
Role Based Access Control Rbac Role Based Access Control Rbac By Role based access control (rbac) is a security approach that authorizes and restricts system access to users based on their role(s) within an organization. Role based access control (rbac) is a model for authorizing end user access to systems, applications and data based on a user’s predefined role. for example, a security analyst can configure a firewall but can’t view customer data, while a sales rep can see customer accounts but can’t touch firewall settings.
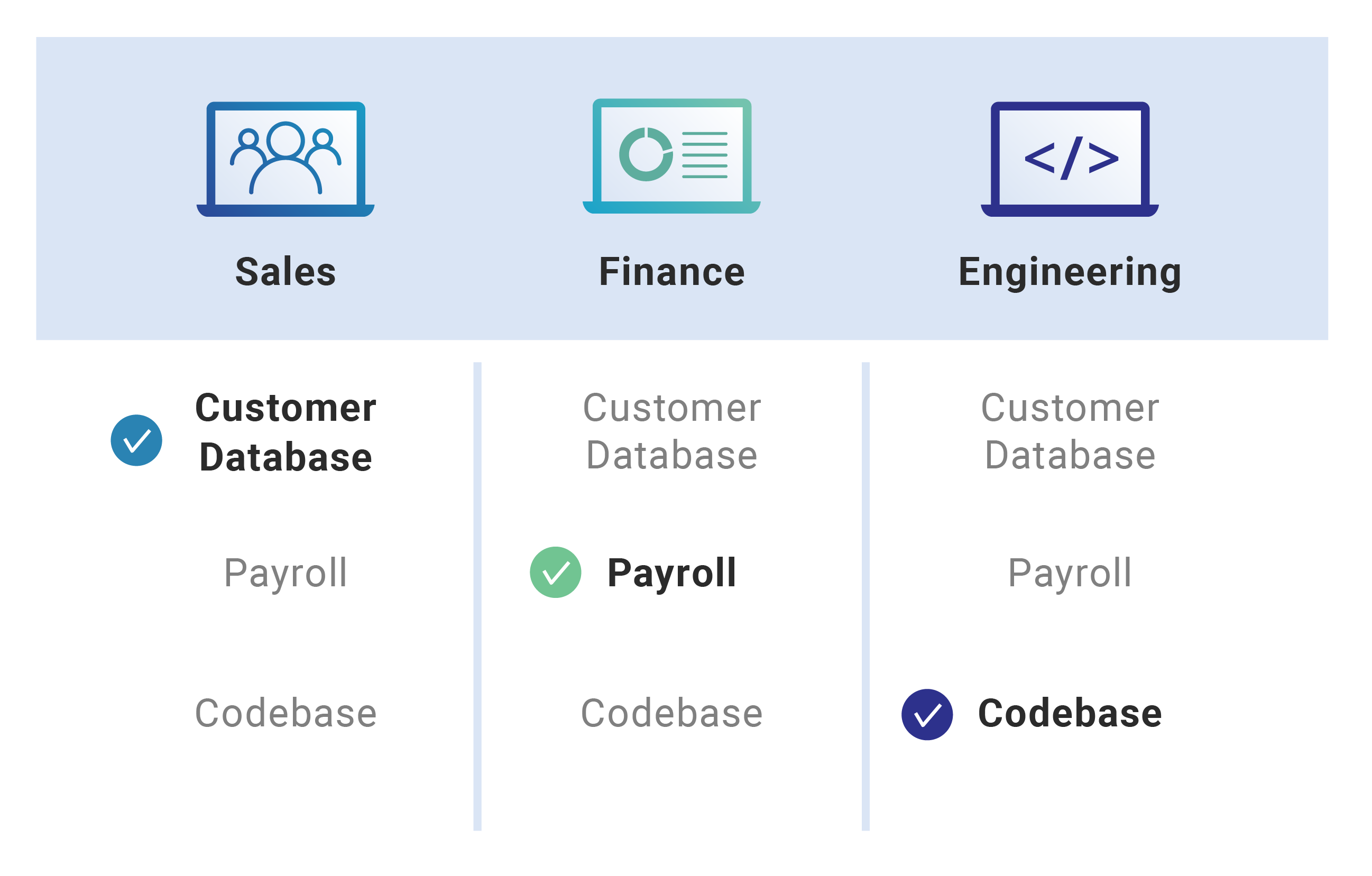
What Is Role Based Access Control Rbac Cloudflare Access management for cloud resources is a critical function for any organization that is using the cloud. azure role based access control (azure rbac) helps you manage who has access to azure resources, what they can do with those resources, and what areas they have access to. Key takeaways role based access control (rbac) restricts system access to authorized users based on their roles, enhancing security, operational efficiency, and compliance by assigning permissions according to job responsibilities rather than individuals. effective rbac implementation requires careful planning, including accurate role definition, appropriate permission assignment, role. Learn what rbac is, how it works, and best practices for implementation. enhance security and access management today. Role based access control (rbac) is a method for managing user permissions based on roles within an organization. this guide explores the principles of rbac, its benefits, and how it enhances security and efficiency.

Role Based Access Control Rbac Cyberhoot Learn what rbac is, how it works, and best practices for implementation. enhance security and access management today. Role based access control (rbac) is a method for managing user permissions based on roles within an organization. this guide explores the principles of rbac, its benefits, and how it enhances security and efficiency. This is a complete overview of role based access control (rbac). learn about common uses of rbac, why it is used, and its benefits in this in post. Rbac (role based access control) is a security model that restricts system access based on users' roles within an organization, assigning permissions to roles instead of individuals.

Role Based Access Control Rbac This is a complete overview of role based access control (rbac). learn about common uses of rbac, why it is used, and its benefits in this in post. Rbac (role based access control) is a security model that restricts system access based on users' roles within an organization, assigning permissions to roles instead of individuals.