.png)
Redline Malware Analysis Overview By Any Run Redline infostealer malware analysis with wireshark & any.run cyberwox 51.4k subscribers 187. Redline stealer is a malicious program that collects users’ confidential data from browsers, systems, and installed software. follow live malware statistics of this infostealer and get new reports, samples, iocs, etc.

Redline Malware Analysis Overview By Any Run A malware analysis project focused on examination of a redline infostealer trojan packet capture in wireshark. Redline stealer, an infostealer malware first identified in march 2020, specializes in extracting valuable information and assets from compromised systems, primarily targeting end users. commonly distributed through compromised software downloads, phishing attempts, and drive by downloads, redline stealer focuses on pilfering insecure passwords and cryptocurrency wallets. Redline stealer’s infection diagram static analysis malware’s architecture the malware is an executable file that works with 32 bit architecture. Analysis of a redline infostealer attack to observe how a redline infection unfolds, a sample of this malware can be uploaded to a malware sandbox like any.run.
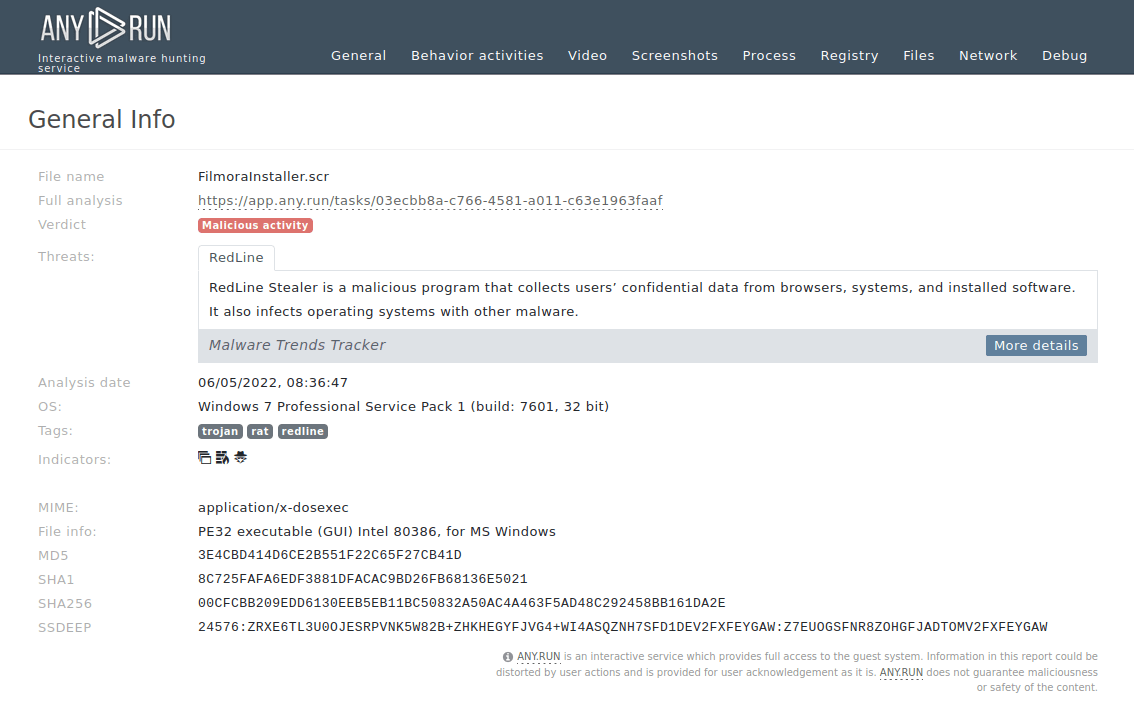
Redline Malware Analysis Overview By Any Run Redline stealer’s infection diagram static analysis malware’s architecture the malware is an executable file that works with 32 bit architecture. Analysis of a redline infostealer attack to observe how a redline infection unfolds, a sample of this malware can be uploaded to a malware sandbox like any.run. Redline stealer is one of the most popular info stealers out there. the malware is available for sale on underground forums for a different subscription options. Dive into our full analysis of redline, the prominent malware impacting users worldwide and trending on russian forums.

Redline Infostealer Cyber Anubis Redline stealer is one of the most popular info stealers out there. the malware is available for sale on underground forums for a different subscription options. Dive into our full analysis of redline, the prominent malware impacting users worldwide and trending on russian forums.
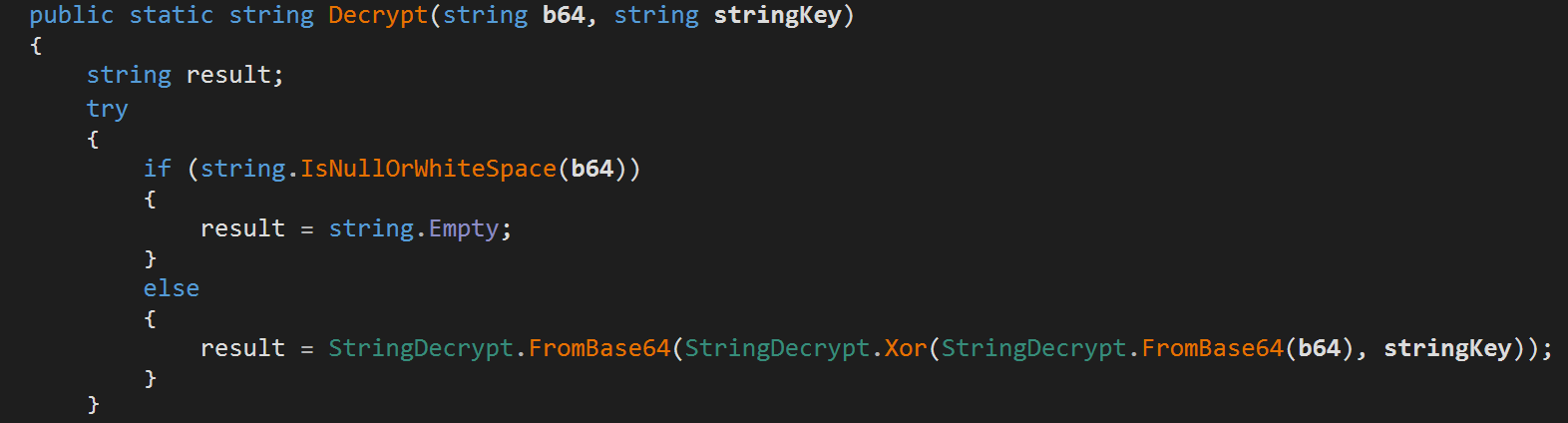
Redline Infostealer Cyber Anubis