
Public Key Cryptography Pdf Public Key Cryptography Key Spies used to meet in the park to exchange code words, now things have moved on robert miles explains the principle of public private key cryptographynote1. Spies used to meet in the park to exchange code words, now things have moved on robert miles explains the principle of public private key.

Public Key Cryptography Pdf Public Key Cryptography Cryptography I think these videos explain very well: public key cryptography computerphile if you can't don't want to watch the video, here is a quick summary: a key pair consists of two keys that can encrypt something but the encrypted product can only be decrypted by its pair. the server has public and private keys and the client has public and private keys that the client got from the server. server's. 10:52 krack attacks (wifi wpa2 vulnerability) computerphile qwak1234 12:29 secrets of the deep dark web (deep dark web pt2) computerphile qwak1234 16:30 public key cryptography rsa encryption algorithm art of the problem qwak1234 5:56 web vs internet (deep dark web pt1) computerphile qwak1234 12:55 a strange map projection (euler. The public key public key cryptography the knapsack problem and public key cryptography. see also knapsack if you want to find out more : public key videos hashing algorithms and security – computerphile encryption and security agencies – computerphile extra bits – data security and flash memory – computerphile. Public key cryptography provides a secure way to exchange information and authenticate users by using pairs of keys. the public key is used for encryption and signature verification, while the private key is used for decryption and signing.

An Introduction To Public Key Cryptography And Its Common Applications The public key public key cryptography the knapsack problem and public key cryptography. see also knapsack if you want to find out more : public key videos hashing algorithms and security – computerphile encryption and security agencies – computerphile extra bits – data security and flash memory – computerphile. Public key cryptography provides a secure way to exchange information and authenticate users by using pairs of keys. the public key is used for encryption and signature verification, while the private key is used for decryption and signing. Public key cryptography computerphile lesson with certificate for technology courses. How passkeys work: going passwordless with public key cryptography what's the achilles' heel of passwords? shared secrets. here's how we eliminate them.
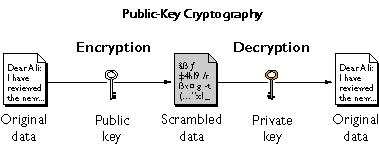
Public Key Cryptography Network Encyclopedia Public key cryptography computerphile lesson with certificate for technology courses. How passkeys work: going passwordless with public key cryptography what's the achilles' heel of passwords? shared secrets. here's how we eliminate them.

Public Key Cryptography Obsidian Publish

Public Key Cryptography Download Scientific Diagram

Ppt Public Key Cryptography Powerpoint Presentation Free Download