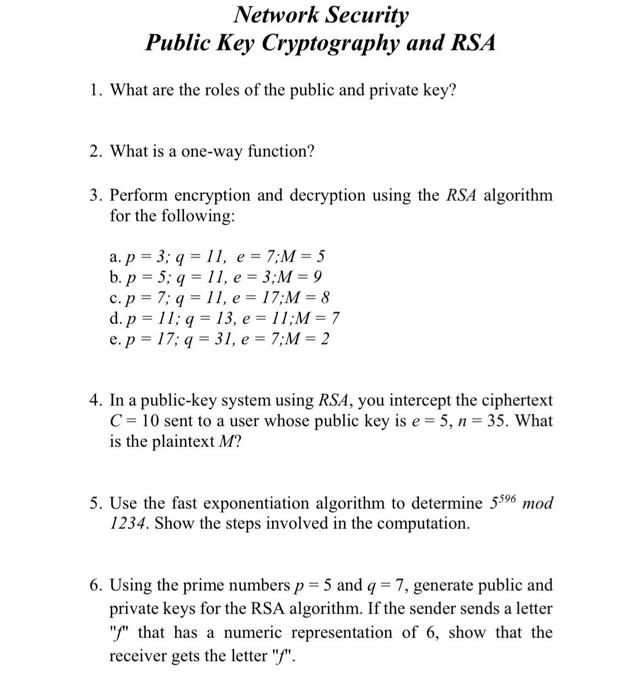
Solved Network Security Public Key Cryptography And Rsa 1 Chegg Using the prime numbers p =5 and q =7, generate public and private keys for the rsa algorithm. if the sender sends a letter " f " that has a numeric representation of 6 , show that the receiver gets the letter " f ". In a system an rsa algorithm with p = 5 and q = 11, is implemented for data security. what is the value of the decryption key if the value of the encryption key is 27 ?.

Network Security 1 0 Modules 15 17 Cryptography Group Exam Answers The public key is used for encryption and is known to everyone, while the private key is used for decryption and must be kept secret by the receiver. rsa algorithm is named after ron rivest, adi shamir and leonard adleman, who published the algorithm in 1977. example of asymmetric cryptography: if person a wants to send a message securely to. However, public key encryption has proved indispensable for key management, for distributing the keys needed for the more traditional symmetric key encryption decryption of the content, for digital signature applications, etc. Learn about the rsa algorithm, a cornerstone of modern cryptography. understand its principles, applications, and how it secures communications. Clo 1. to understand cryptography, network security and its principles clo 2. to analyse different cryptography algorithms clo 3. to illustrate public and private key cryptography clo 4. to explain key management, distribution and certification clo 5. to understand necessary approaches and techniques to build protection mechanisms in order to secure computer networks.

Solved 1 In Rsa Cryptography If The Public Key 25 551 Chegg Learn about the rsa algorithm, a cornerstone of modern cryptography. understand its principles, applications, and how it secures communications. Clo 1. to understand cryptography, network security and its principles clo 2. to analyse different cryptography algorithms clo 3. to illustrate public and private key cryptography clo 4. to explain key management, distribution and certification clo 5. to understand necessary approaches and techniques to build protection mechanisms in order to secure computer networks. Contents 1. public key cryptography and rsa semester 1 2017 advanced network and information security page 1 of 3 vit i victorian institute of technology pty ltd victorie intitute of technology vit.edu.au abn: 41 085 128 525 kto no: 20829 teosa id: prv14007 cricos provider code: 02044 task 1 review questions 1. All public key cryptosystems have some underlying mathematical operation. rsa has exponentiation (raising the message or ciphertext to the public or private values).

Solved 1 In The Use Of Rsa Cryptography If The Public Key Chegg Contents 1. public key cryptography and rsa semester 1 2017 advanced network and information security page 1 of 3 vit i victorian institute of technology pty ltd victorie intitute of technology vit.edu.au abn: 41 085 128 525 kto no: 20829 teosa id: prv14007 cricos provider code: 02044 task 1 review questions 1. All public key cryptosystems have some underlying mathematical operation. rsa has exponentiation (raising the message or ciphertext to the public or private values).
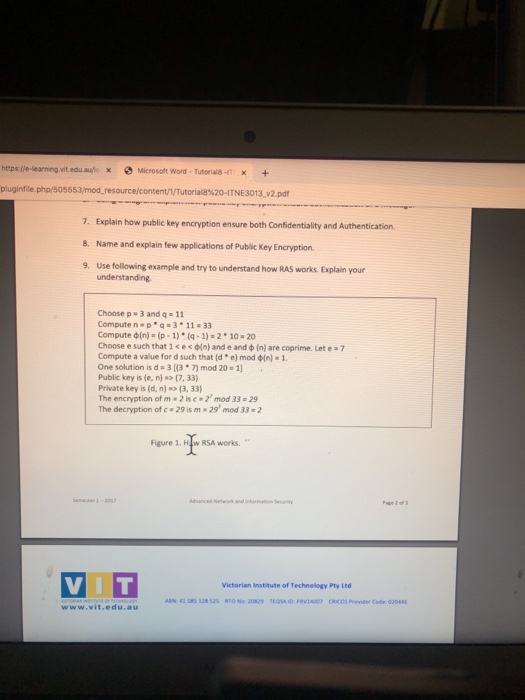
Https E Learning Vit Edu Auto X Microsoft Word Tutorial X