
What Is Role Based Access Control Rbac Pdf Computer Access This slide represents the flow chart of role based access control in an enterprise. it starts with security check on accumulated modifications, application and authentication services and ends with operation on isolated object. features of these powerpoint presentation slides:. Download our role based access control diagram powerpoint template to discuss your organization’s standards regarding accessibility and permissions. role based access control, or rbac, defines who can do what or which user can change the apps, files, online resources, and databases.

Role Based Access Control Rbac Flow Chart Ppt Example This document discusses role based access control (rbac) and provides examples of implementing rbac in perl applications. it begins with definitions of authentication and authorization. it then covers authentication processes, examples of authentication modules for perl, and how to implement authentication sessions. the document discusses different types of authorization, including simple. Role based access control rbac process flow information pdf this slide represents the process flow of role based access control in an organization. it includes details related to urp, baseline policy from national rbac database, nrd activities etc. pitch your topic with ease and precision using this role based access control rbac process flow information pdf. this layout presents information. Download our role based access control template for ms powerpoint and google slides to showcase the key parts, design patterns, and importance of rbac. This powerpoint template explains the process flow of rbac or role based access control in a structured and simple design. it simplifies critical elements of urp, baseline policies, and activities taken from the national rbac database to let you manage access control very easily.

Role Based Access Control Rbac Flow Chart Vrogue Co Download our role based access control template for ms powerpoint and google slides to showcase the key parts, design patterns, and importance of rbac. This powerpoint template explains the process flow of rbac or role based access control in a structured and simple design. it simplifies critical elements of urp, baseline policies, and activities taken from the national rbac database to let you manage access control very easily. The document discusses access control and role based access control (rbac) models. it describes the core components of rbac including users, roles, permissions, and role hierarchies. rbac assigns system access based on a user's role within an organization and restricts access to authorized users. the document outlines how rbac can be implemented in a small company and used to define roles for. Page 15 of itl brochure “i would like to take this opportunity to underscore the importance and relevance of research conducted by your laboratory into role based access control (rbac). in the area of security one of the features most requested by sybase customers has been rbac.
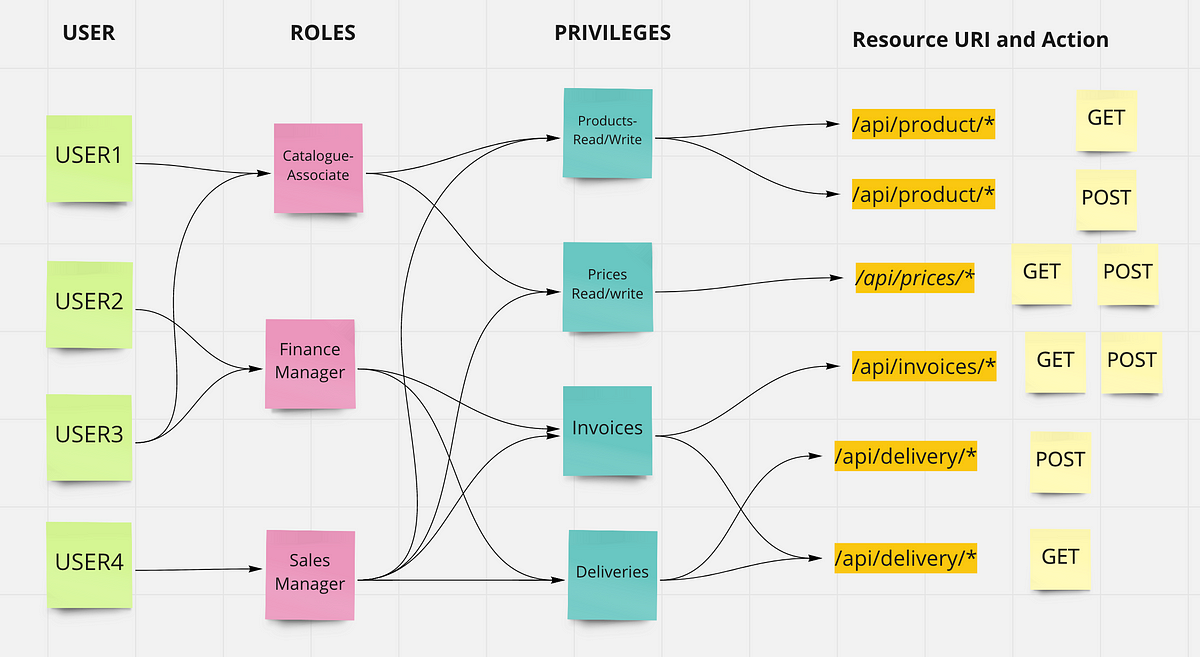
Role Based Access Control Rbac Flow Chart Vrogue Co The document discusses access control and role based access control (rbac) models. it describes the core components of rbac including users, roles, permissions, and role hierarchies. rbac assigns system access based on a user's role within an organization and restricts access to authorized users. the document outlines how rbac can be implemented in a small company and used to define roles for. Page 15 of itl brochure “i would like to take this opportunity to underscore the importance and relevance of research conducted by your laboratory into role based access control (rbac). in the area of security one of the features most requested by sybase customers has been rbac.