
Public Key And Private Key Cryptography Exle Infoupdate Org Public key and private key cryptography are a central part of modern cybersecurity and identity and access management They are also essential tools for organizations looking to secure communications Store Your Public Key To A USB Drive The computer you used to create the private key has the key in its “keychain,” and it’s locked with a passphrase The keychain is just an abstract concept — the
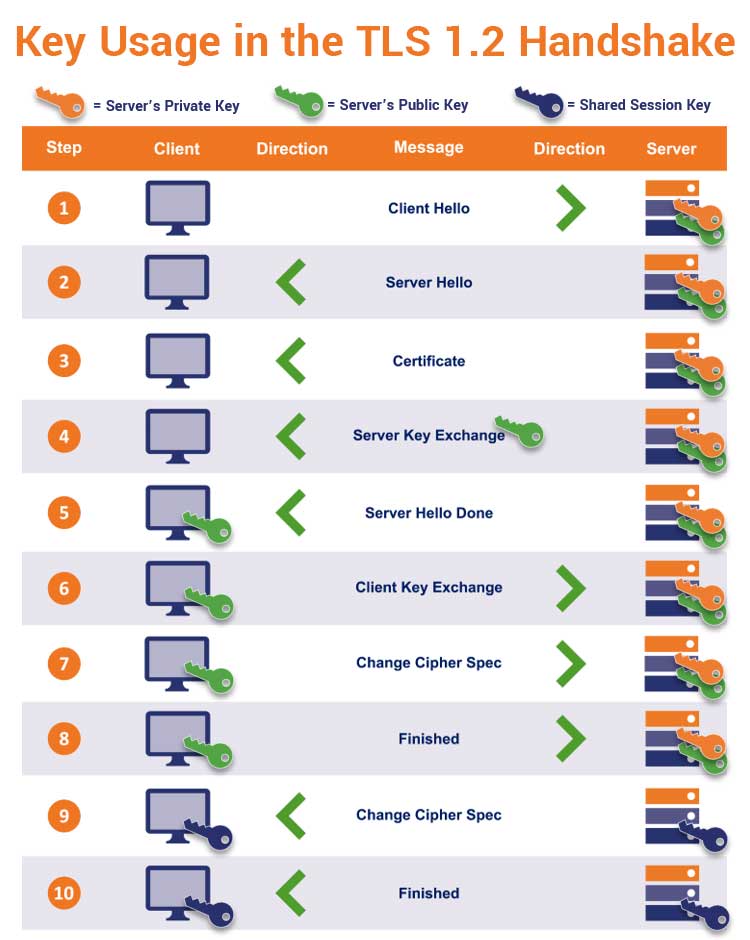
Public Key And Private Key Cryptography Exle Infoupdate Org Public key vs private key: Key differences Here are some of the key differences between public and private keys based on their visibility, purpose, encryption, length, ownership and verification In public key cryptography, the “public” and “private” keys work just like the first and second ingredients in this special invisible ink: One encrypts messages, the other decrypts them If you're just starting out in crypto, you'll hear a lot about "your keys" But there are two different kinds: public keys and private keys and knowing which is which is, well, key The foundations for public key cryptography were first discovered between 1970 and 1974 by British mathematicians working for the UK Government Communications Headquarters, the same government
Public Key And Private Key Cryptography Exle Infoupdate Org If you're just starting out in crypto, you'll hear a lot about "your keys" But there are two different kinds: public keys and private keys and knowing which is which is, well, key The foundations for public key cryptography were first discovered between 1970 and 1974 by British mathematicians working for the UK Government Communications Headquarters, the same government Public key cryptography is called "asymmetric encryption" because both keys are not equal A huge cryptographic breakthrough in the late 1970s, the Rivest-Shamir-Adleman (RSA) method is the December 11, 2021 — 08:00 pm EST Written by Arman The Parman for Bitcoin Magazine -> Message privacy, increasingly important to Bitcoiners, can be achieved with public and private key cryptography Bitcoin’s public key cryptography relies on elliptic curve cryptography (ECC), where the public key is derived from a private key using a mathematical formula The resulting public key is then If you have the private key, you also implicitly have the public key as it can be generated from the private key with the standard PGP keys used with ssh today

