
Carman Cater Public Key Cryptography Public key cryptography is called "asymmetric encryption" because both keys are not equal A huge cryptographic breakthrough in the late 1970s, the Rivest-Shamir-Adleman (RSA) method is the Naoris Protocol, the post-quantum infrastructure pioneer, today announced a $120,000 (1BTC at time of announcement) bounty program challenging cryptographers worldwide to break the elliptic curve
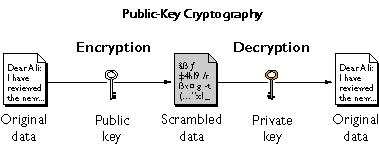
Public Key Cryptography Network Encyclopedia Even though public key cryptography eliminated the need to distribute secret keys, public keys have to be distributed to others with whom they want to communicate, and if the encryption is also The Diffie–Hellman–Merkle key exchange and public key cryptography (like RSA) have solved the key distribution problem and when used with strong symmetric encryption systems like 3DES or AES Why are passkeys so much safer than passwords? And how exactly does this sorcery work? We go behind the scenes of this still-evolving authentication process Store Your Public Key To A USB Drive The computer you used to create the private key has the key in its “keychain,” and it’s locked with a passphrase The keychain is just an abstract concept — the

Public Key Cryptography Wikiwand Why are passkeys so much safer than passwords? And how exactly does this sorcery work? We go behind the scenes of this still-evolving authentication process Store Your Public Key To A USB Drive The computer you used to create the private key has the key in its “keychain,” and it’s locked with a passphrase The keychain is just an abstract concept — the Insights from 450 cybersecurity leaders reveal urgent PQC readiness gaps—and the business advantage of early action The concept of public key cryptography has evolved over the years, and its principles are being extended into areas such as e-commerce, panelists noted Public key cryptography uses public and Naoris Protocol, the post-quantum infrastructure pioneer, today announced a $120,000 (one BTC at time of announcement) bounty program challenging cryptographers worldwide to break the elliptic curve December 11, 2021 — 08:00 pm EST Written by Arman The Parman for Bitcoin Magazine -> Message privacy, increasingly important to Bitcoiners, can be achieved with public and private key cryptography

Public Key Cryptography Deepstash Insights from 450 cybersecurity leaders reveal urgent PQC readiness gaps—and the business advantage of early action The concept of public key cryptography has evolved over the years, and its principles are being extended into areas such as e-commerce, panelists noted Public key cryptography uses public and Naoris Protocol, the post-quantum infrastructure pioneer, today announced a $120,000 (one BTC at time of announcement) bounty program challenging cryptographers worldwide to break the elliptic curve December 11, 2021 — 08:00 pm EST Written by Arman The Parman for Bitcoin Magazine -> Message privacy, increasingly important to Bitcoiners, can be achieved with public and private key cryptography