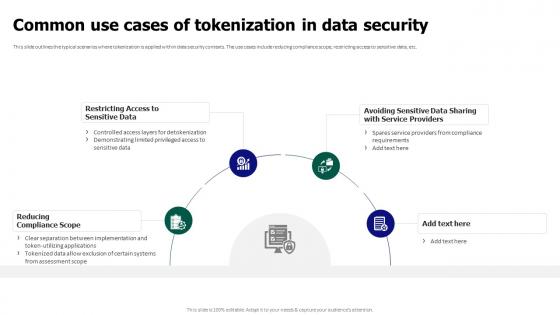
Tokenization For Improved Data Security Common Use Cases Of Companies can’t maximize the value of their data without strong data security Data breaches are becoming more common each year, and every company is looking to deploy AI—making it even more Asset tokenization has emerged as a disruptive force in the financial services landscape In 2018, the global market capitalization of tokenized assets stood at a mere $15 billion

Tokenization For Improved Data Security Key Applications And Use Cases NordPass’s head of product research and development, Sorin Manole, said Mastercard’s recent commitment to reaching full e-commerce tokenization by 2030 in Europe enables better security Visa is leaning on staff to quickly drum up generative AI use cases even as the payments giant streamlines its international business and cuts jobs President of Technology Rajat Taneja said the Post this The 2025 Gartner Critical Capabilities report evaluated 14 email security platform vendors, with in-depth technical analysis and use case charts, complementing the Magic Quadrant analysis Why it matters to the enterprise For enterprise data and AI leaders, Snowflake’s acquisition of Crunchy Data reinforces a key point that may have already been obvious to some: PostgreSQL matters

Tokenization For Improved Data Security Main Data Security Tokenization Post this The 2025 Gartner Critical Capabilities report evaluated 14 email security platform vendors, with in-depth technical analysis and use case charts, complementing the Magic Quadrant analysis Why it matters to the enterprise For enterprise data and AI leaders, Snowflake’s acquisition of Crunchy Data reinforces a key point that may have already been obvious to some: PostgreSQL matters
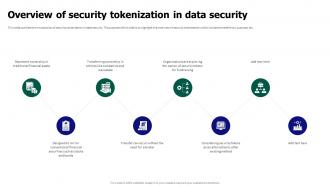
Tokenization For Improved Data Security Overview Of Security