from the start of ch0 ”reader’s guide” sets the scene for why we want to study these issues. * the material in this book is. This document discusses network security and cryptography. it begins by defining a network and common network threats. it then discusses network security, including transit and traffic security. it covers problems and attacks like secrecy, authentication, and integrity control. the document introduces cryptography and its use in encryption and decryption to securely transmit data. it describes.

Network Security Cryptography Ppt