
Information Security Policy Framework Pdf Information Security Security policies must also account for variations in business functions and information systems to be universally applicable. to meet these requirements, microsoft implements a comprehensive security governance program as a part of the microsoft policy framework. security governance falls under the microsoft security policy (msp). Cyber security policies and standards in partnership, the cybersecurity risk foundation (crf) and sans have created a library of free cybersecurity policy templates to help organizations quickly define, document, and deploy key cybersecurity policies.

Protective Security Policy Framework Pdf Computer Security Security The ncsr question set represents the national institute of standards and technology cybersecurity framework (nist csf). this guide gives the correlation between 49 of the nist csf subcategories, and applicable policy and standard templates. a nist subcategory is represented by text, such as “id.am 5.” this represents the nist function of identify and the category of asset management. for. Learn how to build a simple yet powerful information security policy framework with this step by step guide—ideal for startups and growing businesses. An it security policy identifies the rules and procedures for all individuals accessing and using an organization's it assets and resources. learn the different components of an it security policy and the best practices to adopt. Learn about the top it security frameworks and standards available, and get advice on choosing the frameworks and standards to best protect company data.
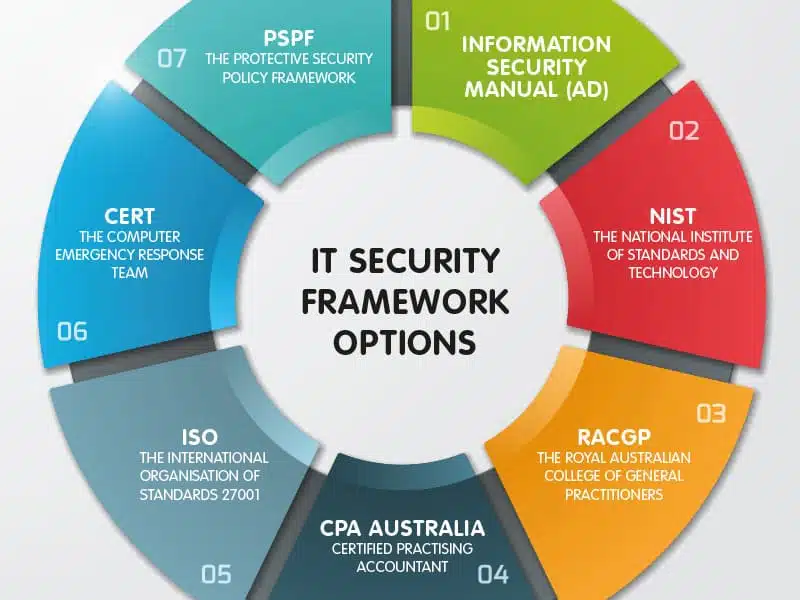
The 7 Most Common It Security Framework Options In Australia Stanfield It An it security policy identifies the rules and procedures for all individuals accessing and using an organization's it assets and resources. learn the different components of an it security policy and the best practices to adopt. Learn about the top it security frameworks and standards available, and get advice on choosing the frameworks and standards to best protect company data. For further guidance, organizations can refer to information security policy examples and information security policy best practices to ensure their policy framework is comprehensive and robust. utilizing an information security policy template can also provide a useful starting point for tailoring a framework to specific organizational needs. A well defined security policy serves as a framework that safeguards data, mitigates risks, and ensures compliance with regulatory standards. without clear security policies, businesses expose themselves to cyber threats, operational disruptions, and legal consequences.

