
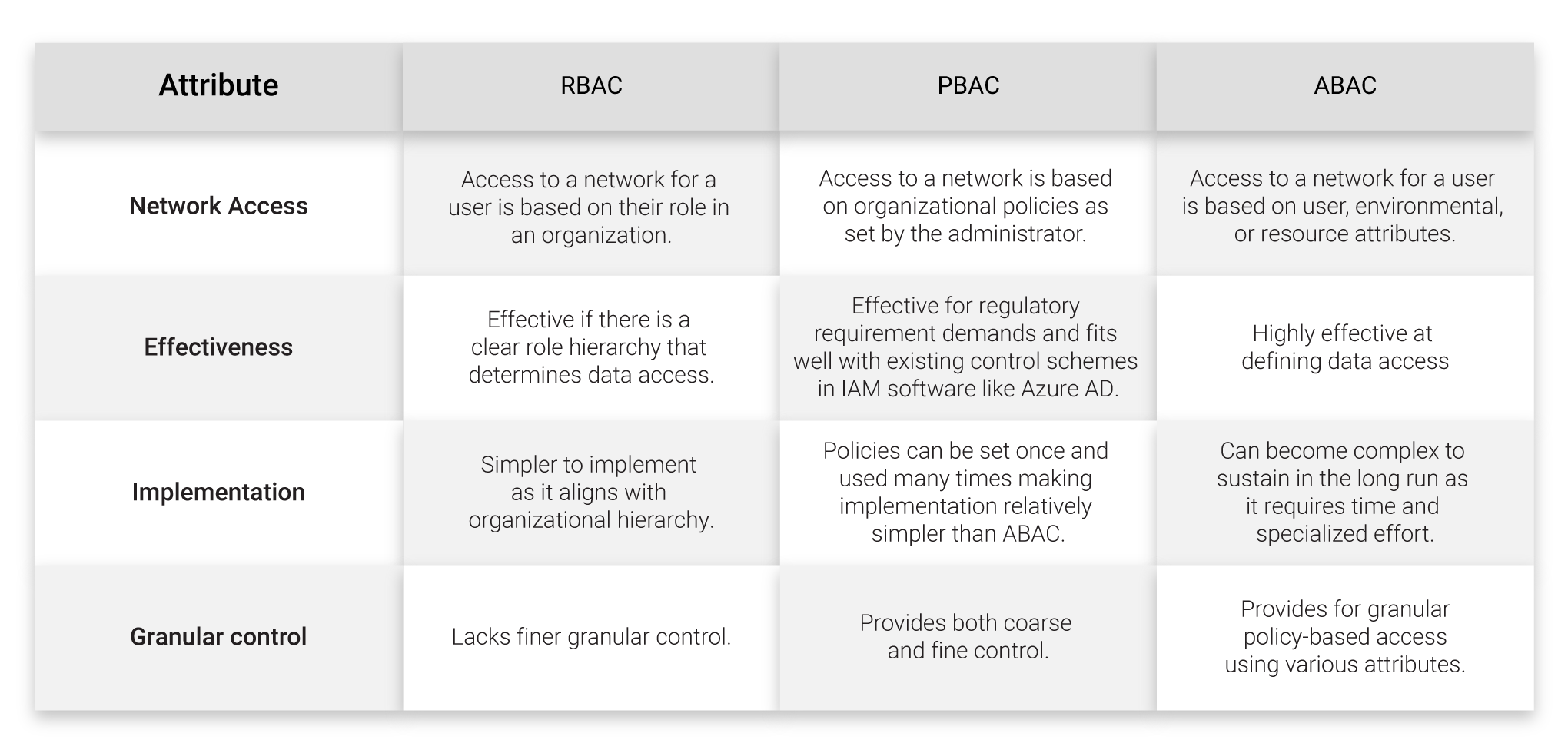
Attribute Based Access Control Vs Role Based Access Control Security is important especially when it comes to product information management systems. many pims on the market come with a variety of security measures, two of the most common being role based access control (rbac) and attribute based access control (abac). so which is the best protocol to secure your pim software when pitting rbac vs. abac. Knowing the difference between role based access control (rbac) vs. attribute based access control (abac) can help you make a smart decision. the main difference between rbac vs. abac is the way each method grants access.

Rbac Vs Abac Role Based Or Attribute Based Access For Pim Security Attribute based access control (abac) is an authorization system that defines access based on attributes associated with security principals, resources, and the environment of an access request. with abac, you can grant a security principal access to a resource based on attributes. azure abac refers to the implementation of abac for azure. Compare rbac vs abac: learn the pros, cons, and use cases of role based & attribute based access control to enhance security and simplify management. Rbac and abac are two popular models for securing access to resources. both models have their merits and both have limitations. learn all about role based and attribute based access control and see example policies in this post. Compare rbac vs abac to find the right access control model. learn how to grant secure, granular access based on roles or attributes.