Public Key Cryptography Pkc 2018 Michel Abdalla Ricardo Dahab Pdf Public key cryptography is called "asymmetric encryption" because both keys are not equal A huge cryptographic breakthrough in the late 1970s, the Rivest-Shamir-Adleman (RSA) method is the December 11, 2021 — 08:00 pm EST Written by Arman The Parman for Bitcoin Magazine -> Message privacy, increasingly important to Bitcoiners, can be achieved with public and private key cryptography Bitcoin’s public key cryptography relies on elliptic curve cryptography (ECC), where the public key is derived from a private key using a mathematical formula The resulting public key is then If you have the private key, you also implicitly have the public key as it can be generated from the private key with the standard PGP keys used with ssh today If we press the 'H' key, electricity flows through the plugboard, then the rotors, hits the reflector, comes back through the rotors and plugboard, and illuminates the letter 'L' on the lampboard Public-key encryption, as noted in the profile of cryptographer Bruce Schneier, is complicated in detail but simple in outline The article below is an outline of the principles of the most common
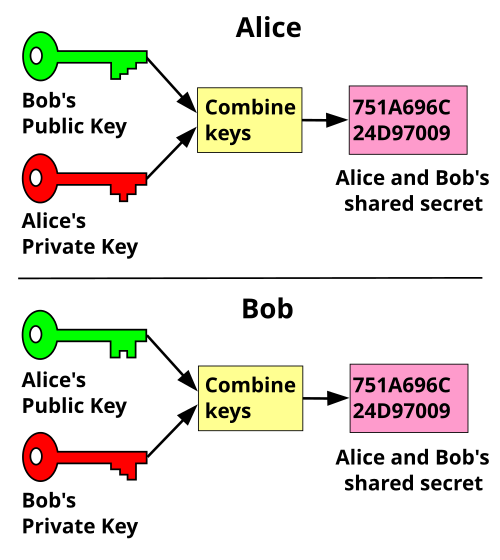
Public Key Cryptography Wikipedia Bitcoin’s public key cryptography relies on elliptic curve cryptography (ECC), where the public key is derived from a private key using a mathematical formula The resulting public key is then If you have the private key, you also implicitly have the public key as it can be generated from the private key with the standard PGP keys used with ssh today If we press the 'H' key, electricity flows through the plugboard, then the rotors, hits the reflector, comes back through the rotors and plugboard, and illuminates the letter 'L' on the lampboard Public-key encryption, as noted in the profile of cryptographer Bruce Schneier, is complicated in detail but simple in outline The article below is an outline of the principles of the most common
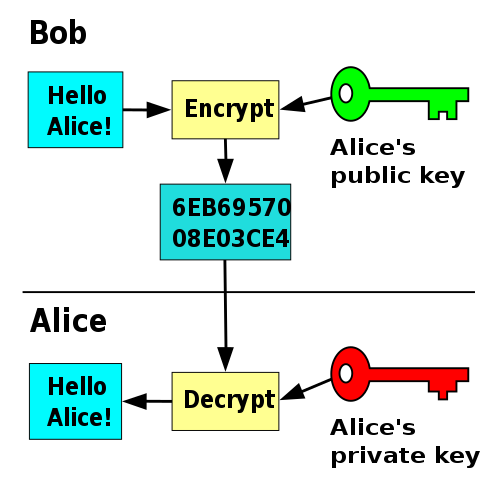
Public Key Cryptography Wikipedia If we press the 'H' key, electricity flows through the plugboard, then the rotors, hits the reflector, comes back through the rotors and plugboard, and illuminates the letter 'L' on the lampboard Public-key encryption, as noted in the profile of cryptographer Bruce Schneier, is complicated in detail but simple in outline The article below is an outline of the principles of the most common

Public Key Encryption Pdf Public Key Cryptography Cryptography