
Role Based Access Control Rbac Role Based Access Control Rbac By This article describes the different built in roles that azure deployment environments supports, and how they map to organizational roles like platform engineer and dev manager. azure role based access control (rbac) specifies built in role definitions that outline the permissions to be applied. Role based access control is available only on distributed deployments (stream, edge) with an enterprise license tier. on single instance deployments or distributed deployments with other licenses all users will have full administrative privileges.
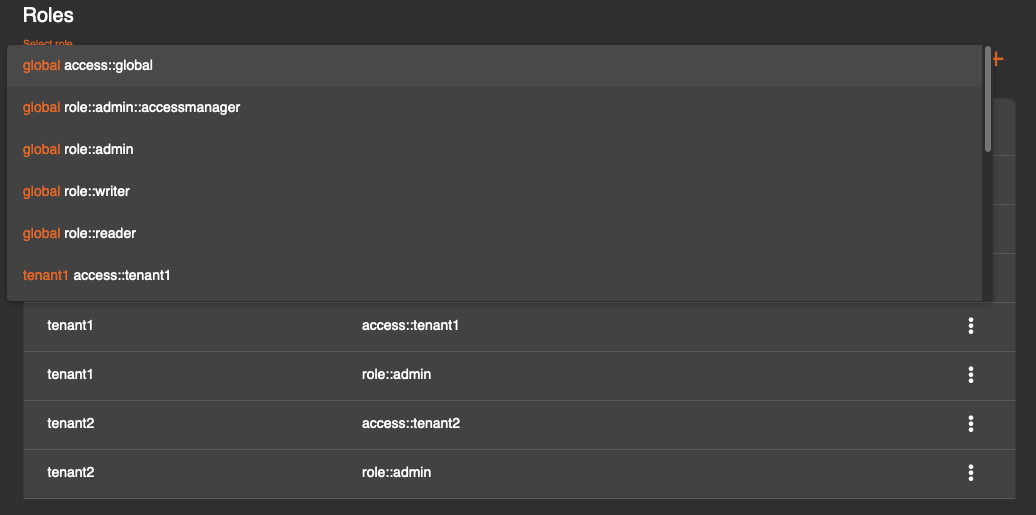
Role Based Access Control Rbac Rbac is available in distributed deployments with an enterprise license. this allows you to assign access policies at both the worker group level and the role level. Using rbac authorization role based access control (rbac) is a method of regulating access to computer or network resources based on the roles of individual users within your organization. Set up role based access control (rbac) authentication is often combined with kubernetes role based access control (rbac) to provide more finely grained access control to clusters for authenticated users and service accounts. it is recommended to create rbac policies that use group names instead of user identifiers. Manage users and roles ece role based access control (rbac) provides a way to add multiple users and restrict their access to specific platform resources. in addition to the system admin and readonly users, you can create additional users and assign pre built roles to control access to platform operations, deployment assets, or api calls.
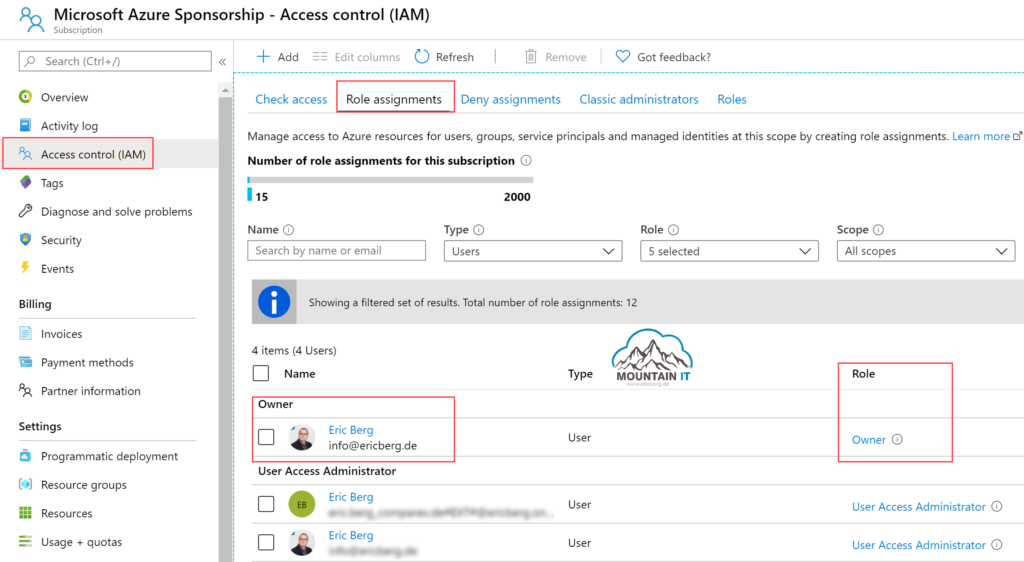
Basic Role Based Access Control Rbac Mountain It Eric Berg Set up role based access control (rbac) authentication is often combined with kubernetes role based access control (rbac) to provide more finely grained access control to clusters for authenticated users and service accounts. it is recommended to create rbac policies that use group names instead of user identifiers. Manage users and roles ece role based access control (rbac) provides a way to add multiple users and restrict their access to specific platform resources. in addition to the system admin and readonly users, you can create additional users and assign pre built roles to control access to platform operations, deployment assets, or api calls. Use role based access control (rbac) and scope tags to filter configuration profiles to specific roles. Azure implements two primary governance tools, role based access control (rbac), and resource policy, and it's up to each organization to design their governance model using them. in this post we will cover rbac.

Role Based Access Control Rbac Use role based access control (rbac) and scope tags to filter configuration profiles to specific roles. Azure implements two primary governance tools, role based access control (rbac), and resource policy, and it's up to each organization to design their governance model using them. in this post we will cover rbac.

Rbac Role Based Access Control Behance
Rbac Role Based Access Control
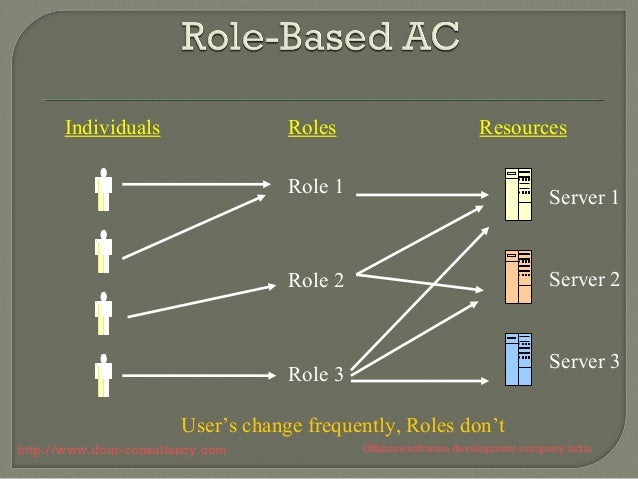
Role Based Access Control Rbac