What Is Role Based Access Control Rbac Vs Abac Vrogue Co Rbac and abac are two popular models for securing access to resources. both models have their merits and both have limitations. learn all about role based and attribute based access control and see example policies in this post. Compare rbac vs abac to find the right access control model. learn how to grant secure, granular access based on roles or attributes. Introduction access control is a cornerstone of application security, ensuring that users only access the resources they are authorized to use. two widely adopted access control models are role based access control (rbac) and attribute based access control (abac). Organizations use attribute based access control (abac) to achieve more fine grained access control —either replacing or supplementing rbac. the difference between rbac and abac stems from the way each method manages access. unlike rbac, which grants access according to predefined roles, abac is a security policy that relies on a combination of attributes to match users with the resources.
What Is Role Based Access Control Rbac Vs Abac Vrogue Co Introduction access control is a cornerstone of application security, ensuring that users only access the resources they are authorized to use. two widely adopted access control models are role based access control (rbac) and attribute based access control (abac). Organizations use attribute based access control (abac) to achieve more fine grained access control —either replacing or supplementing rbac. the difference between rbac and abac stems from the way each method manages access. unlike rbac, which grants access according to predefined roles, abac is a security policy that relies on a combination of attributes to match users with the resources.
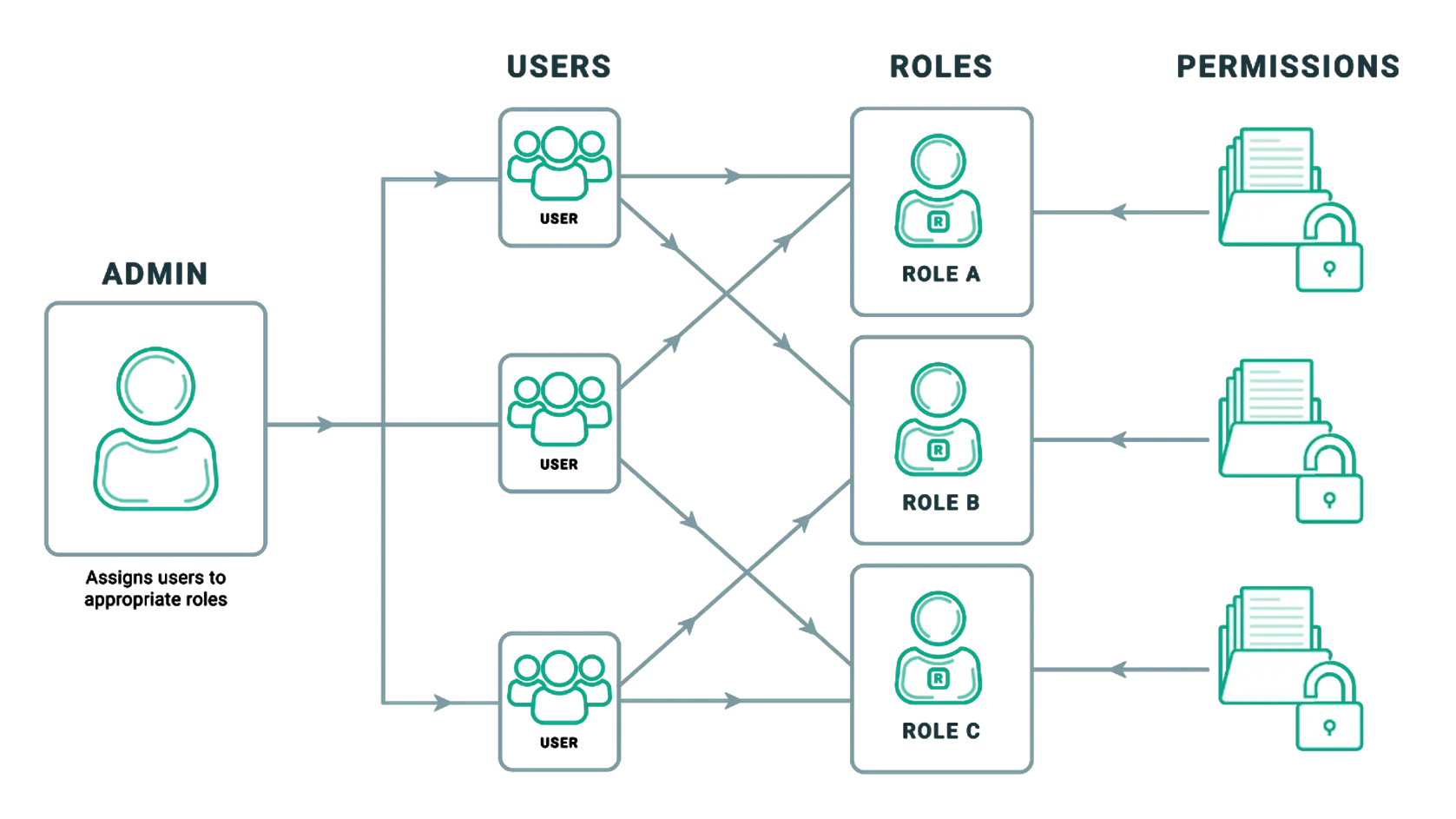
What Is Role Based Access Control Rbac Vs Abac Vrogue Co