Tryhackme Writeups Room Owasp Day03 Webapp Db At Master Pamhrituc Contribute to pamhrituc tryhackme writeups development by creating an account on github. This document delves into the owasp top 10 vulnerabilities, shedding light on their potential impact on system security. it covers a range of owasp topics, explaining the vulnerabilities, their causes, and how they can be exploited. participants in this room will engage in hands on challenges suitable for beginners without prior security knowledge.

Tryhackme Owasp Top 10 Walkthrough By Cybersec Ethical 50 Off Contribute to pamhrituc tryhackme writeups development by creating an account on github. From this point, i easily found the number of characters are in * etc passwd*",""," ",""," > 1611","","### day 10: insufficient logging & monitoring","","simply analyze the given [log file]( github pamhrituc tryhackme writeups blob master room owasp day10 login logs. This is a write up for the room owasptop 10 on tryhackme written 2023. this is meant for those that do not have their own virtual machines…. Answer webapp.db. it’s a file inside assets. now downloding the file and analyzing the file with file webapp.db command shows it’s a sqlite3 file. now, we can read the db file with sqlite3 webapp.db. if we use .table command to get table names, we will see there is two table named session and users.
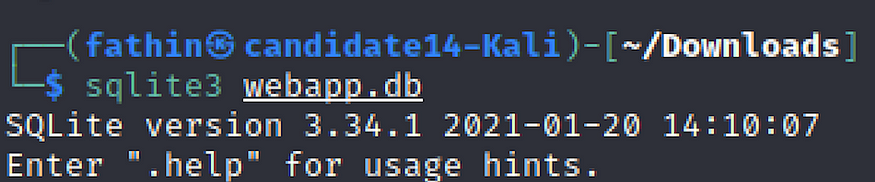
Owasp Top 10 Tryhackme Walkthrough This is a write up for the room owasptop 10 on tryhackme written 2023. this is meant for those that do not have their own virtual machines…. Answer webapp.db. it’s a file inside assets. now downloding the file and analyzing the file with file webapp.db command shows it’s a sqlite3 file. now, we can read the db file with sqlite3 webapp.db. if we use .table command to get table names, we will see there is two table named session and users. Tryhackme rooms guides. usefull when getting stuck or as reference material. Owasp top 10 this room contains info and exploits of top 10 owasp most critical vulnerabilities. for complete tryhackme path, refer the link task 3 [severity 1] injection injection is when user controlled input is interpreted as actual commands or parameters by the application.

Owasp Top 10 Tryhackme Walkthrough Tryhackme rooms guides. usefull when getting stuck or as reference material. Owasp top 10 this room contains info and exploits of top 10 owasp most critical vulnerabilities. for complete tryhackme path, refer the link task 3 [severity 1] injection injection is when user controlled input is interpreted as actual commands or parameters by the application.
Owasp Top 10 Tryhackme Walkthrough

Owasp Top 10 On Tryhackme The Dutch Hacker

Owasp Top 10 On Tryhackme The Dutch Hacker