
What Is Role Based Access Control Rbac Pdf Computer Access Role based access control (rbac) helps minimize the amount of administrative work there is to do and potential errors. we will explain how role based access control works and is implemented. Role based access control the concept of role based access control is to create a set of permissions and assign these permissions to a user or group. with the help of these permissions, only limited access to users can be provided therefore level of security is increased.

Rbac Explained How Does Role Based Access Control Work Ionos Learn how role based access control (rbac) works, its key components, and how it enhances security in managing user permissions. Abac techniques let you determine access by user characteristics, object characteristics, action types, and more. let’s dig into the details. what is role based access control? someone logs into your computer system. what can that person do? if you use rbac techniques, the answer to that question depends on that person's role. How does rbac work? rbac originates from the idea that different employees have different kinds of information they need to access to do their jobs properly. if an employee’s job or work does not need them to access non essential sections of an information technology platform or particular data, role based access control will restrict them from doing so (s). you may, for instance, make it a. This comprehensive guide to rule based access control (rubac) explains how it strengthens data security by managing user access based on predefined roles and rules. learn about the benefits of rbac, best practices for implementation, and how it aligns with zero trust security principles.
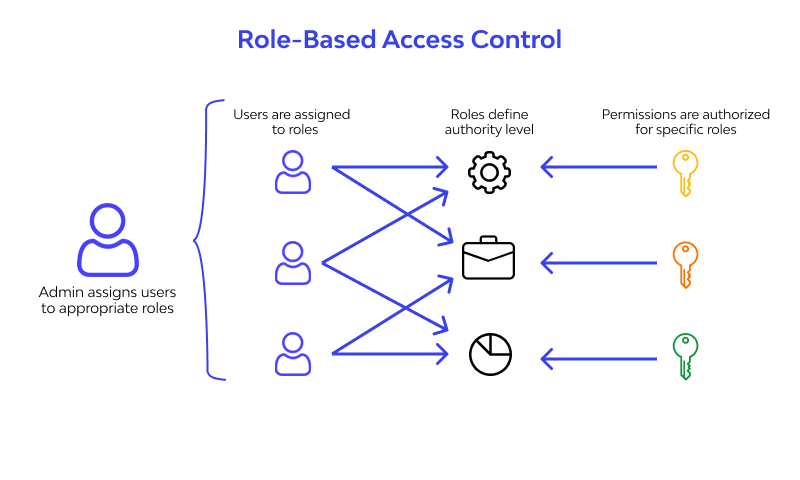
Rbac Explained How Does Role Based Access Control Work Ionos My Xxx How does rbac work? rbac originates from the idea that different employees have different kinds of information they need to access to do their jobs properly. if an employee’s job or work does not need them to access non essential sections of an information technology platform or particular data, role based access control will restrict them from doing so (s). you may, for instance, make it a. This comprehensive guide to rule based access control (rubac) explains how it strengthens data security by managing user access based on predefined roles and rules. learn about the benefits of rbac, best practices for implementation, and how it aligns with zero trust security principles. Die rollenbasierte zugriffskontrolle rbac reduziert verwaltungsaufwand und fehler. wir erklären, wie role based access control funktioniert und umgesetzt wird. Learn what rbac is, how it works, and how role based access control helps enforce least privilege in cloud and enterprise environments.
Role Based Access Control Rbac Die rollenbasierte zugriffskontrolle rbac reduziert verwaltungsaufwand und fehler. wir erklären, wie role based access control funktioniert und umgesetzt wird. Learn what rbac is, how it works, and how role based access control helps enforce least privilege in cloud and enterprise environments.

Role Based Access Control Rbac Cyberhoot