
Cryptographic Hash Function Wikipedia Pdf Cryptography Password Wanting to learn what a cryptographic hashing function is? maybe you're wondering what exactly the math that is happening when someone mines for a bitcoin. well, in this video we explain how. Cryptographic hash functions are mathematical algorithms that transform input data into a fixed length sequence of characters, referred to as a hash value. cryptographic hash functions are intended to be fast, deterministic, and one way, meaning that even a minor change in input yields a very different hash. these functions are important for securing information digitally by allowing data.

Cryptographic Hash Function And Its Properties Pdf Cryptography Most cryptographic hash functions are designed to take a string of any length as input and produce a fixed length hash value. a cryptographic hash function must be able to withstand all known types of cryptanalytic attack. in theoretical cryptography, the security level of a cryptographic hash function has been defined using the following properties: pre image resistance given a hash value h. Cryptographic hash functions combine message passing capabilities needed in database security and cryptocurrency transactions. Dive into the world of cryptographic hash functions with this beginner friendly guide, unlocking their complexity and practical applications. Ssdeep is an example of a fuzzy hash function. before moving forward with the details of cryptographic hash functions, let us define the requirements mentioned above.

M 3 Cryptographic Hash Functions Pdf Public Key Cryptography Dive into the world of cryptographic hash functions with this beginner friendly guide, unlocking their complexity and practical applications. Ssdeep is an example of a fuzzy hash function. before moving forward with the details of cryptographic hash functions, let us define the requirements mentioned above. Discover the essentials of cryptographic hash functions, their role in digital security, and examples like 256 bit and sha 512 in cryptography. Learn about cryptography hash functions, their properties, and applications in data integrity and security. explore types of hash functions and their significance in cryptography.
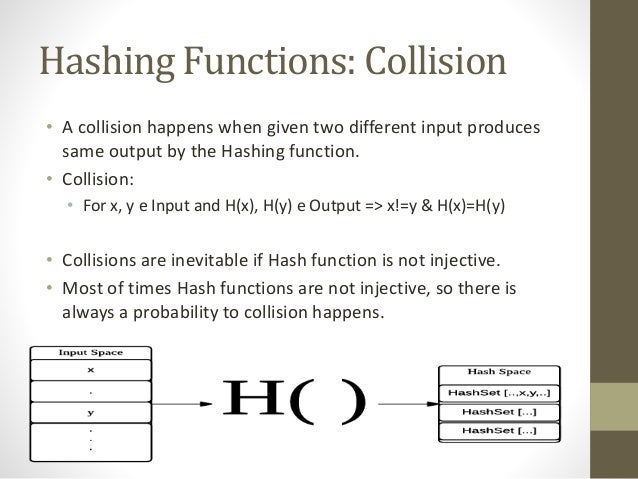
Cryptographic Hashing Functions Discover the essentials of cryptographic hash functions, their role in digital security, and examples like 256 bit and sha 512 in cryptography. Learn about cryptography hash functions, their properties, and applications in data integrity and security. explore types of hash functions and their significance in cryptography.

Cryptographic Hashing Functions