Security Policy Framework Go Coding For further guidance, organizations can refer to information security policy examples and information security policy best practices to ensure their policy framework is comprehensive and robust. utilizing an information security policy template can also provide a useful starting point for tailoring a framework to specific organizational needs. A well defined security policy serves as a framework that safeguards data, mitigates risks, and ensures compliance with regulatory standards. without clear security policies, businesses expose themselves to cyber threats, operational disruptions, and legal consequences.
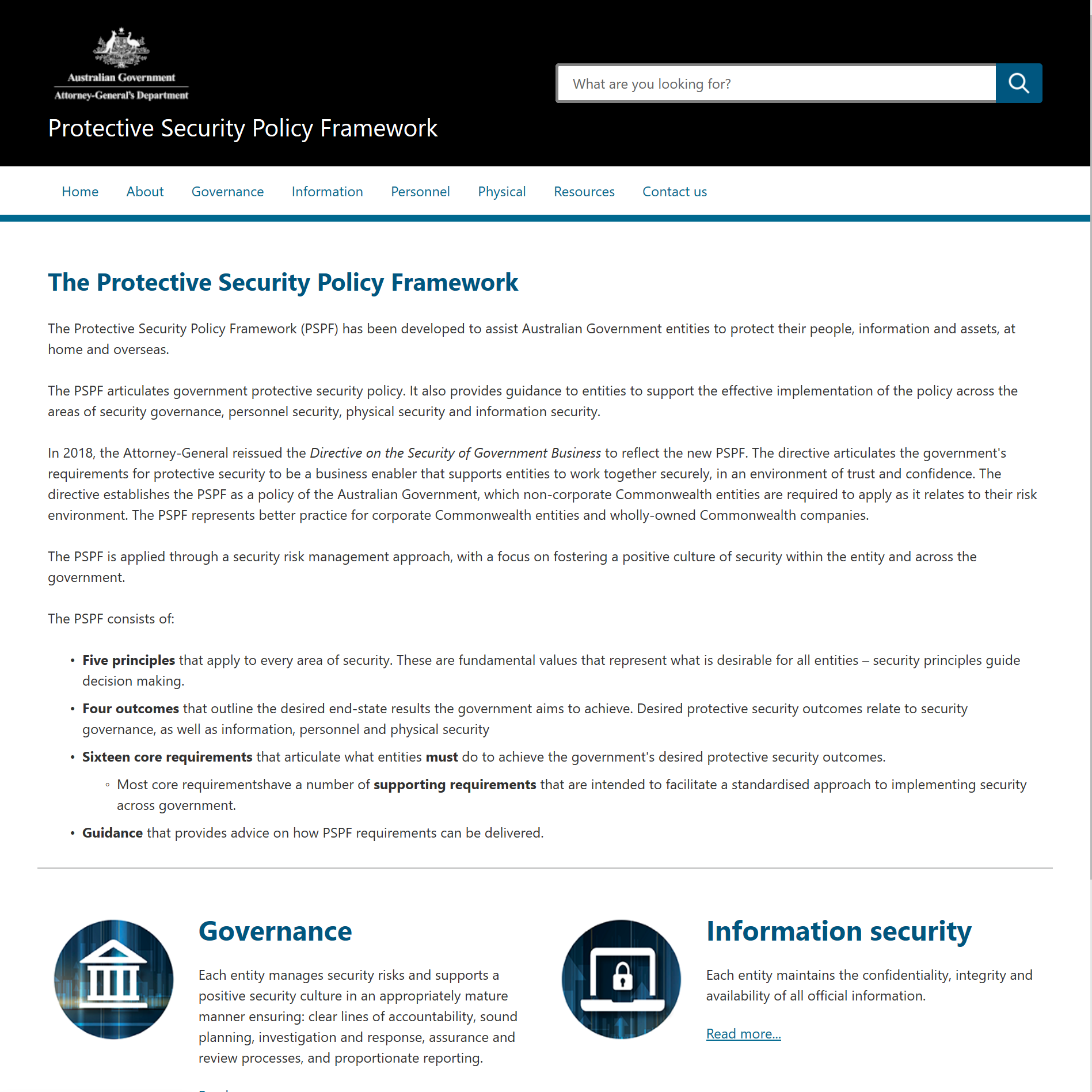
Protective Security Policy Framework Pspf Govcms

Protective Security Policy Framework Commonwealth Fraud Prevention Centre
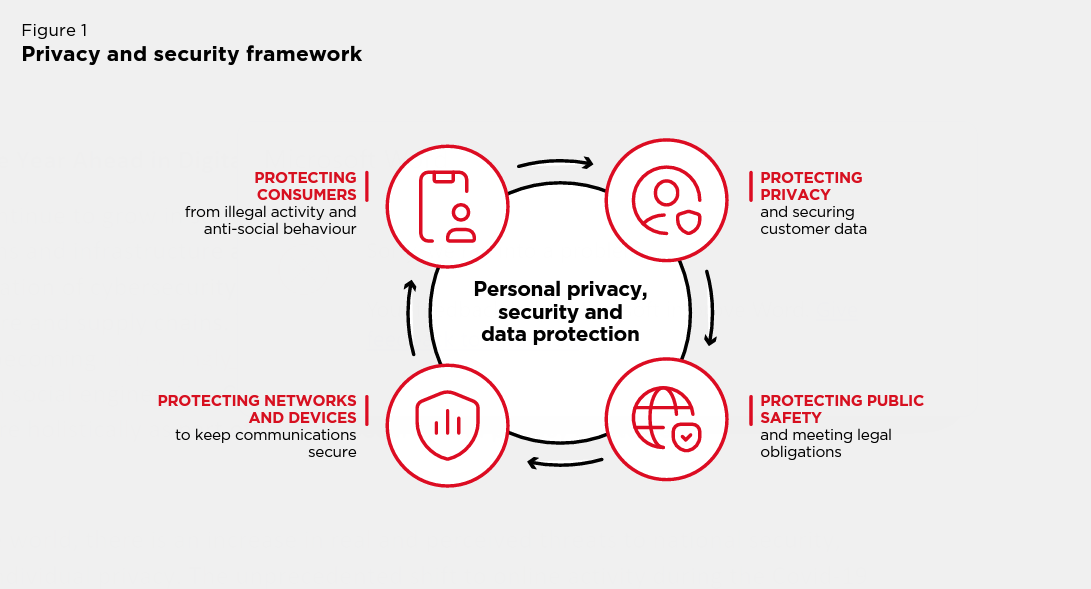
Gsma Privacy And Security Framework Public Policy