
An Overview Of The Security System Development Life Cycle Process For Ensuring secure software development life cycle (ssdlc) involves practical steps to integrate security effectively into the software development process. education and training: train the development team on security best practices to increase awareness and equip them with the skills needed to address potential security threats. Devsecops is the integration of security practices into every phase of the software development lifecycle. learn about devsecops in a multicloud environment.

Cybersecurity Best Practices Into Secure Software Development Devx The security development lifecycle (sdl) is a structured framework that integrates security best practices into every phase of software development. unlike traditional development processes that treat security as an afterthought, sdl ensures that security considerations are embedded from the start, reducing vulnerabilities and strengthening software resilience before deployment. Security measures should be integrated at multiple points into your existing software development lifecycle (sdlc) to ensure: design choices don't lead to security gaps. application code and configuration don't create vulnerabilities because of exploitable implementation and improper coding practices. software acquired via the supply chain doesn't introduce security threats. application code. Ssdlc is an approach to software design and development that embeds security considerations throughout the development process. referring generally to processes for producing secure software by design, ssdlc stresses the integration of security best practices into all phases of the sdlc – from requirements gathering and design to testing and. In today’s rapidly evolving digital landscape, integrating security into agile development processes has become a critical imperative rather than a mere afterthought. the traditional approach of addressing security concerns at the end of the development cycle creates vulnerabilities and leads to costly remediation efforts. by embedding security practices throughout the agile development.

Integrating Security Into The Software Development Lifecycle Ssdlc is an approach to software design and development that embeds security considerations throughout the development process. referring generally to processes for producing secure software by design, ssdlc stresses the integration of security best practices into all phases of the sdlc – from requirements gathering and design to testing and. In today’s rapidly evolving digital landscape, integrating security into agile development processes has become a critical imperative rather than a mere afterthought. the traditional approach of addressing security concerns at the end of the development cycle creates vulnerabilities and leads to costly remediation efforts. by embedding security practices throughout the agile development. Implementing secure sdl helps you follow security best practices, integrating security activities and checkups across the development cycle. this will help to increase your product and company security posture. Explore different software development life cycle (sdlc) models and learn how to integrate security into each model for better, secure development practices.
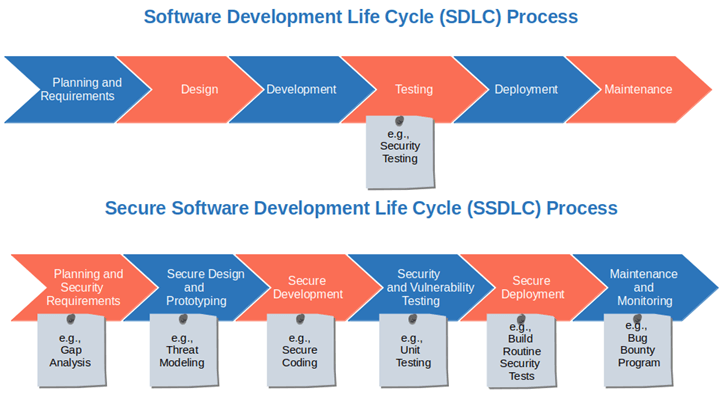
Secure Software Development Building Security Into Your Software Implementing secure sdl helps you follow security best practices, integrating security activities and checkups across the development cycle. this will help to increase your product and company security posture. Explore different software development life cycle (sdlc) models and learn how to integrate security into each model for better, secure development practices.

Pdf Integrating Security Into The Software Development Lifecycle

Devsecops Integrating Security Into Development Lifecycle

Building Security Into The Software Development Lifecycle Best